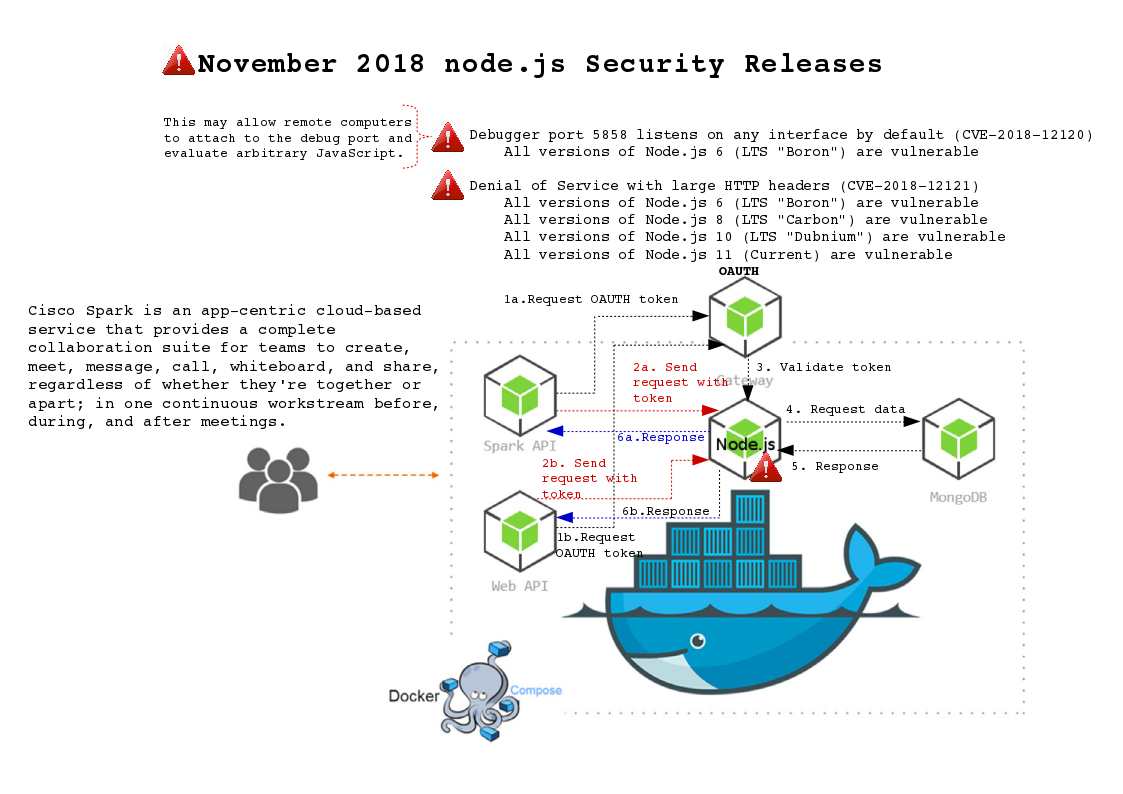
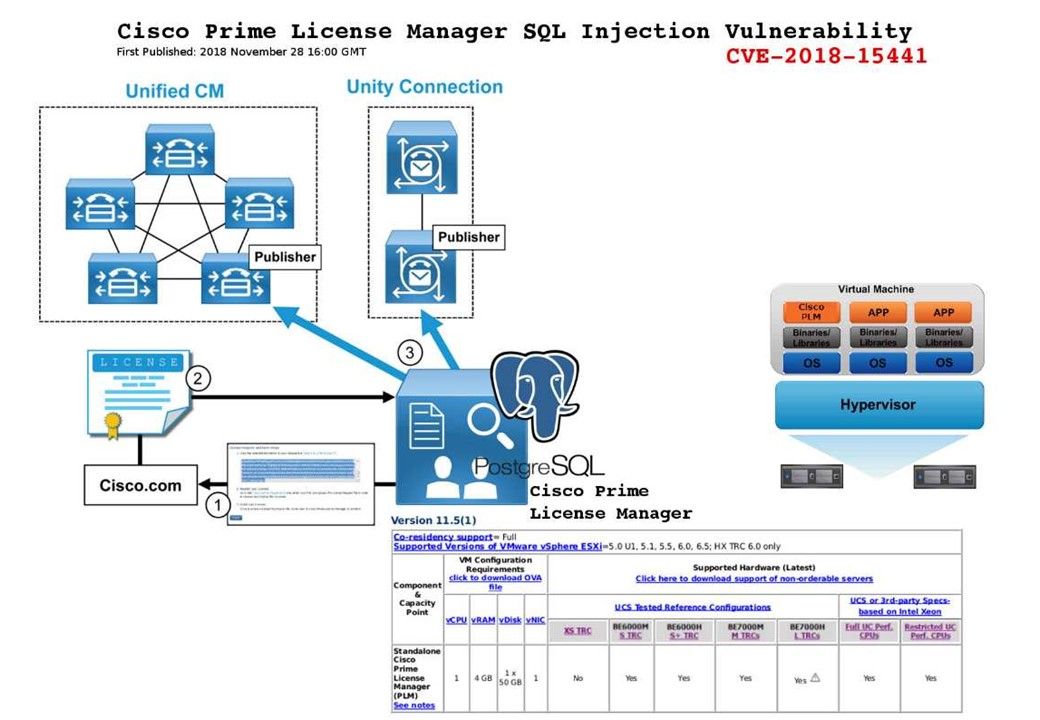
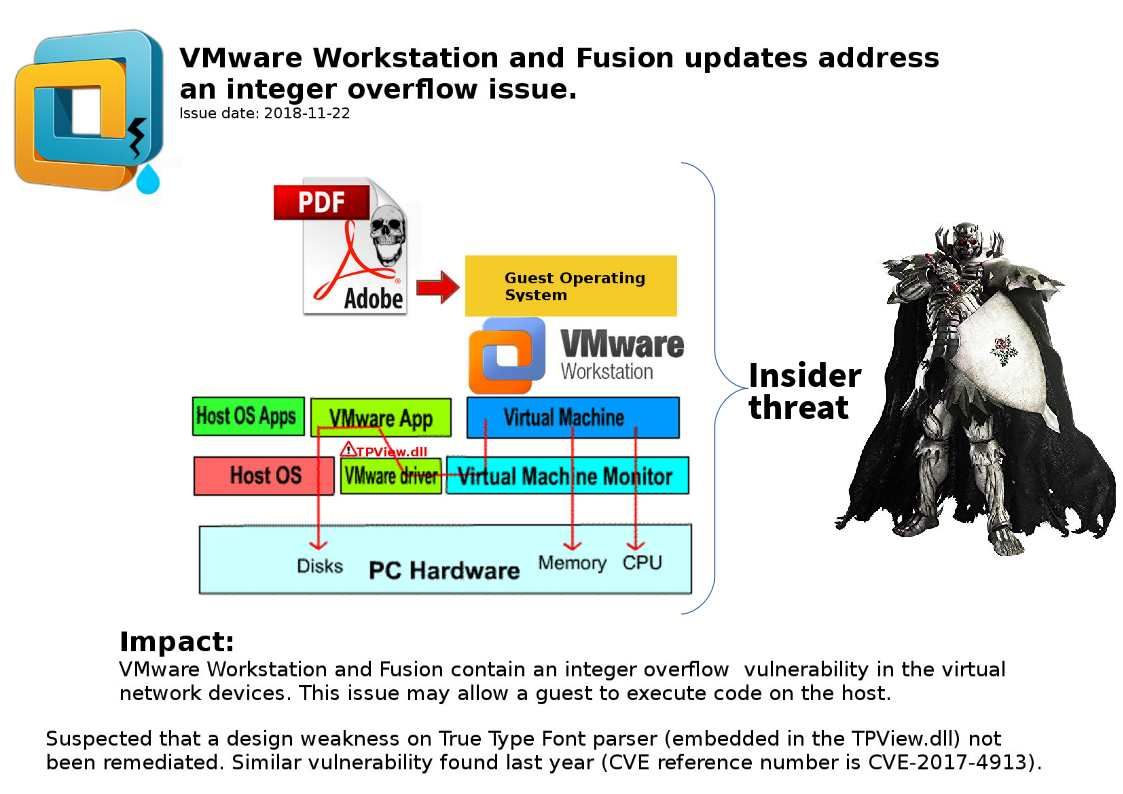
Preface:
NVIDIA GeForce graphics cards are built for the ultimate PC gaming experience, delivering amazing performance, immersive VR gaming, and high-res graphics.
