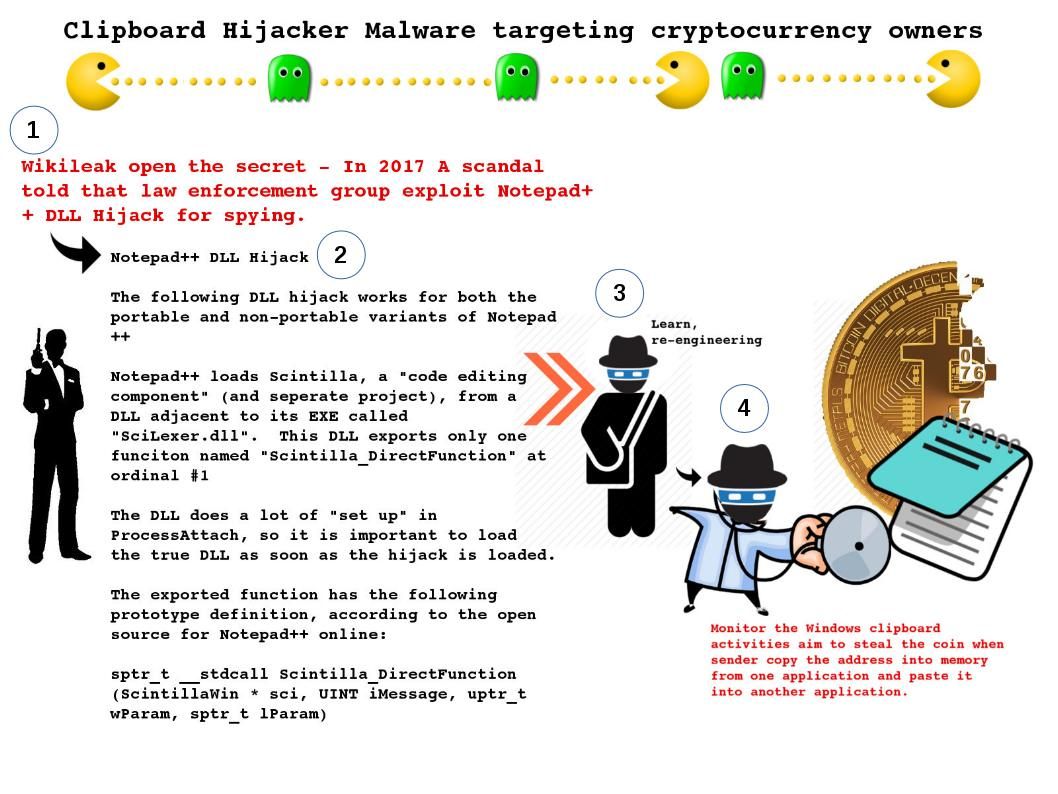
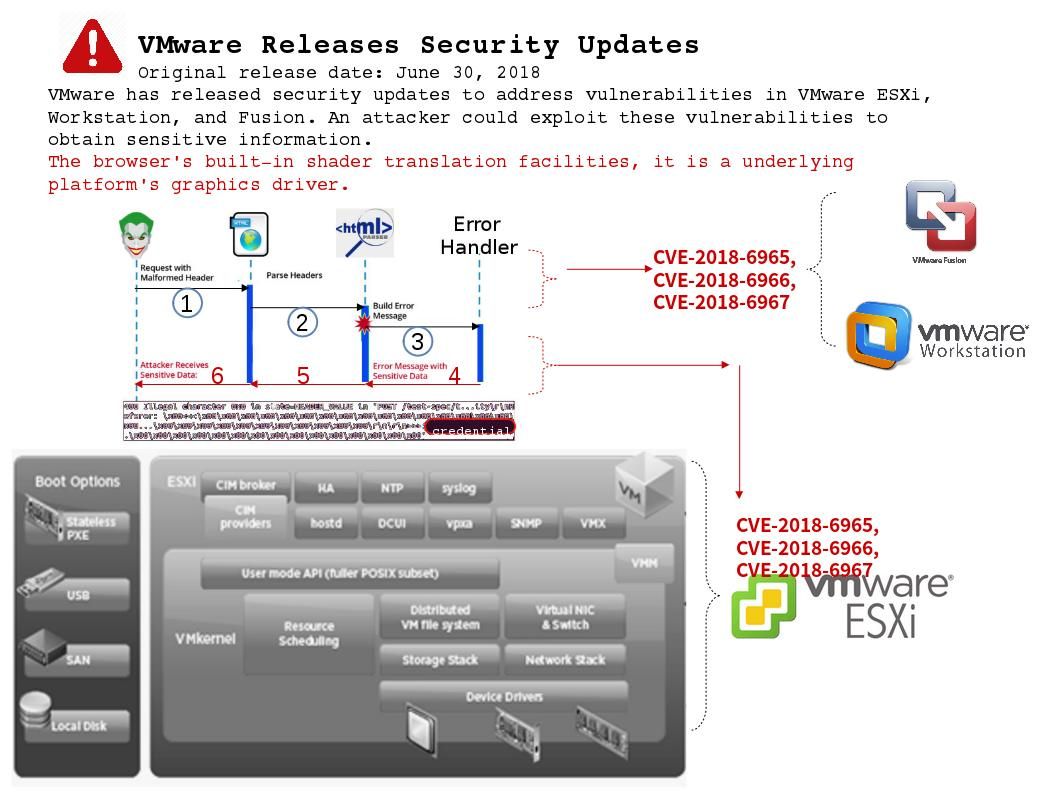
As time goes by node.js and MYSQL database become another technology trend in IT world. Before Node.js, Javascript was only used for client-side development. It was necessary to use a different server-side programming language. Nowadays web applications deploy Javascript, making app deployment much easier and more efficient.
But web application developer must staying alert. However a vulnerability was found. The Node.js third-party module query-mysql versions 0.0.0, 0.0.1, and 0.0.2 are vulnerable to an SQL injection vulnerability due to lack of user input sanitization. This may allow an attacker to run arbitrary SQL queries when fetching data from database.
Should you have interested, please see below: