Preface
NSA’s backdoor catalog (OS system and Network) exposed:
In conspiracy theory point of view, what is the reason for operation system vendor maintain SMB version 1 until NSA scandal exposed to the world then take the patching action. Perhaps if not WannaCry ransomware attack outbreak tarnished SMB 1 design limitation. Meanwhile hacker claimed that they are appreciate for NSA found this secret! Since nobody aware this issue until secret leak to the world! But who know what is the true factor let OS vendor delay SMB version 1 patching schedule till incident happen afterwards? (Microsoft released patches for all supported versions of Windows on the March 2017).
Conspiracy theory point of view on Network system ( merely personal opinion )
Based on the Shadow Brokers disclosed. The two exploits, listed in the archive directory as EPICBANANA and EXTRABACON, can be used to achieve remote code execution on Cisco firewall products. A vulnerability exploited by one of the tools was patched in 2011 but the other exploit’s vulnerability is entirely new. From logical point of view, it is hard to imagine that such big technology company did not know the design weakness of their product? Maybe they are trustworthy. Or Who know, God know?
Who dare say there is no unknown backdoor in hardware unit including CPU
Information Update on 31st Aug 2017 – Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability Escalation of Privilege
Headline news today report that CPU vendor design computer according the requirement by customer , sometimes the client is a government. For instance, US government might compliance to their security standard (High Assurance Platform program so called HAP). However a design limitation was found. An official announcement by Intel in regards to this vulnerabilities on May 2017. Furthermore security experts found a unknown backdoor on Intel ME Chip. From technical point of view, this is not coincidence and speculated that both vulnerabilities has relationship.
From safety view point, it is impossible to use hostile national science and technology products
In defense and protective prospective, it was not possible to use hostile national science and technology products in military zone. Even though the hardware and operation system vendor are trustworthy. However the hostile country will try different to implant malware or infiltrate techniques to related system. For instance, Network equipment vendor (router, switch and firewall) do not know the design weakness will trigger such critical level of destructive result. Below is a simple example to proof this concept.