Technical background:
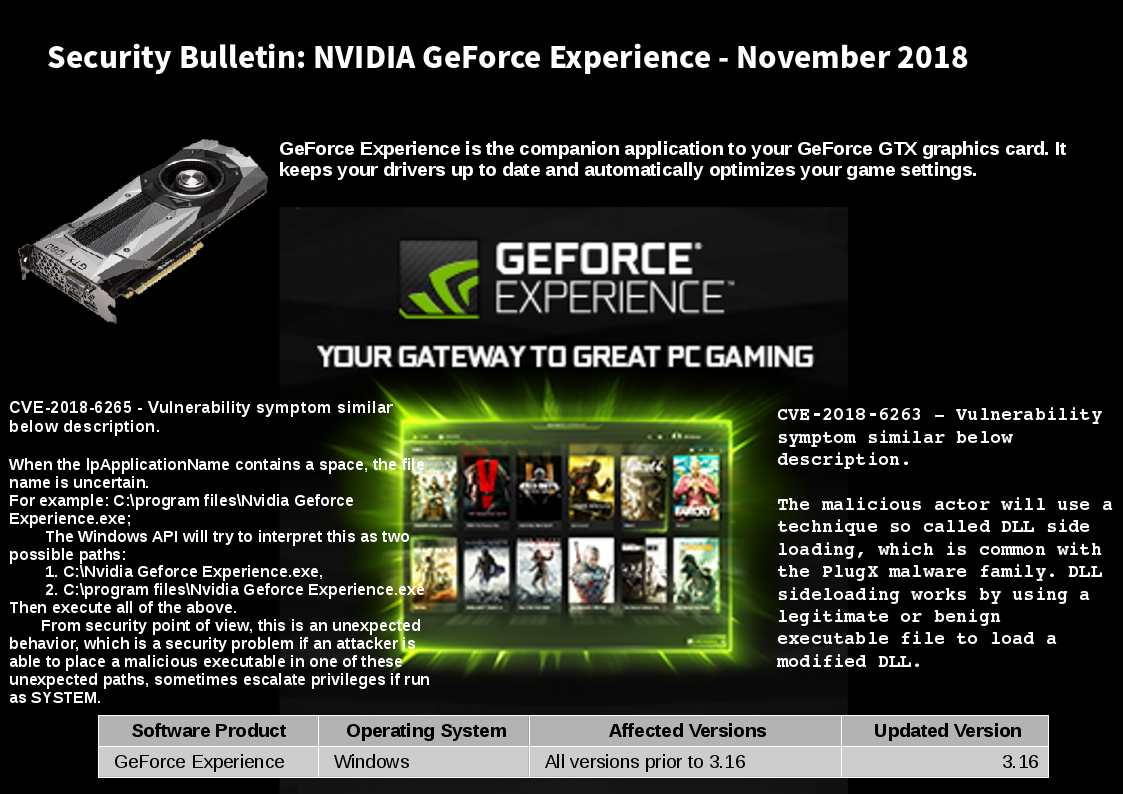
GeForce Experience is the companion application to your GeForce GTX graphics card. It keeps your drivers up to date and automatically optimizes your game settings.
