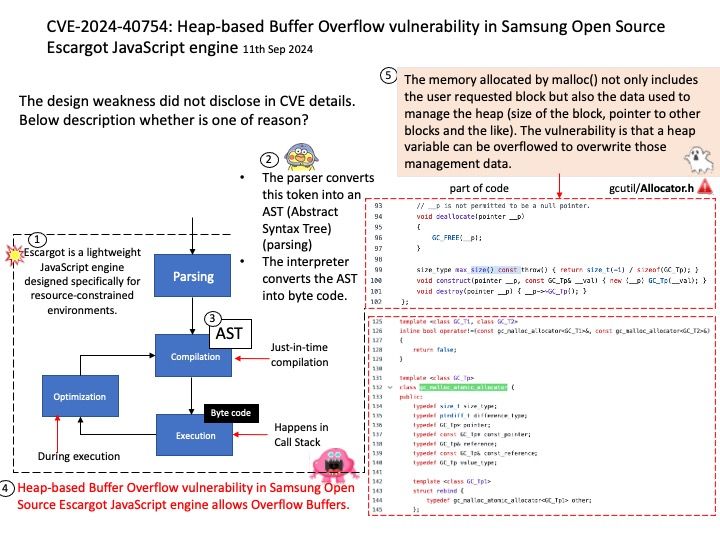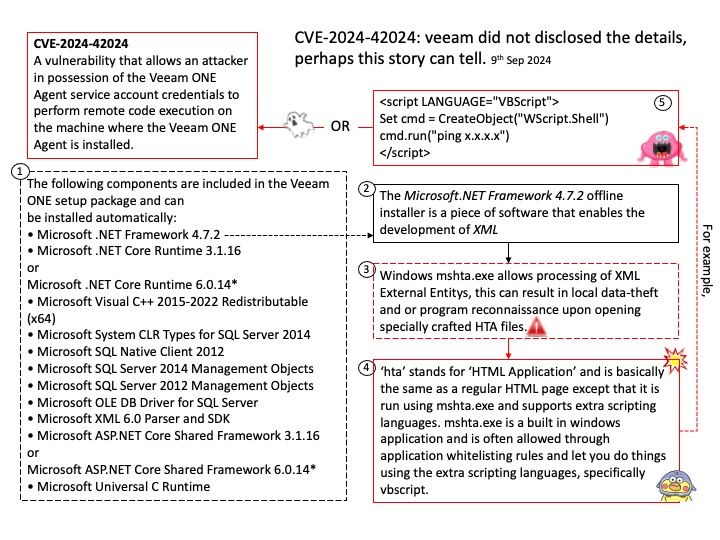
Preface: When you got a valid non-NULL pointer to a memory address returned by malloc(), only the requested size of memory is allocated to your process and you’re allowed to use (read and / or write) into that much space only.
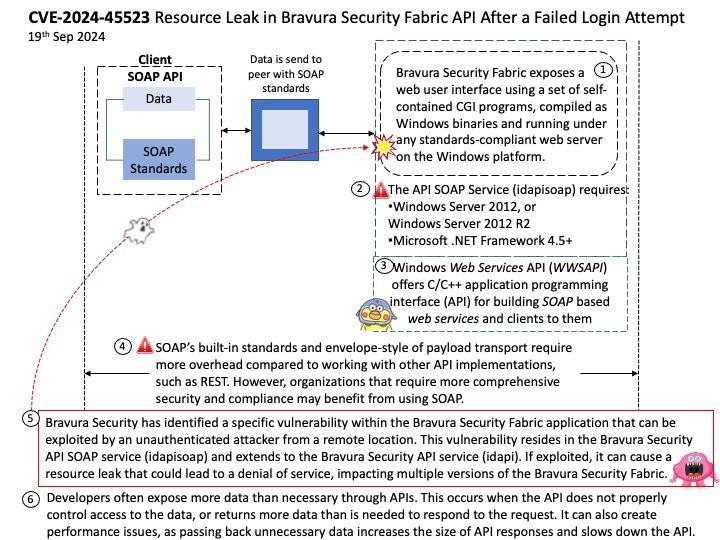
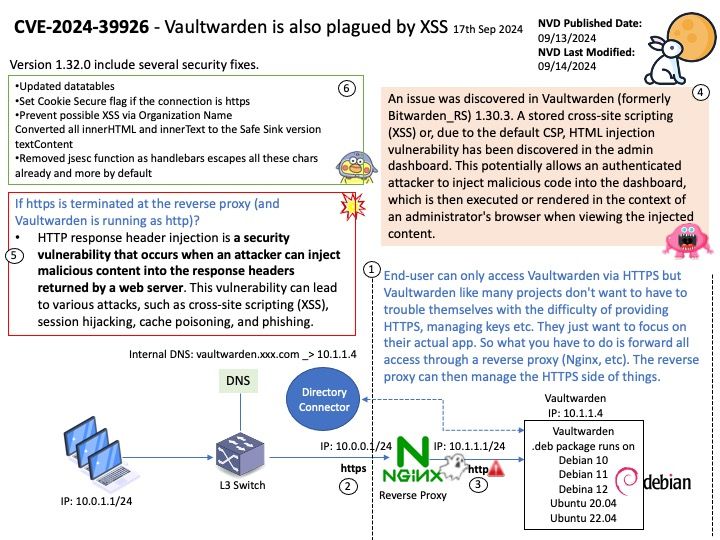
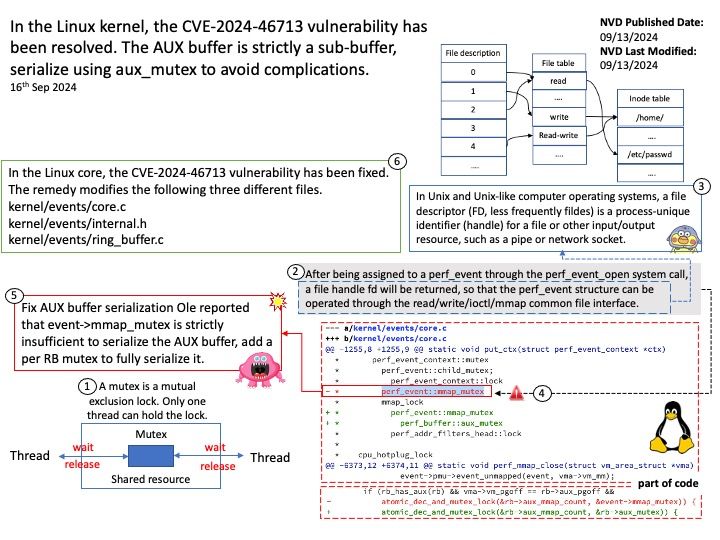
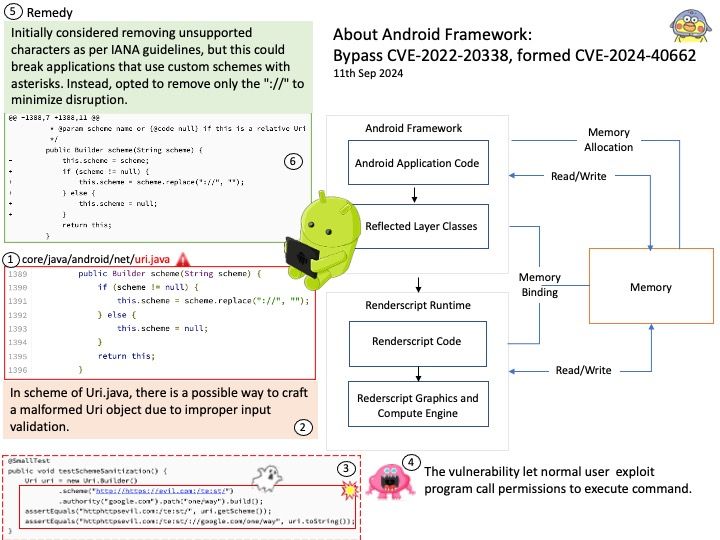
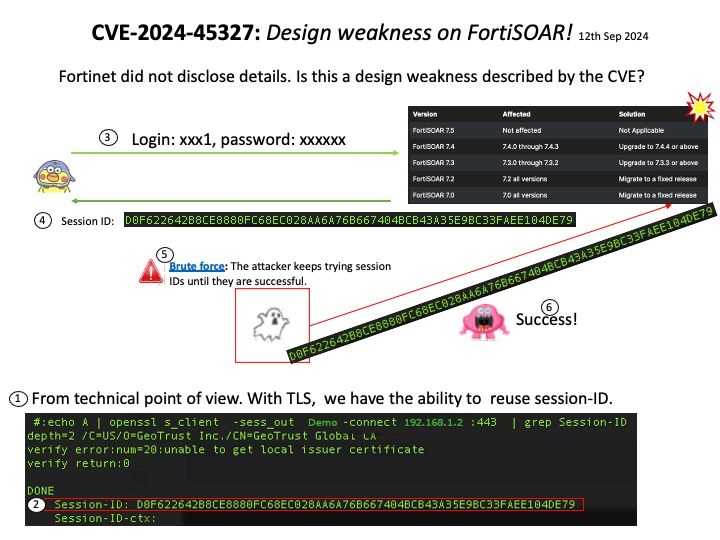
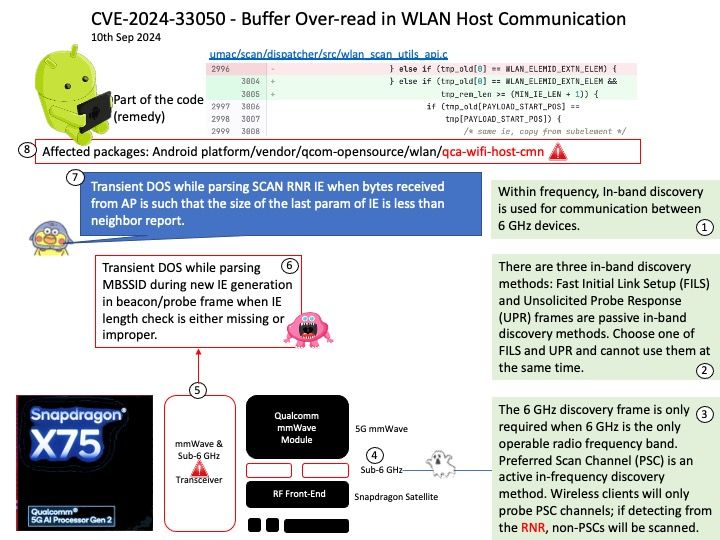
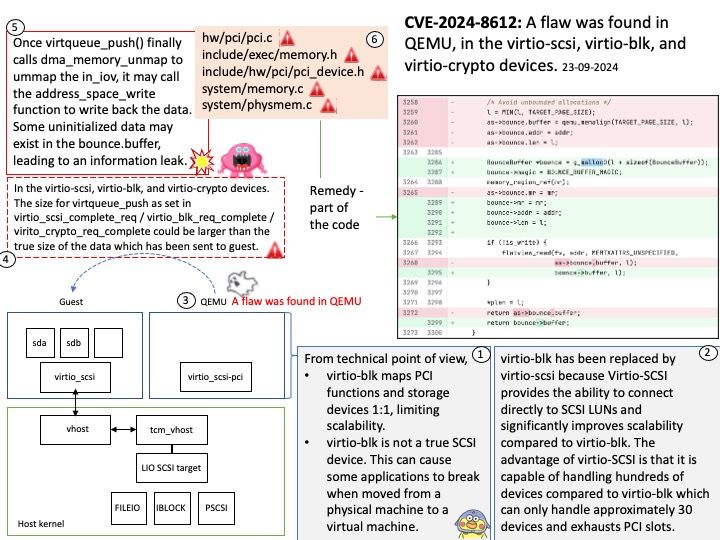
