Preface:
Human immunodeficiency virus infection and acquired immune deficiency syndrome (HIV/AIDS) is a spectrum of conditions caused by infection with the human immunodeficiency virus (HIV).
Background:
On July 2017, Meltdown was discovered independently by Jann Horn from Google’s Project Zero, Werner Haas and Thomas Prescher from Cyberus Technology, as well as Daniel Gruss, Moritz Lipp, Stefan Mangard and Michael Schwarz from Graz University of Technology. The same research teams that discovered Meltdown also discovered a related CPU security vulnerability now called Spectre.
Meltdown is a hardware vulnerability affecting Intel x86 microprocessors, IBM POWER processors, and some ARM-based microprocessors.It allows a rogue process to read all memory, even when it is not authorized to do so.
Spectre is a vulnerability that affects modern microprocessors that perform branch prediction. On most processors, the speculative execution resulting from a branch misprediction may leave observable side effects that may reveal private data to attackers.
Remark: On January 28, 2018, Intel was reported to have shared news of the Meltdown and Spectre security vulnerabilities with Chinese technology companies before notifying the U.S. government of the flaws.
A dramatic development
The CPU manufacturer (AMD) claimed that they are not vulnerable to this design flaw. As a result all we are focus and believe that the flaw only given by Intel. Regarding to this CPU design flaw, there are total of three design flaws. They are Spectre (Types 1 and 2) and Meltdown (Type 3). However AMD Zen core based products are only immune to Meltdown. And therefore they are still under the Spectre flaw finally. The official announcement by AMD shown as below:

The announcement by AMD looks that they are not going to take any action in regards to Spectre. Their situation similar comparing to the operating system and computer relationship. The operation itself do not have feature to avoid virus. As a result, it relies on antivirus program. The CPU vendor (AMD) apply the similar idea of concept to this vulnerability and therefore they transfer the responsibility to OS vendor.
Vendors have begun to roll out OS patches
Microsoft
However so called install the remediation CPU patch looks amazed the windows OS user. I am using window 7 instead of windows 10. Perhaps I just did the windows update this morning. It behind my seen that CPU vulnerability still valid on my PC. The cache-misses as compared to missed-branches data collected from Spectre is possible on my PC (see attached screen-shot for reference).

Perhaps my diagnosis executed on 19th Jan 2018. It can’t tell the truth explicitly. Since at least 3 rounds of patch (patch tuesday) has been executed. In order to protect your windows OS. Please refer to below url for references (Microsoft official announcement)
https://portal.msrc.microsoft.com/en-US/security-guidance
Apple iPhone
Apple iPhone released that patch on 23rd Jan 2018. For more details, please refer to below picture diagram for reference.

Apple computer issue the patch on 8th Jan 2018 only for Spectre attack. The remediation products include iPhone, MacOS and Safari.
macOS High Sierra 10.13.2 Supplemental Update
https://support.apple.com/en-hk/HT208397
Safari 11.0.2 includes security improvements to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715).
https://support.apple.com/en-hk/HT208403
iOS 11.2.2 includes security improvements to Safari and WebKit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715).
https://support.apple.com/en-hk/HT208401

Linux – Retpoline
In order to mitigate against kernel or cross-process memory disclosure (the Spectre attack), OS developer find the following way. A technical definition so called retpoline. A retpoline is a return trampoline that uses an infinite loop that is never executed to prevent the CPU from speculating on the target of an indirect jump. Technical details shown in below url:
Linux https://lkml.org/lkml/2017/11/22/956
The remediation step will be focus on the following protection technique.
ARM (Protection Unit (PU))
The advantages of this system are:
- Access control held entirely on-chip (no need for any off-chip tables)
- Provides four levels of access control, cache and write-buffer control
- Separate control over instruction and data caches.
The disadvantages are:
• Small number of regions
• Restrictions on region size and alignment.
VMware

