Preface: Python provides the essential programming language for smart devices and solutions for the Internet of Things and Industry 4.0.
Technical background: When you use AES128 encrypt string, if the encrypted string is too long. It will contain \r\n in it. Actually, the encryption output is an array of 8-bit bytes, not characters.
The code is Base64 encoding the encrypted data with an option to insert line breaks every 64 characters.
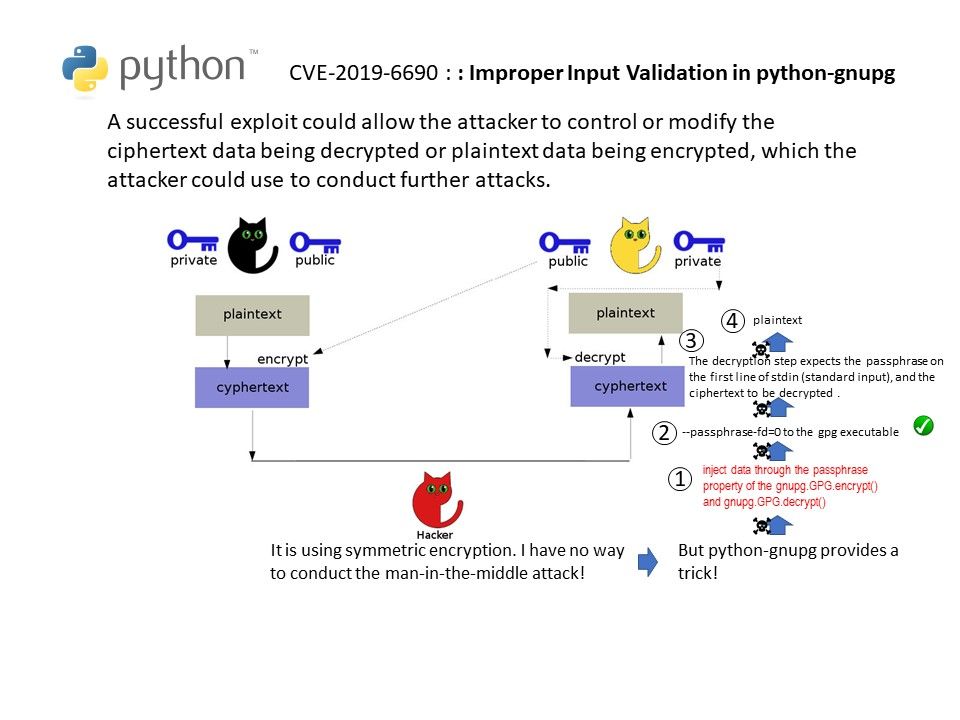
About python-gnupg: gnupg module enables Python to use the functionality of GNU Privacy Guard or GnuPG. With this module Python programs can create and managed keys, encrpt and decrypt data, sign and verify.
Vulnerability detail: A design weakness due to insufficient validation of user-supplied input submitted to the passphrase property of the gnupg.GPG.encrypt() and gnupg.GPG.decrypt() methods when symmetric encryption is used. Such vulnerability could allow a local attacker to control or modify sensitive information on a targeted system.
Remedy: Added checks to disallow newline-type characters in passphrases. https://github.com/vsajip/python-gnupg/commit/39eca266dd837e2ad89c94eb17b7a6f50b25e7cf#diff-88b99bb28683bd5b7e3a204826ead112