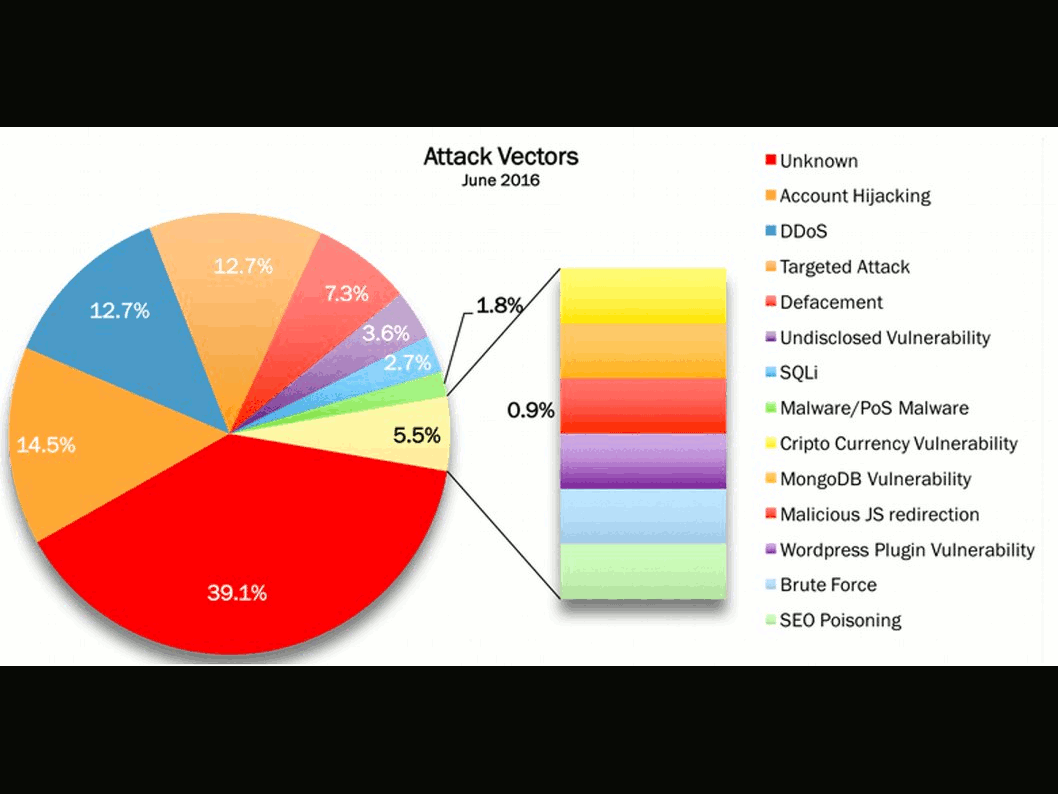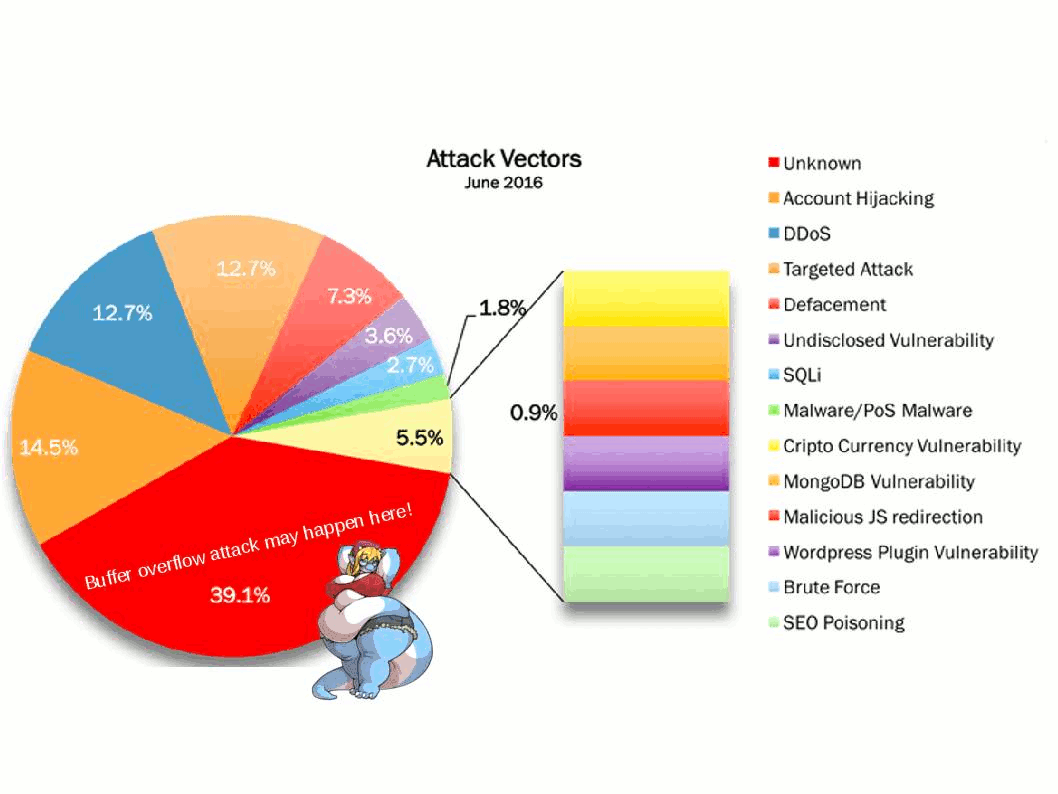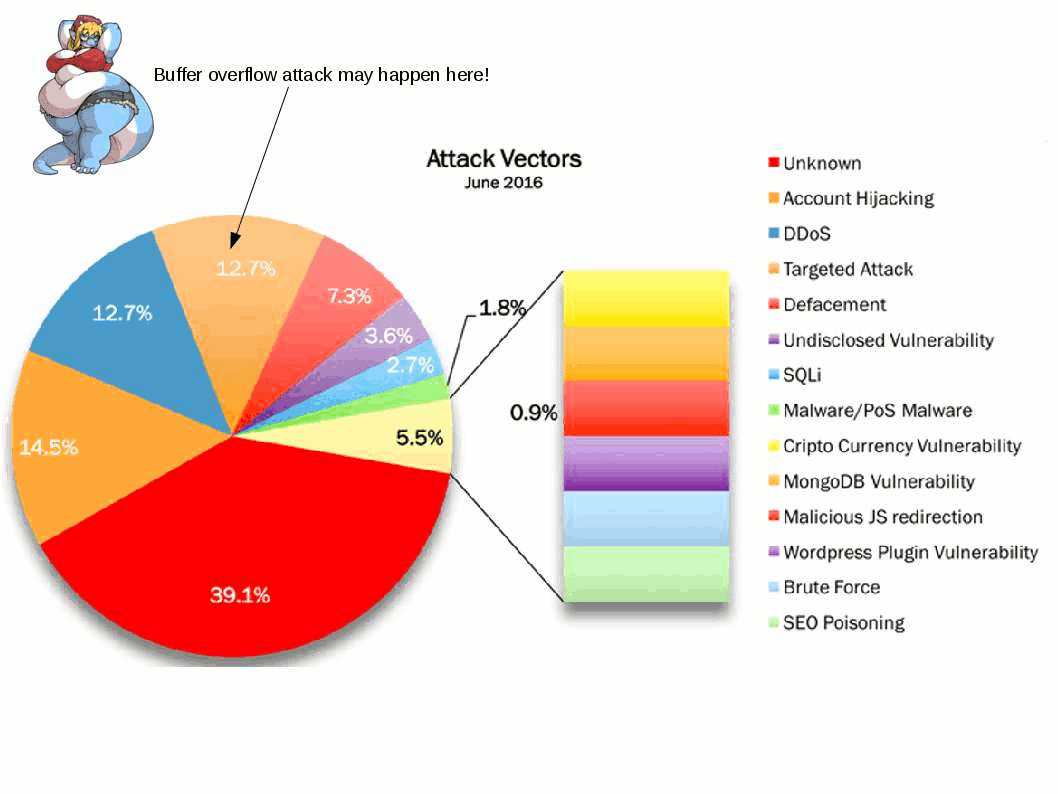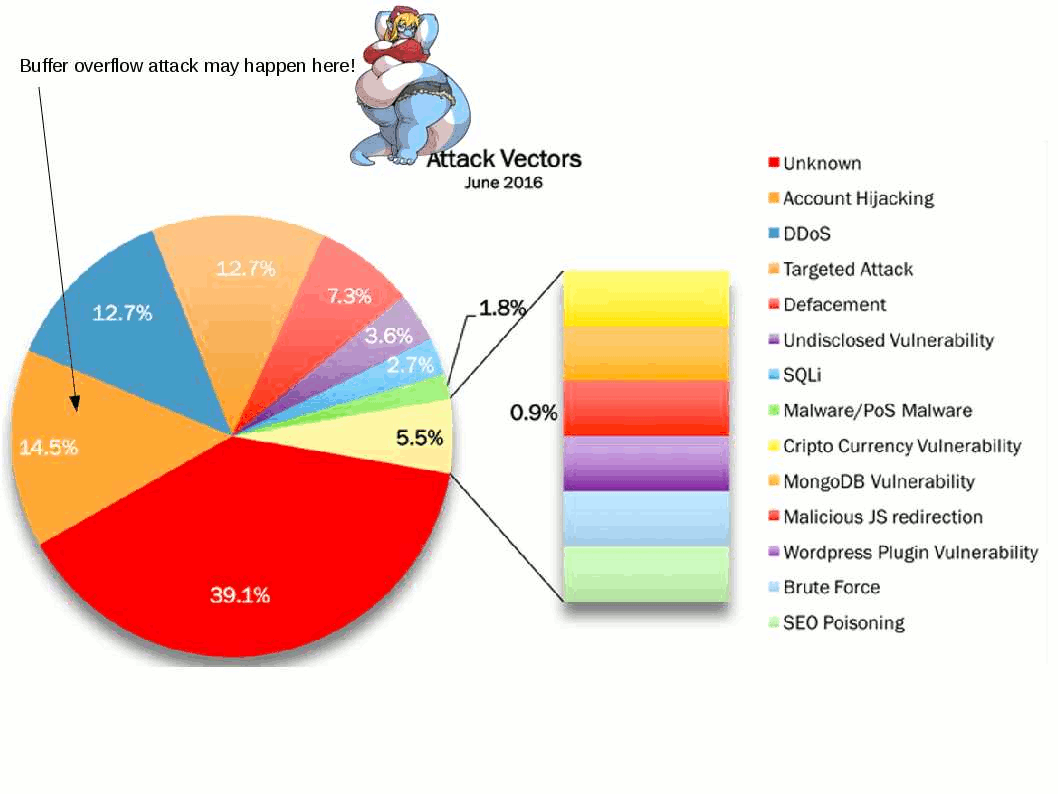
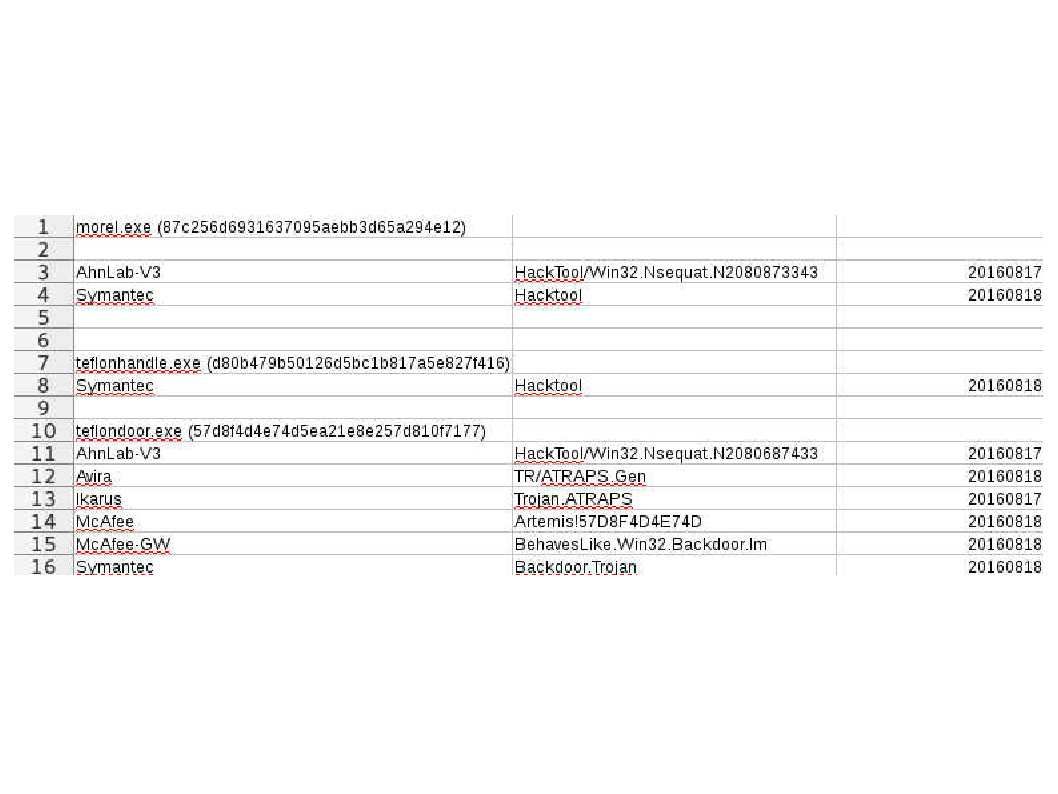
IT world encounters Storm in a tea cup from weekly. Heard that Microsoft blame Google mistaken on their web browser (chrome) design mistake causes vulnerability occurs (CVE-2016-7255). On hand information described that hacker would like to find back door in web