Preface: The world’s first web-speed, internet-scale public blockchain. At the virtual event launching Sodium on September 30, 2022, the DFINITY Foundation will launch the Network Nervous System, an open algorithmic governance system that controlling the Internet computer. The event will also showcase in-depth technical material on advanced cryptography, consensus protocols, and token economics.
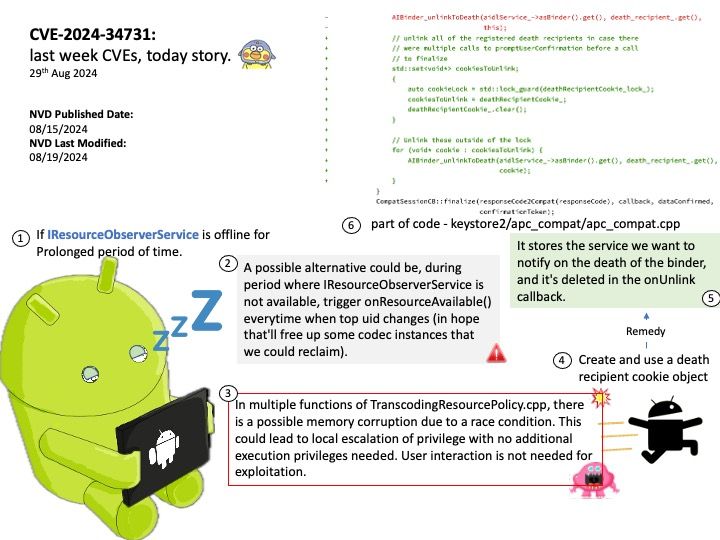
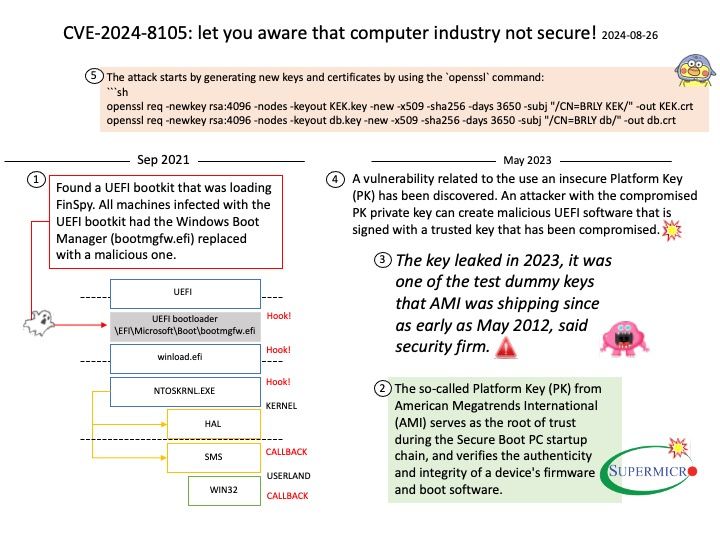
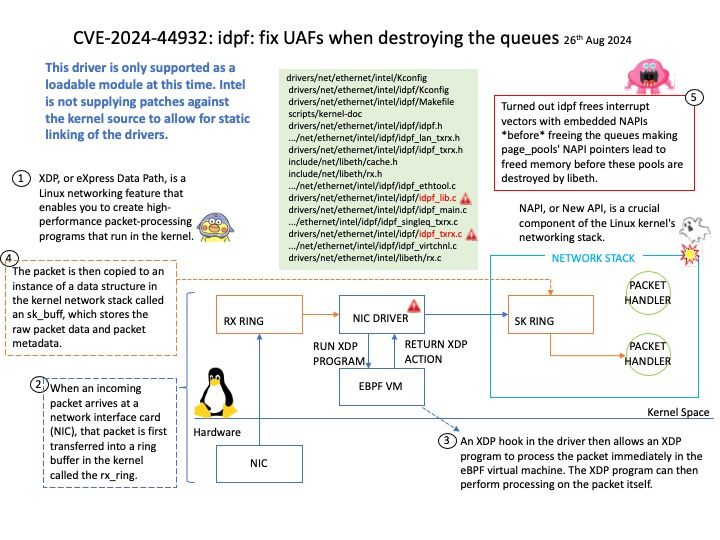
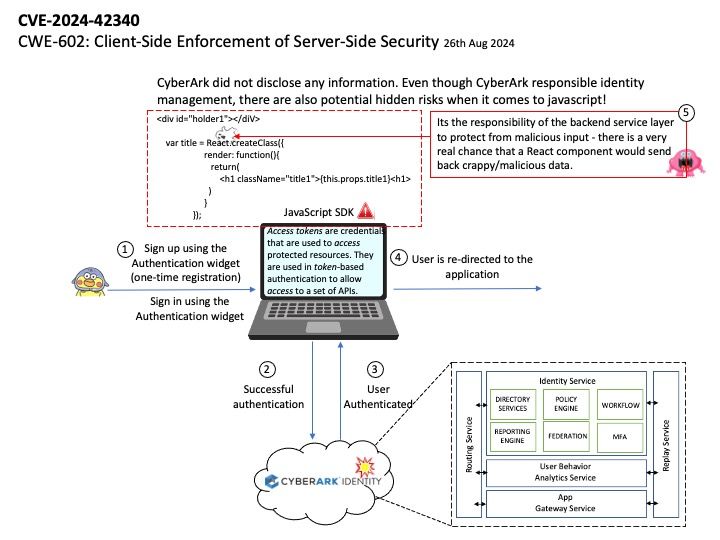
Background: Inter–canister calls can be used to update information between two or more canisters.
