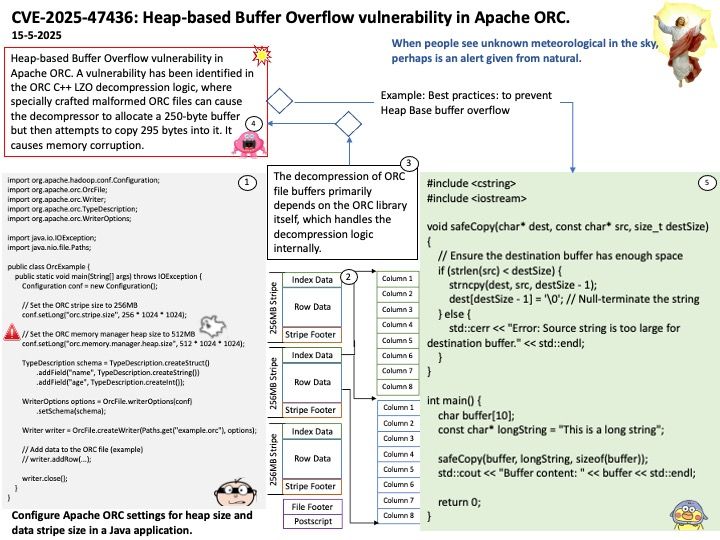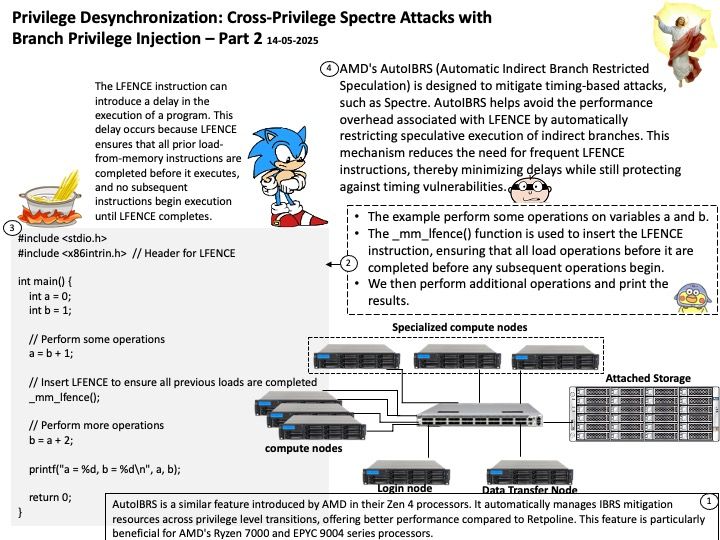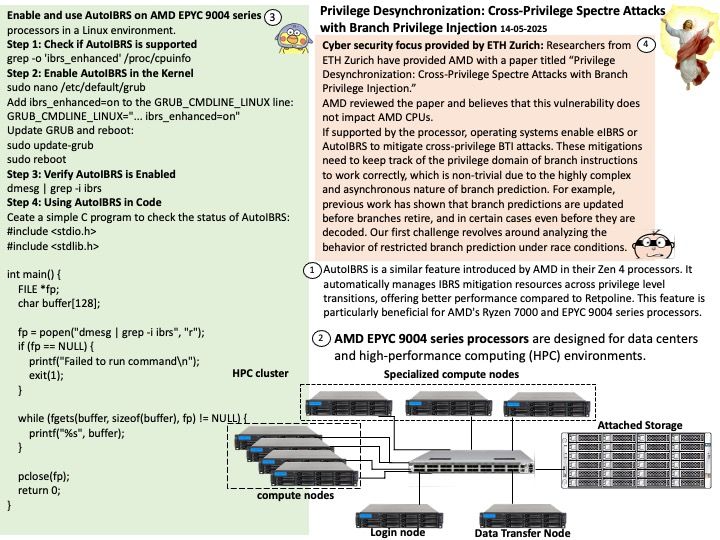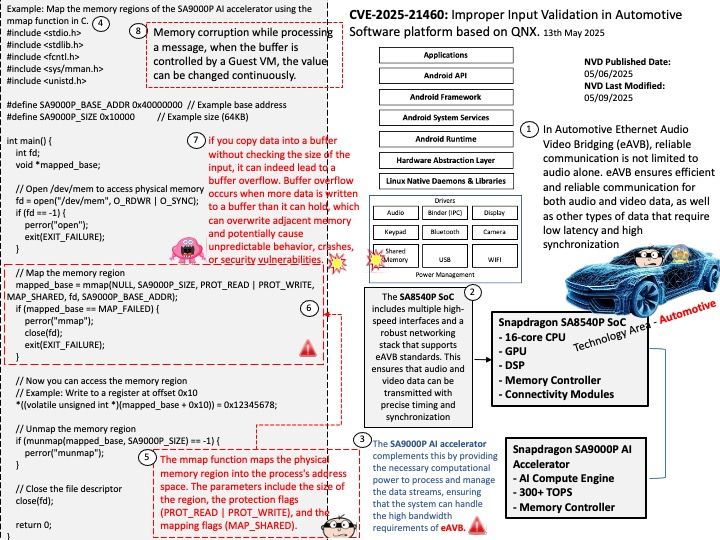
Preface: Hertzbleedis about inferring secrets from timing differencescaused by how CPUs adjust their frequency under load.
