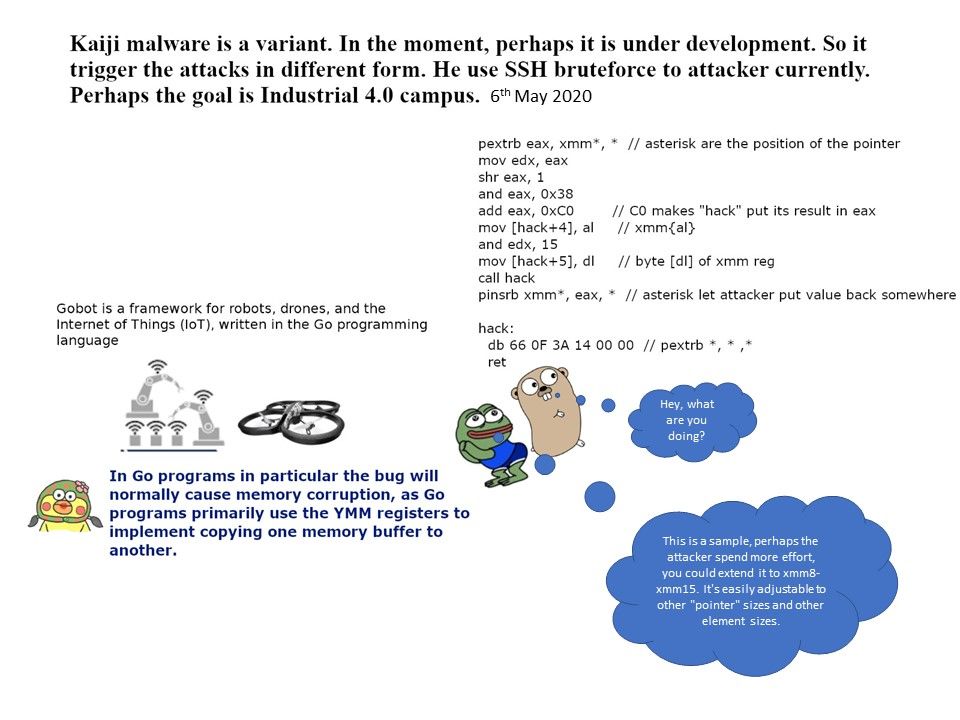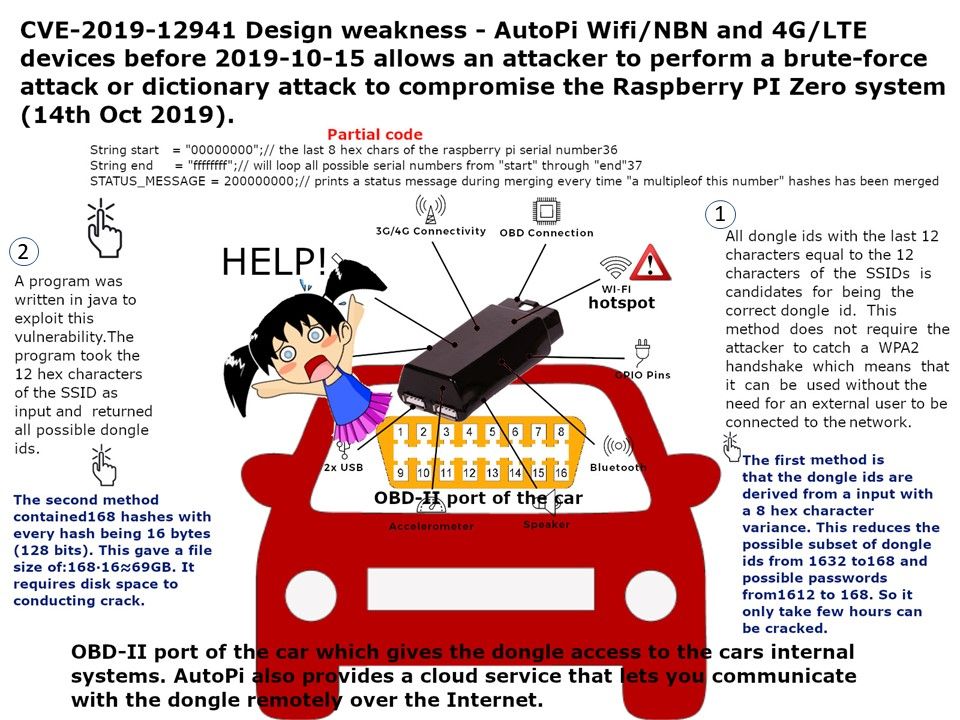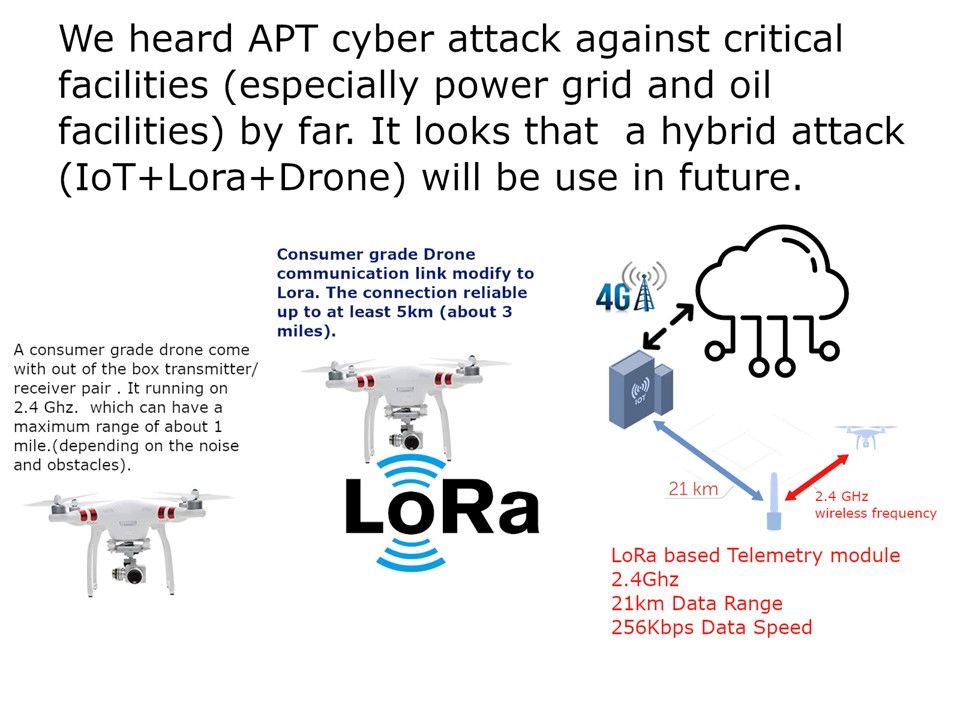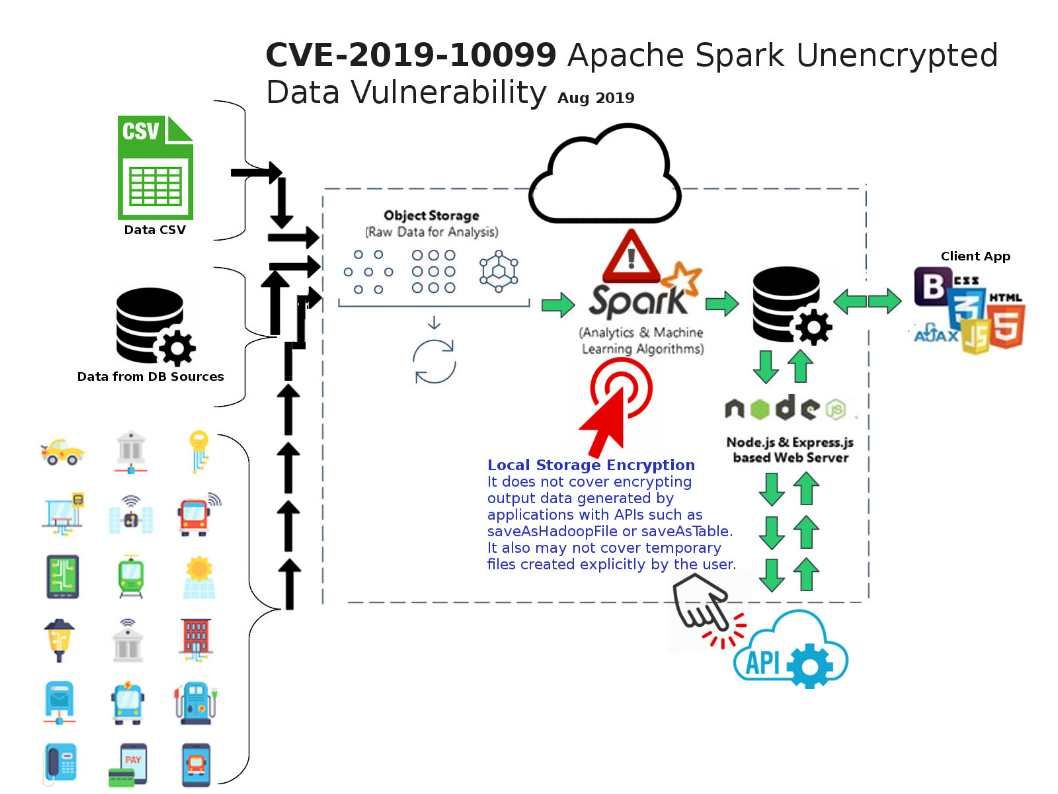
Preface: Baxter US, Caterpillar, Digi International, Hewlett Packard Enterprise, Intel, Rockwell Automation, Schneider Electric and Trek are impact by this vulnerability.