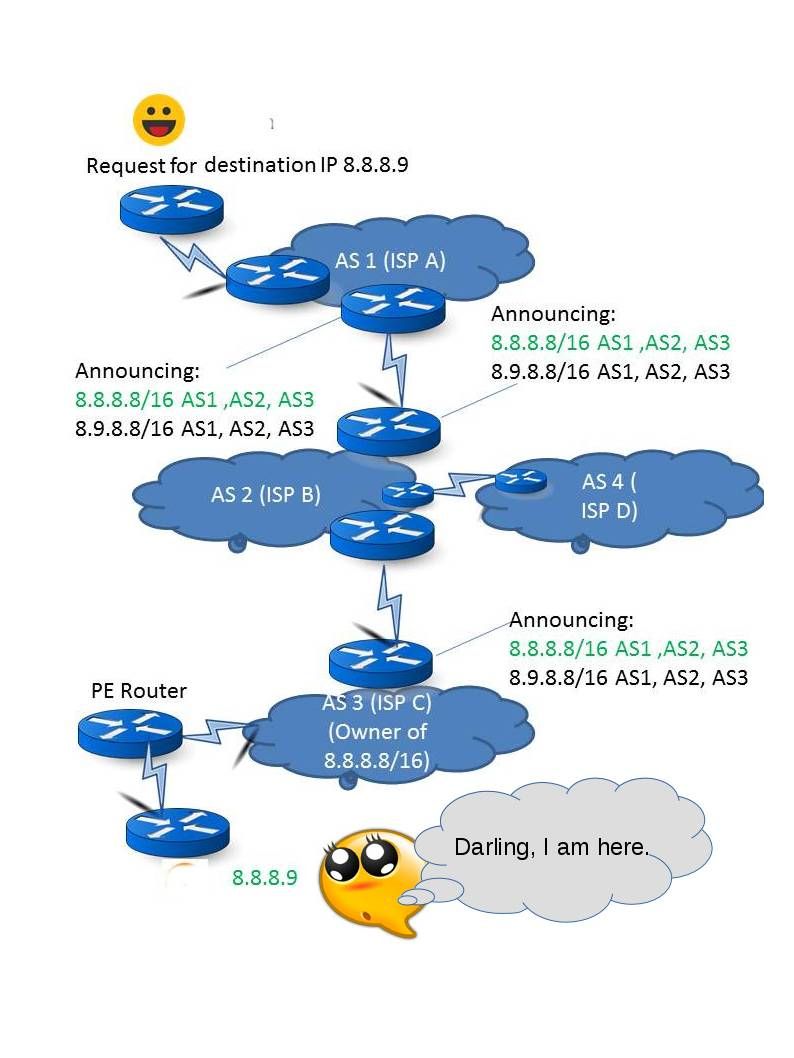
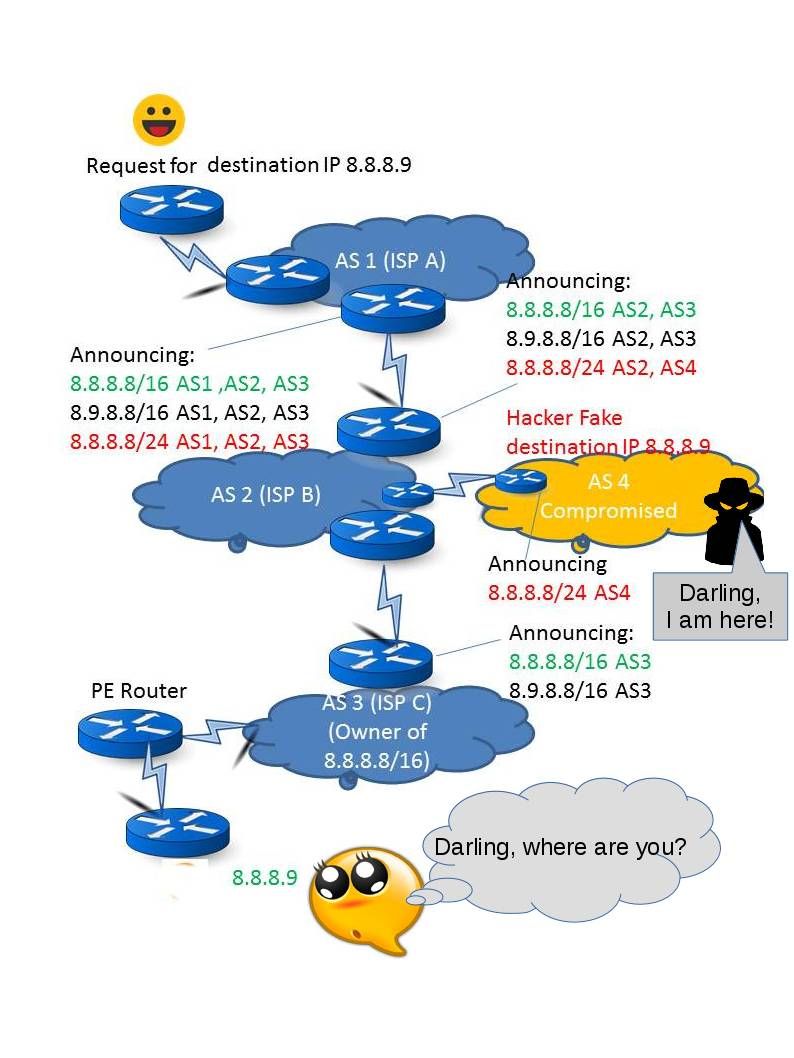
Picture A is the reference of normal network operating scenario. We understand that internet world coexists with BGP network protocols. The zoning driven by AS number (autonomous system number). The AS Using BGP to Distribute Routes. For instance, on picture B. The ISP D network equipment hits SNMP design flaw and encountered core OS buffer overflow causes privileges escalation. As a result the core router has been compromised. Base on BGP protocol hijack concept, the compromised router might obfuscate the network. It might have way to control the network routing path. I am not going to explain into details since it is a very long discussion. However if you base on above techincal terms and concept do a google search. You will be able to find the details. Yes, internet world is the big data. It is free.
Put above concept to the realistic world
Since above example is my imagination, however it will bring a solid idea to you. How serious level of destruction will be occurs in similar circumstances. So to protect yourself in cyber war battle seems better do not let your enemy know what type of equipment you are in use. Even though they are using CVE attack or Zero day attack. You equipment will be ignore those kind of cyber attack.
The focus of the discussion
I can’t written down a term of summary or conclusion right now. Since there are more and more information coming. However I need to study the details before continues this discussion. Ok, have a nice weekend. We discuss next time, Thank you! Bye!
Picture A – Normal scenario (request to reach adjacent side IP address)
Picture B – Telecommunication service provider network equipment compromised by hostile national.(As a result, the network traffic will route to their area and under their control)
Electronic War reference:

I Will keep this for later.
Please let me know if you’re looking for a article writer for your site. You have some really good articles and I think I would be a good asset. If you ever want to take some of the load off, I’d love to write some articles for your blog in exchange for a link back to mine. Please blast me an email if interested. Thanks!