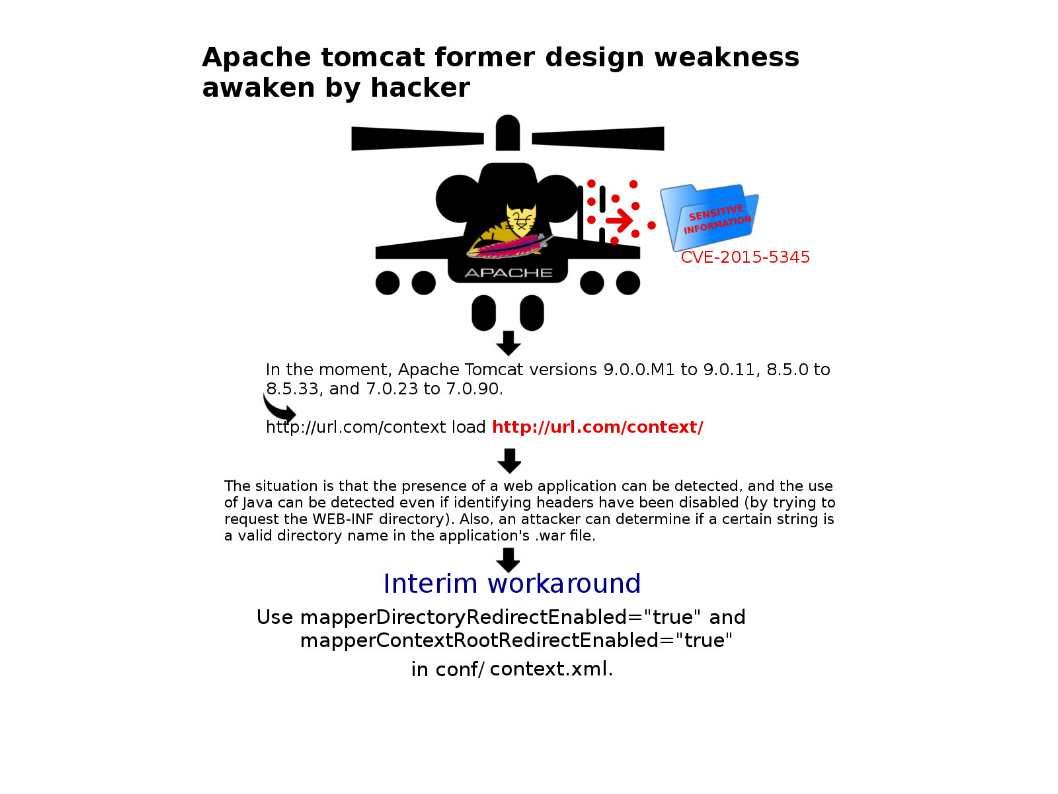
A vulnerability occurs in Apache Tomcat versions 9.0.0.M1 to 9.0.11, 8.5.0 to 8.5.33, and 7.0.23 to 7.0.90. Exploit this vulnerability to obtain sensitive information.
For more detail, please refer to attached diagram.
Official URL shown as below:

A vulnerability occurs in Apache Tomcat versions 9.0.0.M1 to 9.0.11, 8.5.0 to 8.5.33, and 7.0.23 to 7.0.90. Exploit this vulnerability to obtain sensitive information.
For more detail, please refer to attached diagram.
Official URL shown as below:
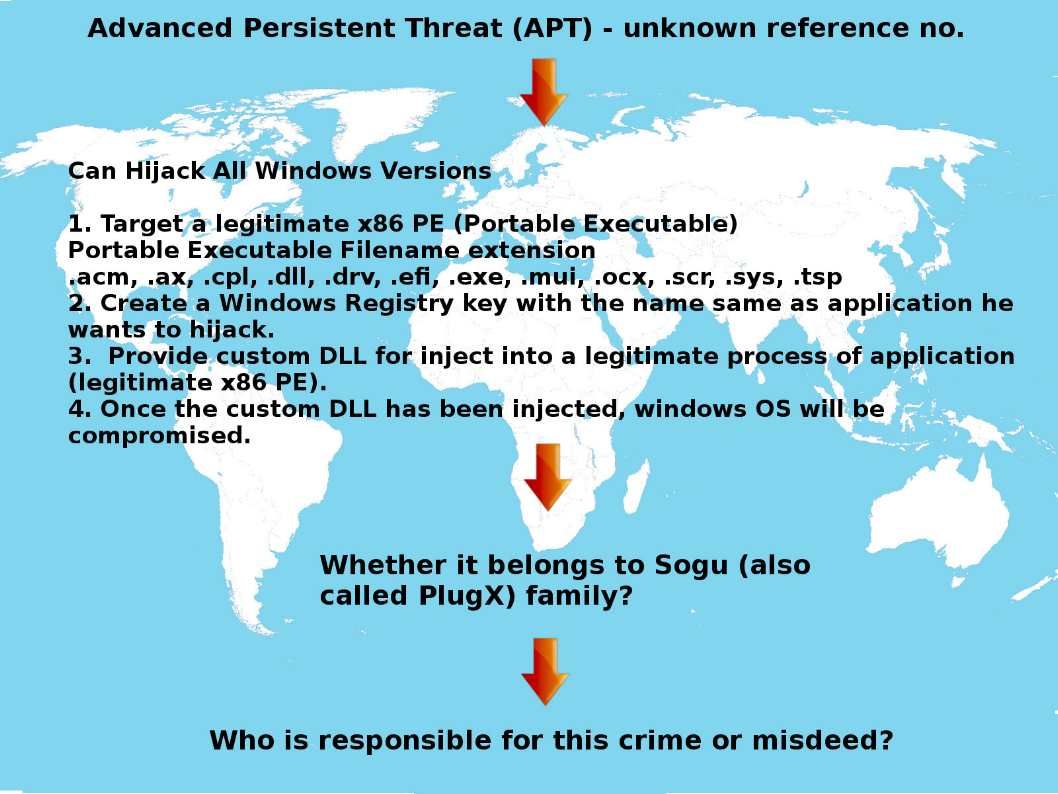
The cyber attack hot topic we focus retail payment system (Fastcash campaign) and adobe product vulnerabilities this week. However an additional cyber security alert announced by DHS. Yes, it is a APT cyber attack activities.