There are more vendor which do not know the actual status.
Vulnerability details:
An attacker from outside the network taking control over a device within the network, if internet facing. There are more ways to exploit this vulnerability, please refer below link for reference.
Root causes: The attacker exploit of the IP protocol flexibility. That is the incoming IPv4 fragments over an IP-in-IP tunnel. As we know, IPv4 found early than Internet services. At that period of time the most serious incident is merely virus infection to local machine. Machine to Machine communication will be make use of serial cable or Novell network. In short, it is a simple architecture. But the attacker can be exploit the design weakness engaging the cyber attack to digital world.
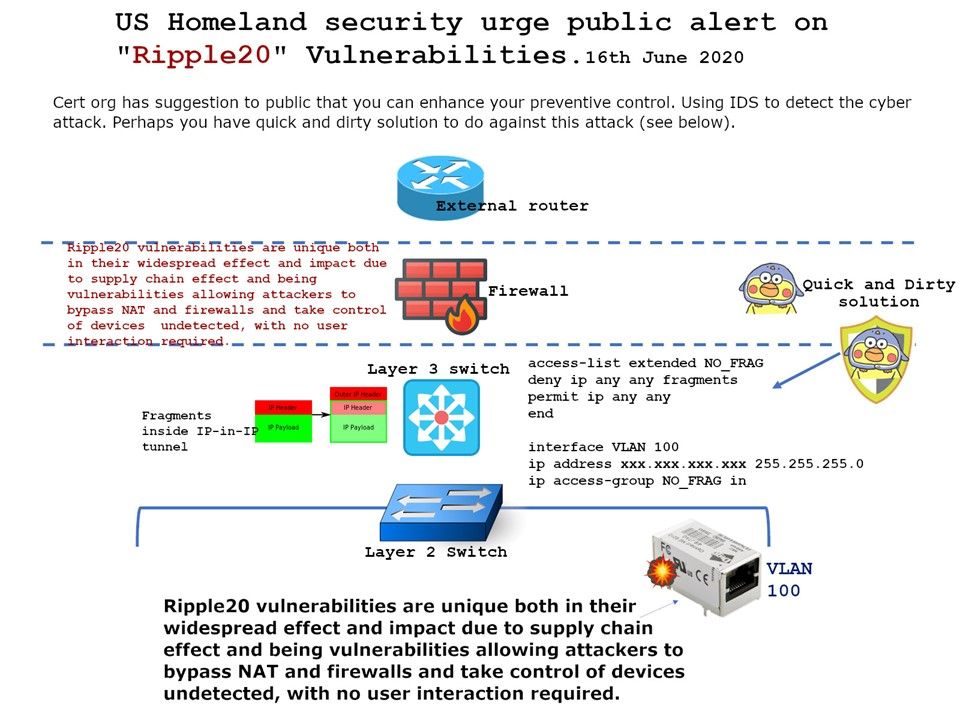
Remedy: You can follow cert.org recommendation install IDS (refer below url link) or refer to attached diagram. A quick and dirty solution.
https://kb.cert.org/vuls/id/257161
.jpg?width=1920&height=1080&fit=bounds)