Originally posted by AMD 3rd Feb 2025
2025-02-17 – Updated Acknowledgement
2025-06-03 Update:A subsequent report of the same attacks was received from researchers at Graz University of Technology.
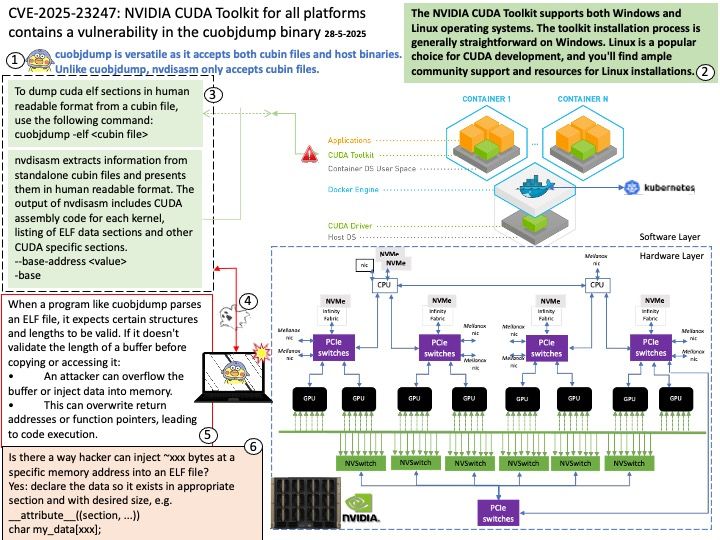
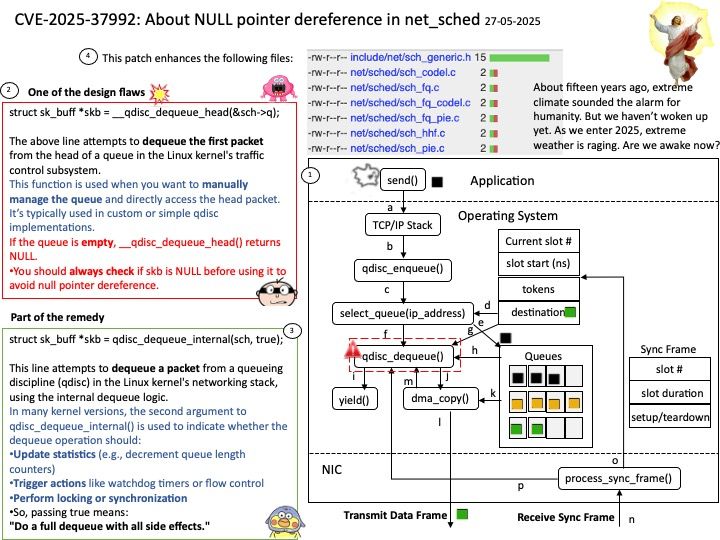
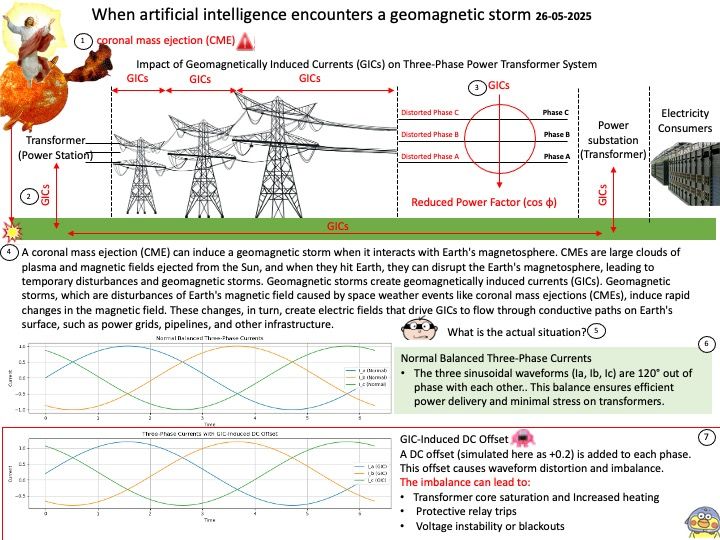
Preface: FIPS 186-5 removes DSA as an approved digital signature algorithm “due to a lack of use by industry and based on academic analyses that observed that implementations of DSA may be vulnerable to attacks if domain parameters are not properly generated.
February 3, 2023 – NIST published Federal Information Processing Standard (FIPS) 186-5, Digital Signature Standard (DSS), along with NIST Special Publication (SP) 800-186, Recommendations for Discrete Logarithm-based Cryptography: Elliptic Curve Domain Parameters.
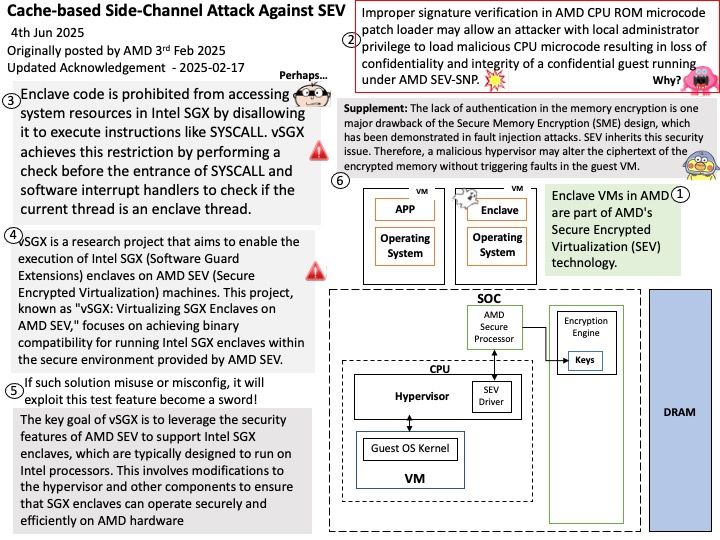
Background: The SEV feature relies on elliptic-curve cryptography for its secure key generation, which runs when a VM is launched. The VM initiates the elliptic-curve algorithm by providing points along its NIST (National Institute of Standards and Technology) curve and relaying the data based on the private key of the machine.
Vulnerability details: AMD has received a report from researchers at National Taiwan University detailing cache-based side-channel attacks against Secure Encrypted Virtualization (SEV).
Remedy: AMD recommends software developers employ existing best practices for prime and probe attacks (including constant-time algorithms) and avoid secret-dependent data accesses where appropriate. AMD also recommends following previously published guidance regarding Spectre type attacks (refer to the link in the reference section below), as it believes the previous guidance remains applicable to mitigate these vulnerabilities.
Supplement: The lack of authentication in the memory encryption is one major drawback of the Secure Memory Encryption (SME) design, which has been demonstrated in fault injection attacks. SEV inherits this security issue. Therefore, a malicious hypervisor may alter the ciphertext of the encrypted memory without triggering faults in the guest VM.
Office announcement: Please refer to the link for details –
https://www.amd.com/en/resources/product-security/bulletin/amd-sb-3010.html