browser (Google chrome), they found a privileges escalation at the end. It looks that similar vulnerability caused by web browser will be happened in future. The vulnerable service daemon is the win32K.sys this round!
What is win32K.sys – It is a multi user win 32 driver file.
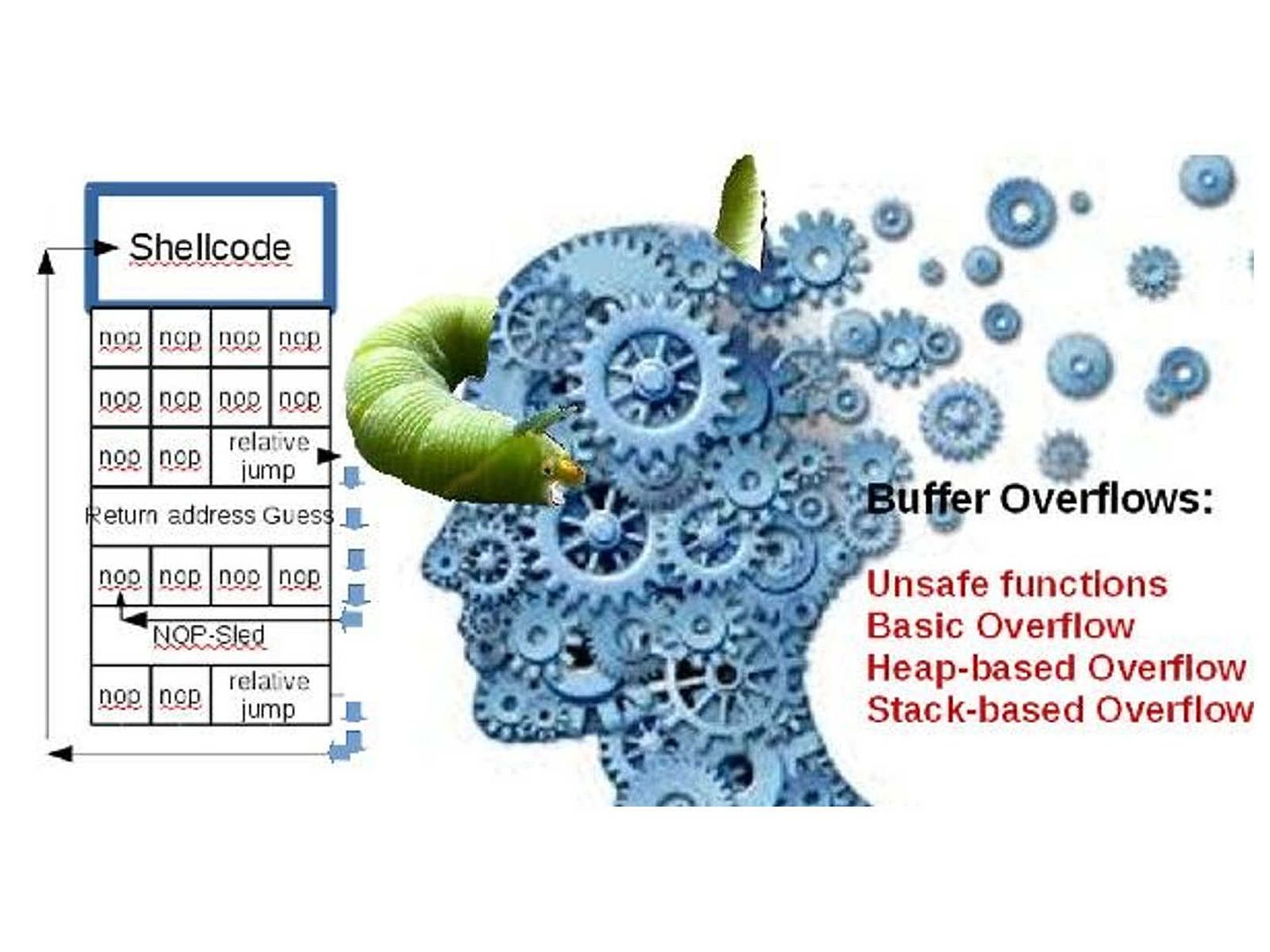
It looks that win32K.sys has design limitation, a page_fault_in_nonpaged_area discovered in 2009. But what is page fault in non page area? The symptom is that application asked for a page of memory in order to continue, and the page was not available then crash.
Suspected that why google chrome is the instigator
When Chrome attempts to access critical data from memory that was supposed to be stored in the Non-Paged area, but cannot find it. Because this area of memory is reserved for the Windows core.
Below windows OS register keys relate to CVE-2016-7255
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe “Debugger” = ‘svchost.exe’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe “Debugger” = ‘svchost.exe’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Exp.CVE-2016-7255
HKEY_LOCAL_MACHINE\SOFTWARE\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = ’0′
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = ’0′
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore “DisableSR ” = ’1′
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe “Debugger” = ‘svchost.exe’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe “Debugger” = ‘svchost.exe’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “3948550101?
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “xas
HKEY_CURRENT_USER\Software\Exp.CVE-2016-7255
Comment:
CVE-2016-7255 hit design limitation and causes local privilege escalation. Patch is available. But my comments this time is wait for next round of announcement by Microsoft. What’s the reason? …….!!!!!