Background: When you launch a KVM-based guest, most often you would see QEMU doing the major user space heavy-lifting by providing a PC-like environment—it handles guest memory management, network cards, emulated storage devices, and so forth.
When using QEMU, all I/O travels through a single queue, which can affect performance.
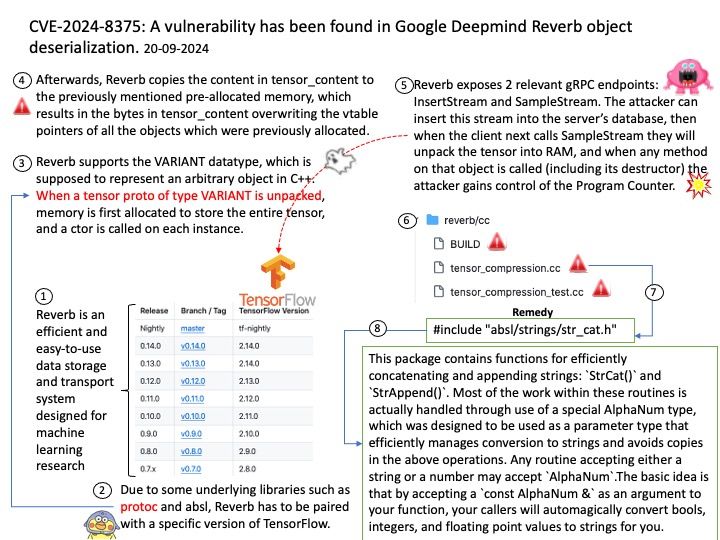
Vulnerability details: In the virtio-scsi, virtio-blk, and virtio-crypto devices. The size for virtqueue_push as set in virtio_scsi_complete_req / virtio_blk_req_complete / virito_crypto_req_complete could be larger than the true size of the data which has been sent to guest.
Once virtqueue_push() finally calls dma_memory_unmap to ummap the in_iov, it may call the address_space_write function to write back the data. Some uninitialized data may exist in the bounce.buffer, leading to an information leak
Ref: A bounce buffer resides in memory low enough for a device to copy from and write data to. It is then copied to the desired user page in high memory. This additional copy is undesirable, but unavoidable. Pages are allocated in low memory which are used as buffer pages for DMA to and from the device.
This CVE only low risk vulnerability. However, but should staying alert.
Official announcement: Please refer to the vendor announcement for details – https://nvd.nist.gov/vuln/detail/CVE-2024-8612