Even though mitigation plan has been released. For recent chip design weakness, once the patches are applied, developers have to rewrite code to support the patch. Perhaps VMware programming team cannot address the problem in full scale. But you do not have choices if you are a VM users!
VMware Response to Speculative Execution security issues, CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 (aka Spectre and Meltdown) (52245) – see below url for reference.
https://kb.vmware.com/s/article/52245
Cloud platform service provider
AWS – Amazon
As far as I know, Cloud services provides is the earlier customer to receive the patch provided by Intel. The guidelance release to remediate meltdown and Spectre vulnerabilities start from the 1st version issued on 3rd Jan 2018 to 23rd Jan 2018 (version 17). For more details, please refer below url for reference.
https://aws.amazon.com/security/security-bulletins/AWS-2018-013/
Discussion checkpoint
Regarding to my observation. The similar vulnerability found on Aug 2017. I remember that my article posted here mentioned before (see below url for reference). In the meantime, I personally agree with Intel announcement that based on the CPU features to date, many types of computing devices with many different vendors’ processors and operating systems are susceptible to these exploits. And therefore Intel might not the only victim.
The enemy of ASLR (Address space layout randomization) – memory leak
The cache side channel attack of this security incident on Intel side looks compatible to other chips vendor. The worst scenario is that similar channel attack will be happened once you have cache. So, foreseen that this is the prelude of new form of attack in this year!
Hardware vendor patch announcement on 5th Jan 2018
ARM https://developer.arm.com/support/security-update
Intel https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
F5 https://support.f5.com/csp/article/K91229003
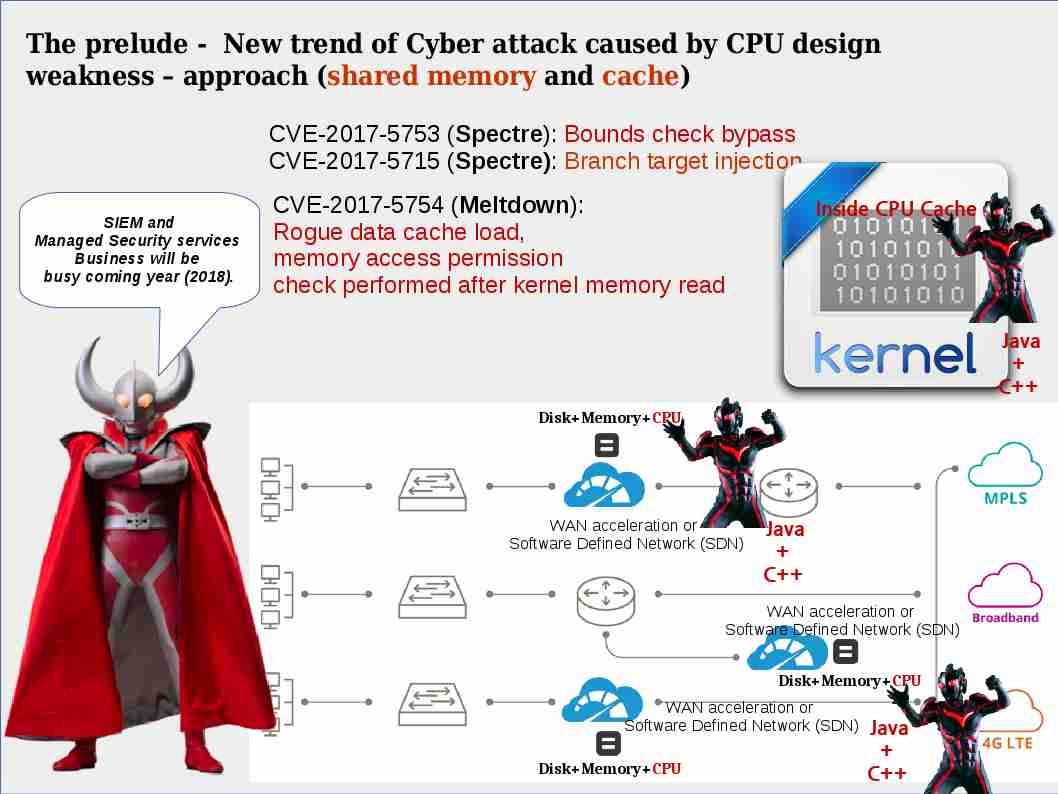
WAN acceleration solution vendor
I speculated that WAN acceleration solution vendor and Software defined network will be the next of the victims but now they are keep silent. Perhaps headline news article comment that no know cyber attacks deployed similar definition of theory utilization in past. But I’m in doubt?
As of today short term summary:
The research report evident that the Meltdown vulnerability occurs on Intel processors only, while the Spectre vulnerability can possibly affect some Intel, AMD, and ARM processors. AMD not vulnerable to GPZ Variant 3 since AMD enforced use of privilege level protections within paging architecture. However AMD is not going to take any action in regards to Spectre. Their situation similar comparing to the operating system and computer relationship. The operation itself do not have feature to avoid virus. As a result, it relies on antivirus program. The CPU vendor (AMD) apply the similar idea of concept to this vulnerability and therefore they transfer the responsibility to OS vendor. As a matter of fact, Intel CPU design flaw lack of permission check. It allows a rogue process to read all memory, even when it is not authorized to do so. Spectre, an attacker may be able to extract information about the private data using a timing attack.
Since the flaw given from CPU design. The alternative taken today is urge OS and application vendor setup the protect front-line to avoid Java, C++ execute the malicious code causes leak passwords and sensitive data. The situation similar the HIV virus attacks a specific type of immune system cell in the body, known as CD4 helper lymphocyte cells. HIV destroys these cells, making it harder for your body to fight off virus. Meltdown and Spectre given from CPU fundamental design flaw. If we are only relies on OS and application remediation. Threat actors still have opportunities jump to CPU side satisfy their wants.
End of topic, thank you.