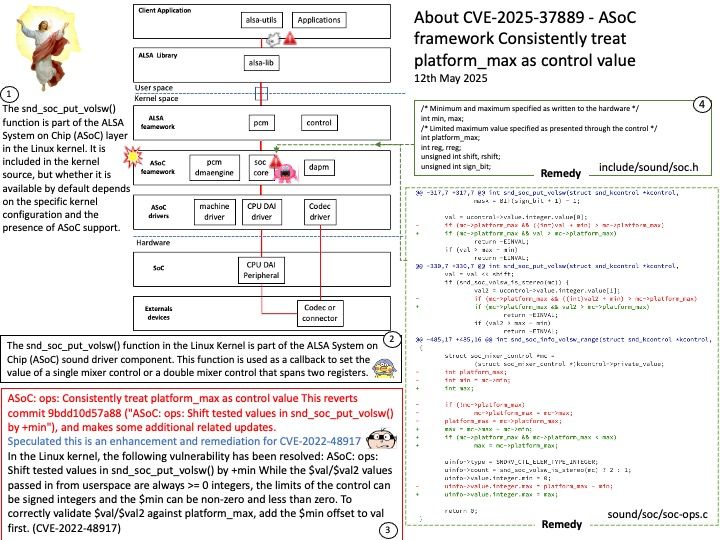
Background: The Hertzbleed vulnerability does not specifically target the L2 cache of AMD CPUs. Instead, it exploits a broader mechanism related to dynamic frequency scaling — a feature used by modern CPUs (including AMD Zen 2 and Zen 3) to adjust clock speeds based on workload and thermal conditions.
How is IOLeak Different?
| Feature | Hertzbleed | IOLeak |
| Primary Trigger | Data-dependent CPU workload | I/O latency and interaction with CPU |
| Leakage Source | Frequency scaling due to computation | Frequency scaling influenced by I/O timing |
| Focus | Cryptographic operations (e.g., SIKE) | Broader I/O-related operations |
| Novelty | First to show DVFS can leak data remotely | First to show I/O latency can amplify DVFS-based leakage |
Ref: AMD’s DVFS (Dynamic Voltage and Frequency Scaling) is a power management technique that dynamically adjusts the CPU’s voltage and frequency based on the current workload. This allows for a balance between performance and energy consumption by reducing both when the workload is light and boosting them when more processing power is needed. DVFS is used in AMD processors to optimize power usage and improve battery life in mobile devices, as well as to reduce energy costs in servers.
Vulnerability details: The researchers provided AMD with a summary of their comments and findings, detailed in a paper titled “IOLeak Side-Channel Attacks Exploiting CPU Frequency Scaling and I/O Latency.”
AMD reviewed the summary and believes this attack is similar to previously disclosed side-channel attacks such as “Hertzbleed” and that existing mitigation recommendations for such attacks remain applicable to mitigate the techniques described in the researchers’ summary.
Official announcement: Please see the link for details – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7042.html