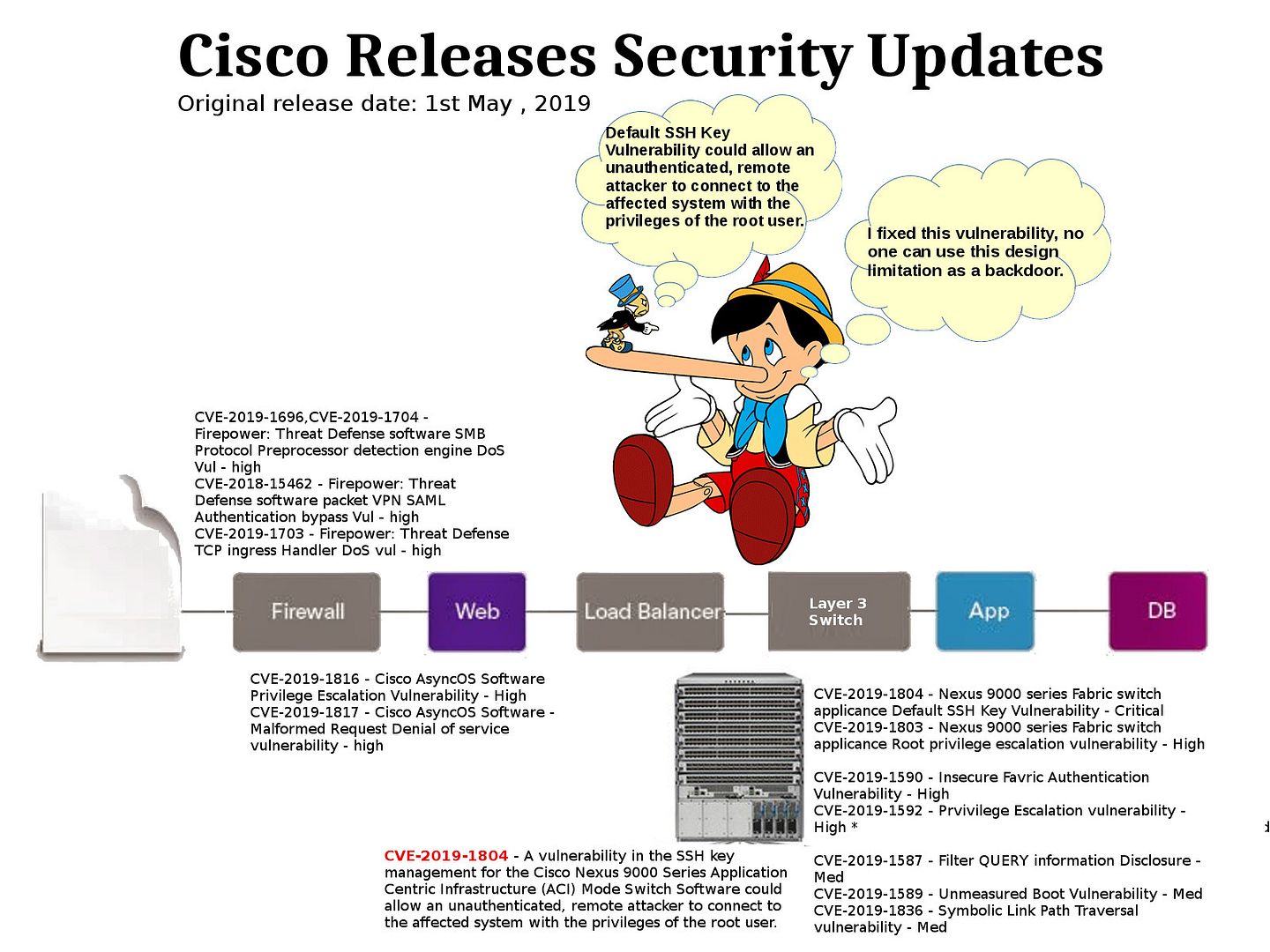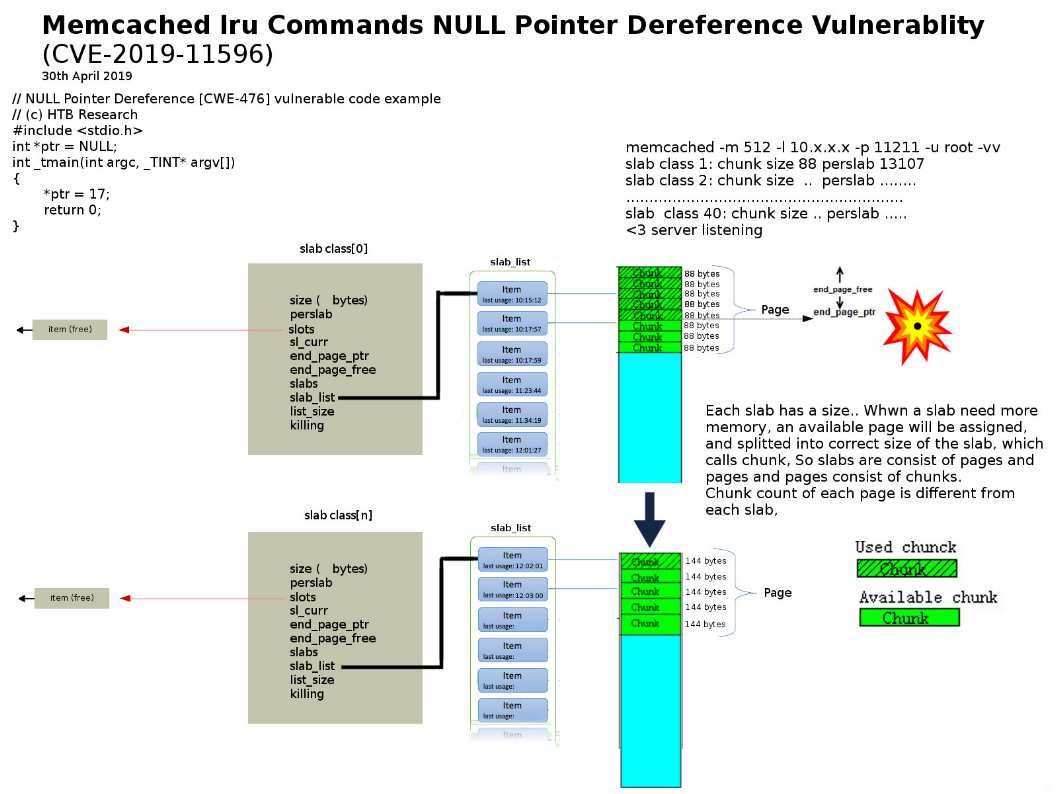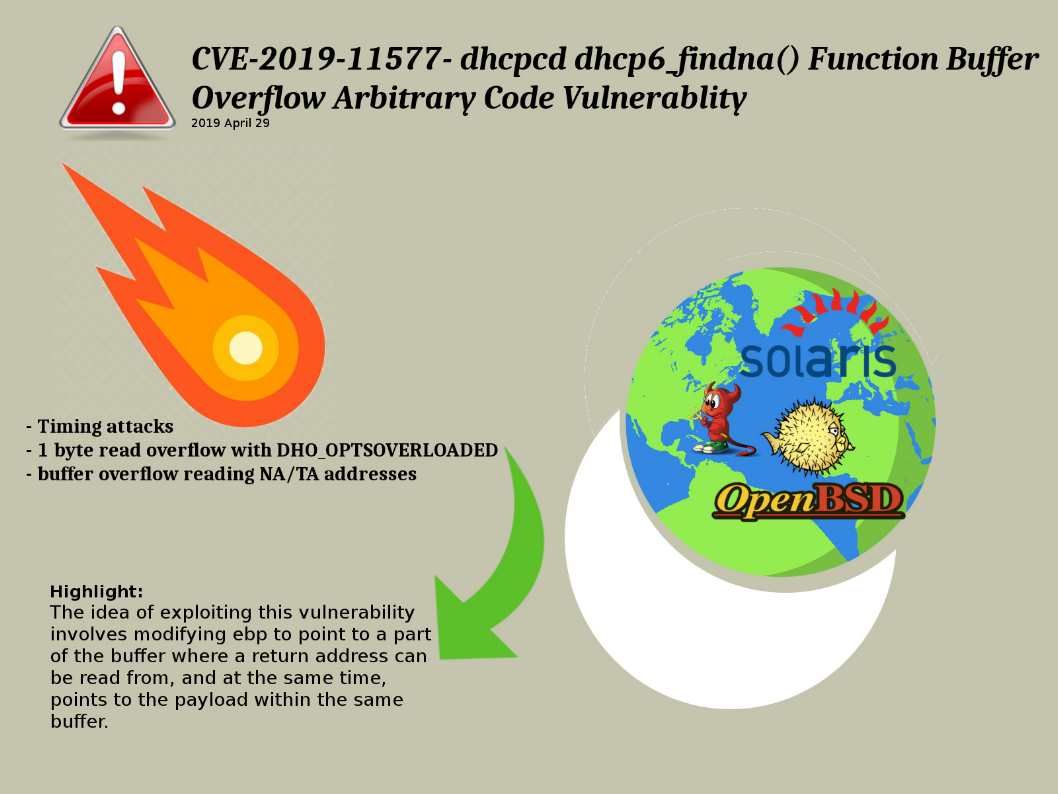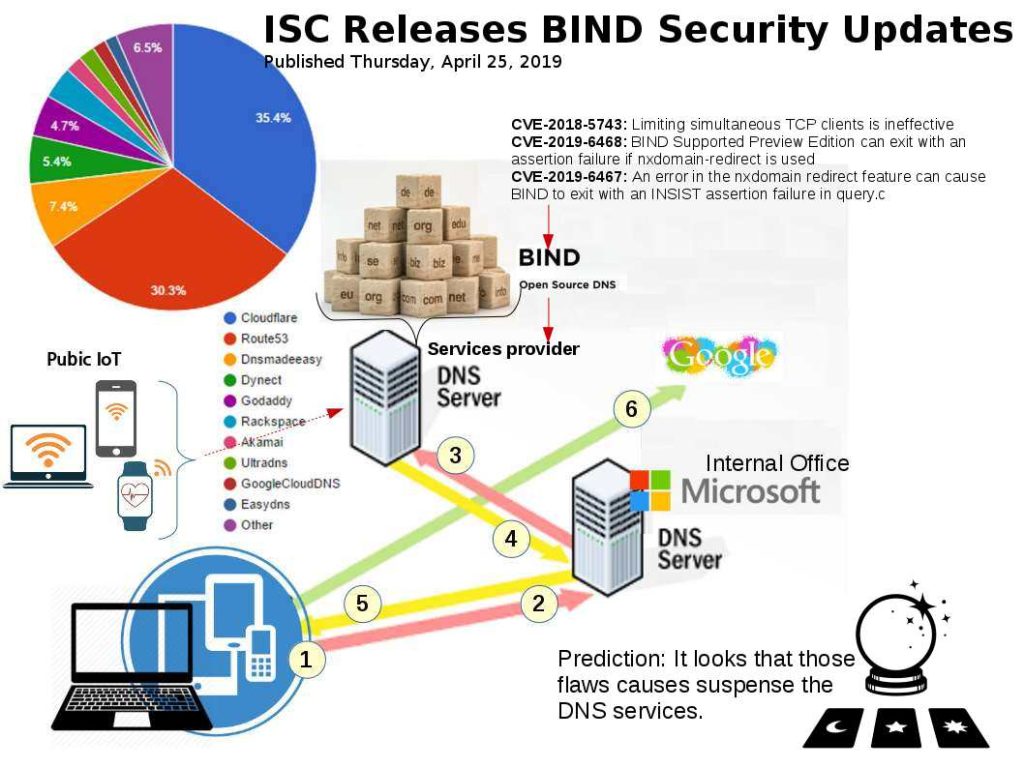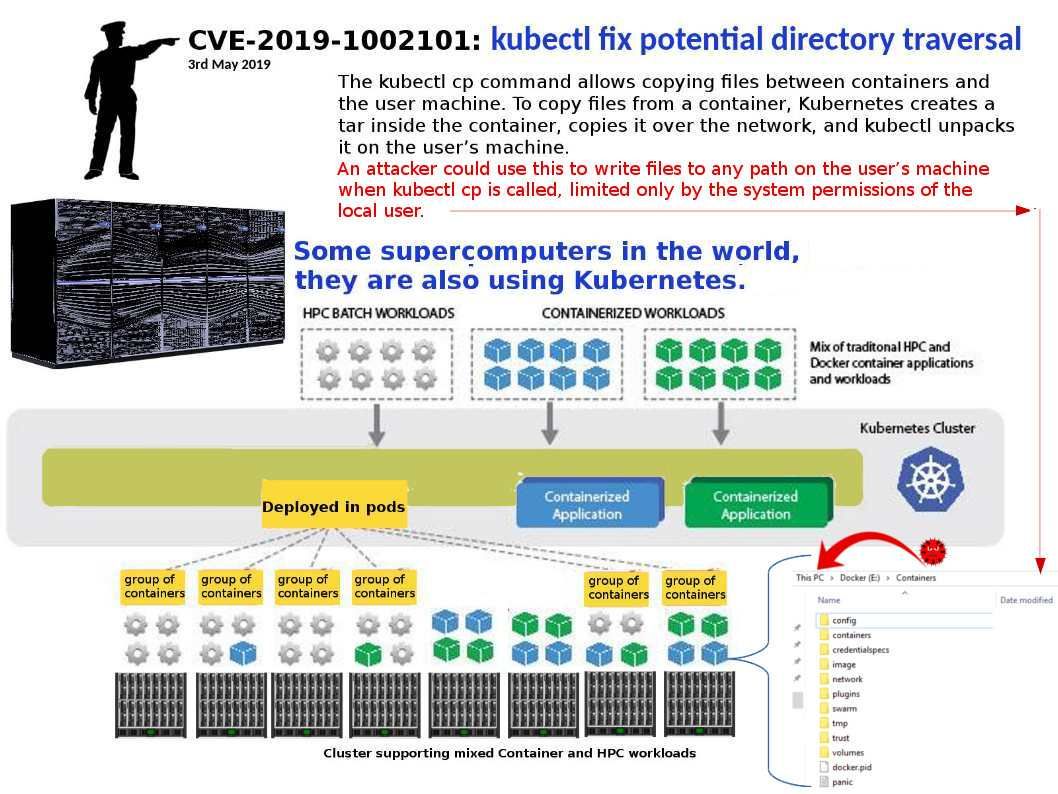
Preface: Some supercomputers in the world, they are also using Kubernetes.
Technical background: kubectl controls the Kubernetes cluster manager.Make use of “kubectl cp” command is able to copy files and directories to and from containers.
Vulnerability details: An attacker can fool a user to use the kubectl cp command to copy and store a malicious tar file in a container. Successful exploitation may allow an attacker to overwrite or delete any file in the user’s security context.
Remedy: Kubernetes has released a software update via the following link: https://github.com/kubernetes/kubernetes/releases
Comment: This vulnerability looks has difficulties to compromise the system. However the level of risk depends on the feature of the docker services. So do not contempt the issue because it is hard to predict the level of risk.