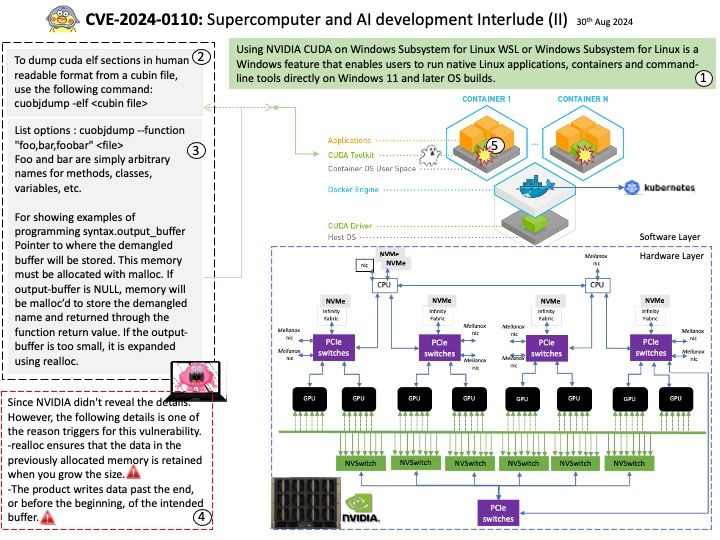
ic-cdk : Inter-canister calls for the ICRC-1 ledger.
ledger-icrc-js : A library for interfacing with ICRC-1 ledger on the Internet Computer.
When you deploy the WebAssembly module that contains your program on the Internet Computer blockchain, the program is executed inside a conceptual computational unit called a canister. Canisters can be developed in various programming languages.
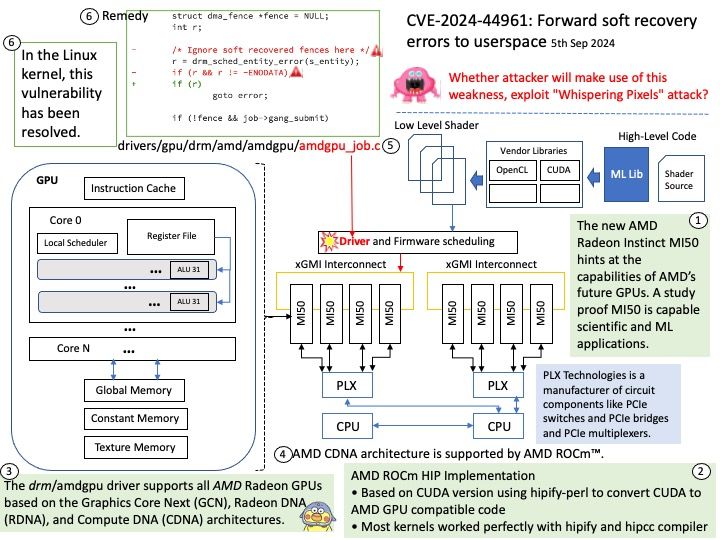
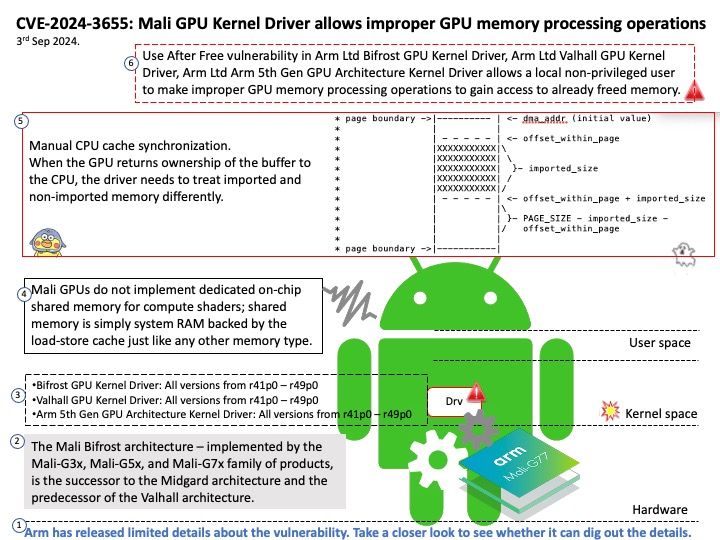
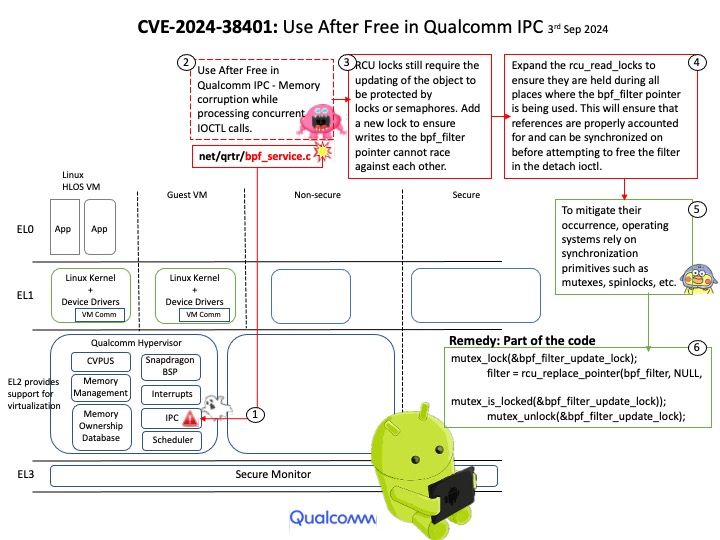
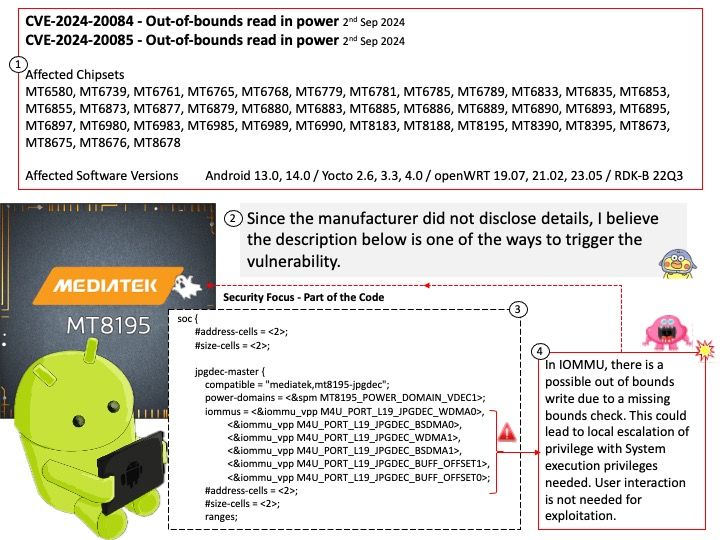
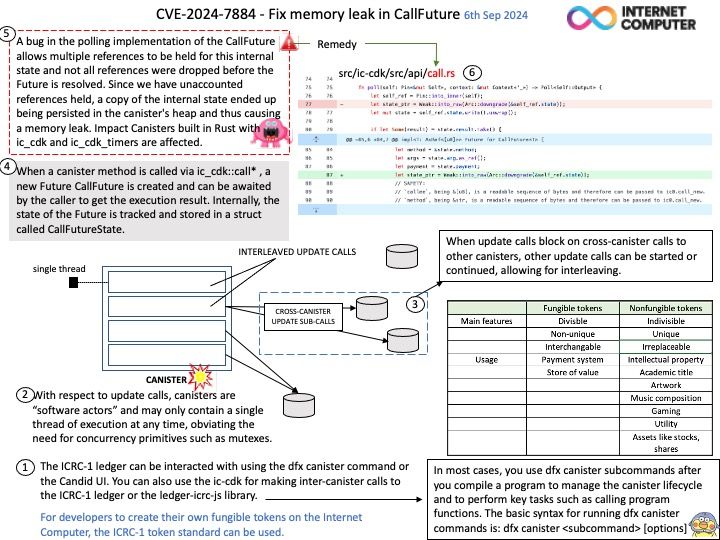
With respect to update calls, canisters are “software actors” and may only contain a single thread of execution at any time, obviating the need for concurrency primitives such as mutexes. However, when update calls block on cross-canister calls to other canisters, other update calls can be started or continued, allowing for interleaving.
Ref: In most cases, you use dfx canister subcommands after you compile a program to manage the canister lifecycle and to perform key tasks such as calling program functions. The basic syntax for running dfx canister commands is: dfx canister <subcommand> [options]
Vulnerability details: When a canister method is called via ic_cdk::call* , a new Future CallFuture is created and can be awaited by the caller to get the execution result. Internally, the state of the Future is tracked and stored in a struct called CallFutureState. A bug in the polling implementation of the CallFuture allows multiple references to be held for this internal state and not all references were dropped before the Future is resolved. Since we have unaccounted references held, a copy of the internal state ended up being persisted in the canister’s heap and thus causing a memory leak. Impact Canisters built in Rust with ic_cdk and ic_cdk_timers are affected. If these canisters call a canister method, use timers or heartbeat, they will likely leak a small amount of memory on every such operation. In the worst case, this could lead to heap memory exhaustion triggered by an attacker.
Official announcement: Please refer to the link for details – https://www.tenable.com/cve/CVE-2024-7884