Vulnerability details announced on Nov 2018:
https://nvidia.custhelp.com/app/answers/detail/a_id/4740
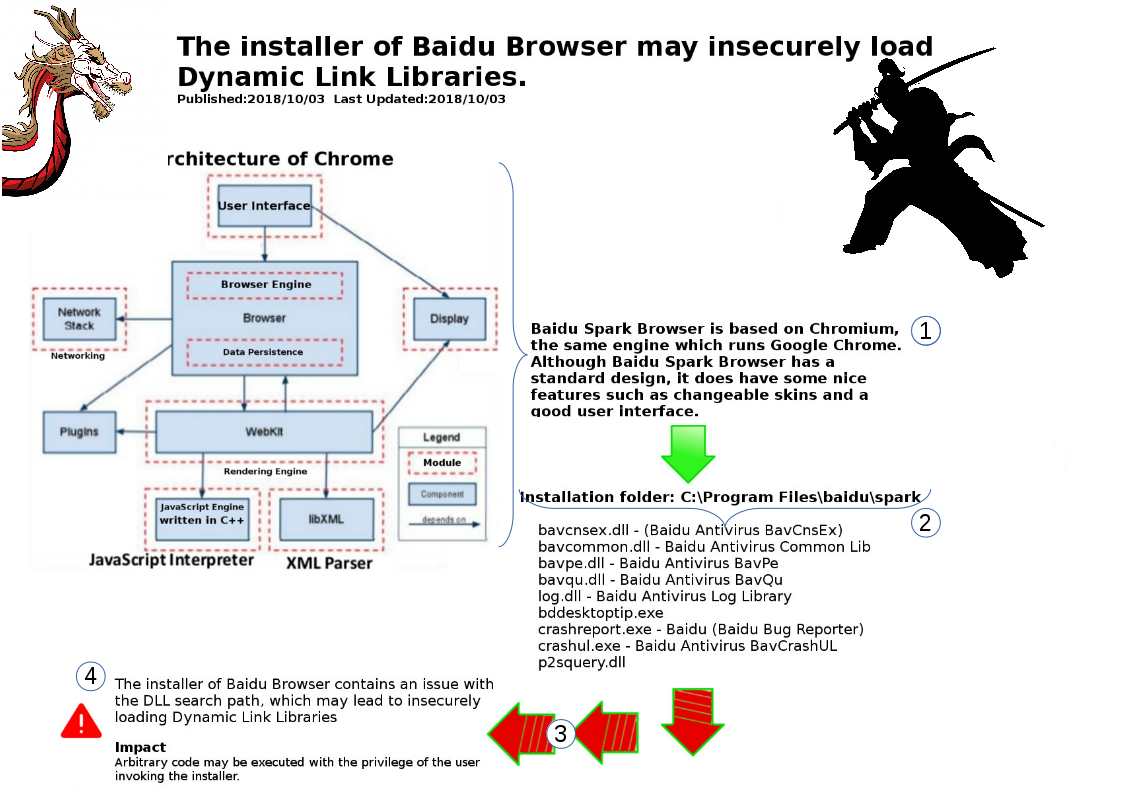
CVE‑2018‑6263 – NVIDIA GeForce Experience contains a vulnerability in all versions prior to 3.16 on Windows in which an attacker who has access to a local user account can plant a malicious dynamic link library (DLL) during application installation, which may lead to escalation of privileges.
CVE‑2018‑6265 – NVIDIA GeForce Experience contains a vulnerability in all versions prior to 3.16 during application installation on Windows 7 in elevated privilege mode, where a local user who initiates a browser session may obtain escalation of privileges on the browser.
For more details, please refer to attached diagram.