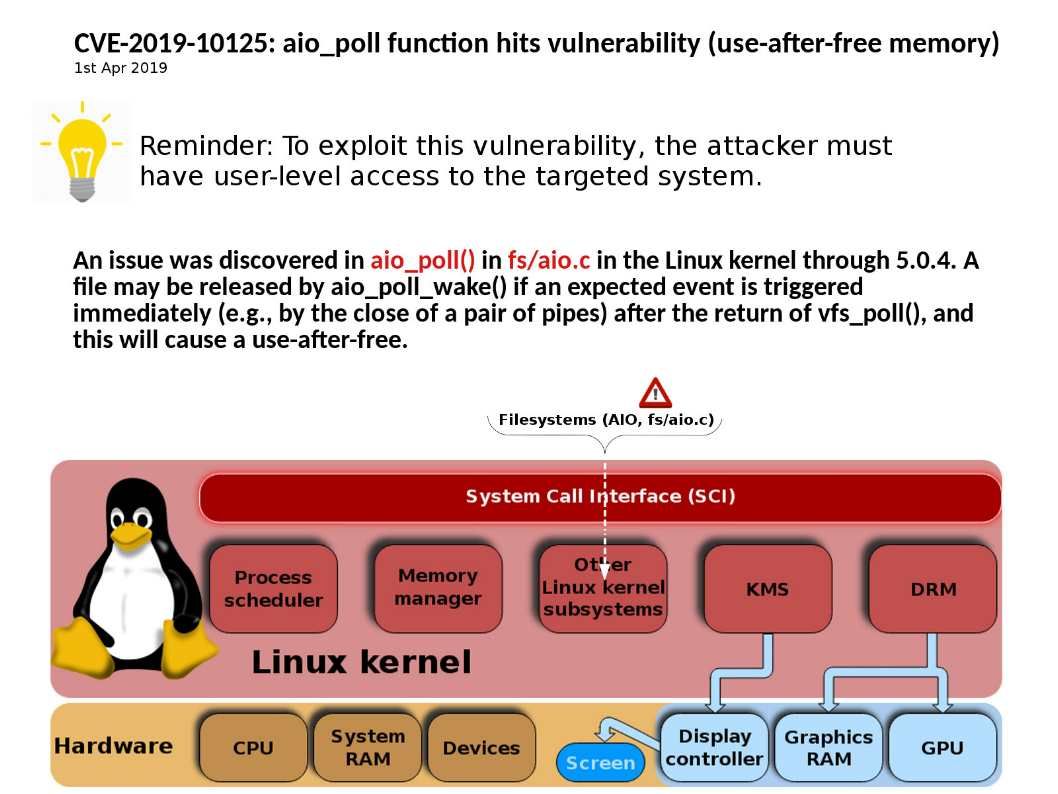
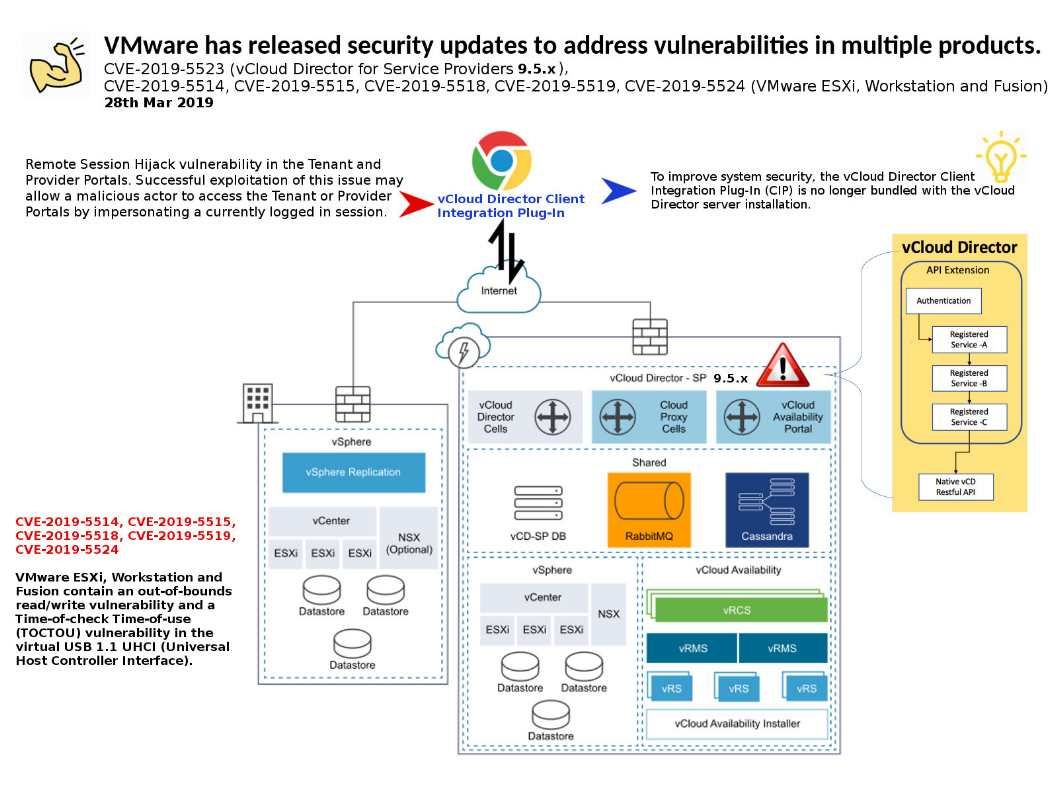
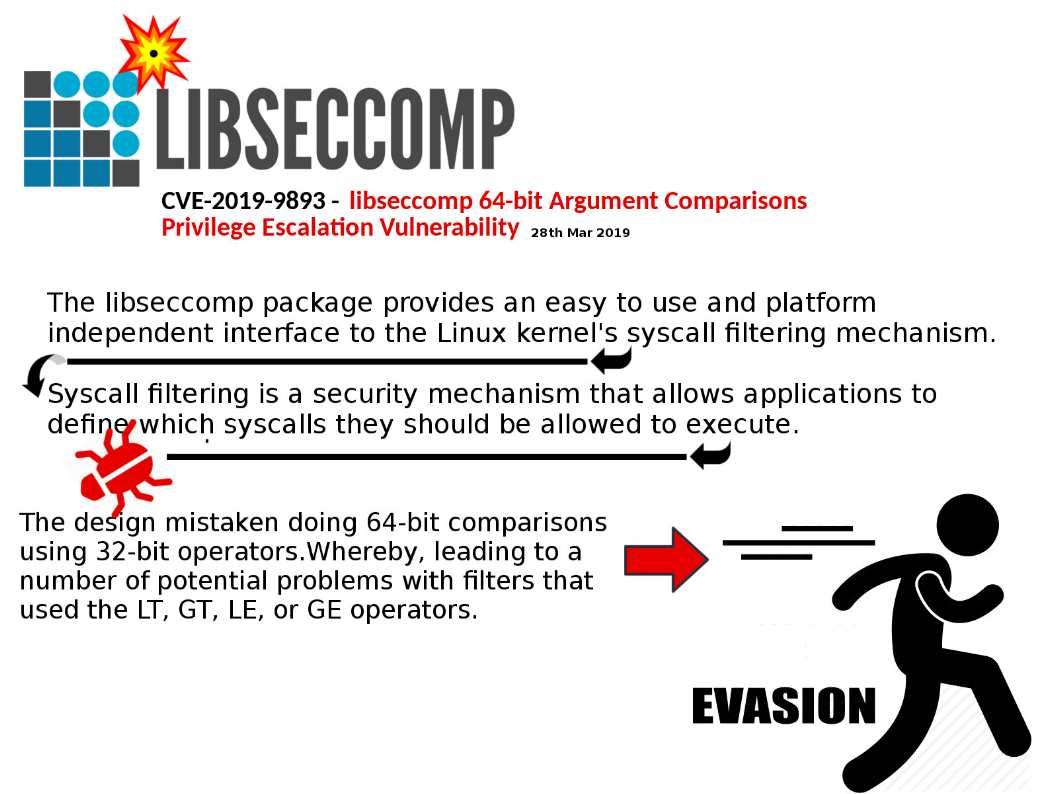
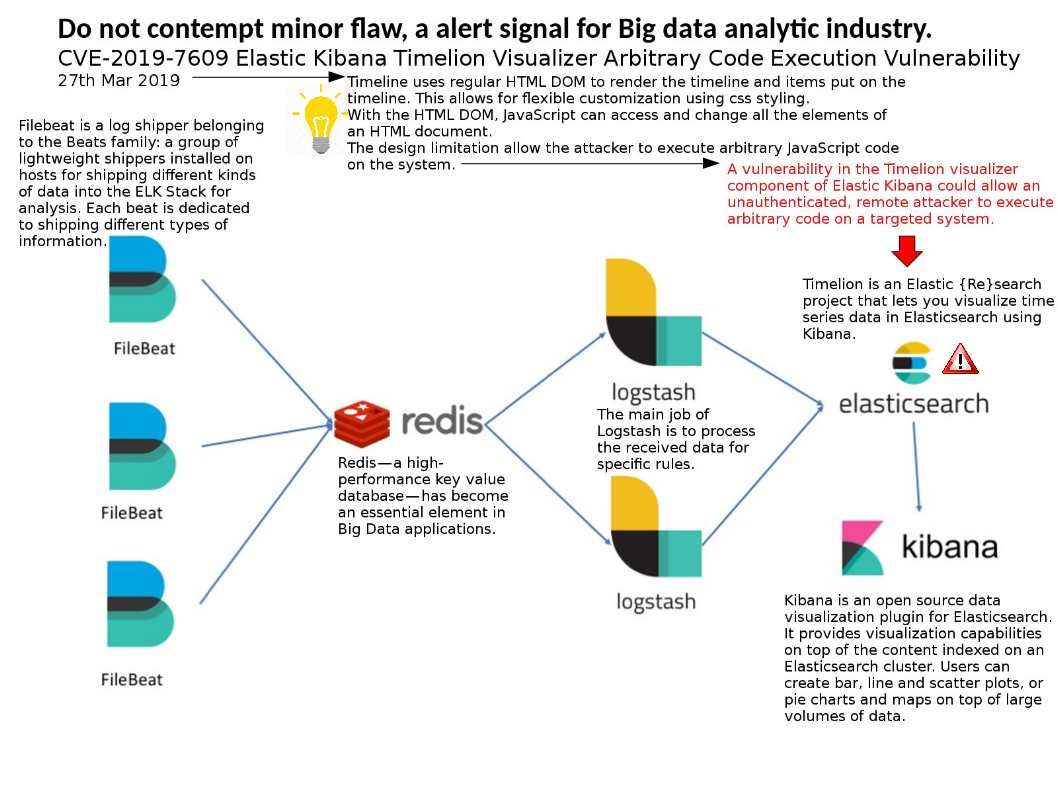
Preface: The vulnerability if not require attacker conduct scam to persuade a user. It is a extreme dangerous vulnerability.
Technical background of Kubernetes: Kubernetes (often referred to as K8s) is an open source system for automatically deploying, extending, and managing containerized applications. The system was designed by Google and donated to the Cloud Native Computing Foundation (now the Linux Foundation).
Synopsis: The container escape vulnerability in runc awaken docker users in regard to cyber security in their domain. Perhaps the vulnerability of CVE-2019-1002101 is in high severity level. But strongly believed that it is an alert. Hey administrator, staying alert! Should you have interest receive a quick understanding, please refer to attached diagram.
Kubernetes has released software updates at the following link: https://github.com/kubernetes/kubernetes/releases