APT processes require a high degree of covertness over a long period of time. If you habit to observe the online real time cyber attack statis map. It looks that cyber attack vector in north korea not in high volume. As far as we know, an APT usually targets either private organizations, states or both for business or political motives. Do you experience below malware actvities?
Can Hijack All Windows Versions
1. Target a legitimate x86 PE (Portable Executable)
2. Create a Windows Registry key with the name same as application he wants to hijack.
3. Provide custom DLL for inject into a legitimate process of application (legitimate x86 PE).
4. Once the custom DLL has been injected, windows OS will be compromised.
Whether we can blame Microsoft fifteen years old undocumented legitimate feature?
Should you have interest for APT 38. Below URL can provide the details.
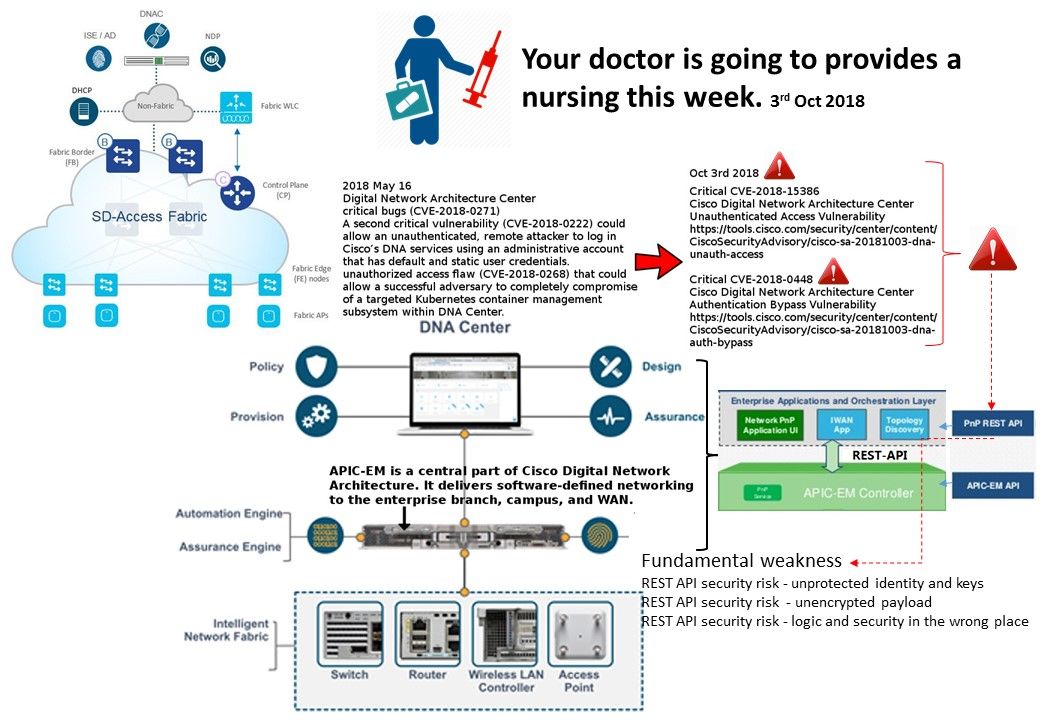
Your doctor is going to provides a nursing this week. Since vendor only provided high-level overview of vulnerability. But believe that the weakness given by REST-API.
Critical CVE-2018-15386
Cisco Digital Network Architecture Center Unauthenticated Access Vulnerability
https://tools.cisco.com/
Critical CVE-2018-0448
Cisco Digital Network Architecture Center Authentication Bypass Vulnerability
https://tools.cisco.com/
Additional 1:
Critical CVE-2018-15379
Cisco Prime Infrastructure Arbitrary File Upload and Command Execution Vulnerability
https://tools.cisco.com/
Additional 2:
High CVE-2018-15390
Cisco Firepower Threat Defense Software FTP Inspection Denial of Service Vulnerability
https://tools.cisco.com/
High CVE-2018-0455
Cisco Firepower System Software Detection Engine Denial of Service Vulnerability
https://tools.cisco.com/
High CVE-2018-15389
Cisco Prime Collaboration Provisioning Intermittent Hard-Coded Password Vulnerability
https://tools.cisco.com/
* A vulnerability in the install function of Cisco Prime Collaboration Provisioning (PCP) could allow an unauthenticated, remote attacker to access the administrative web interface using a default hard-coded username and password that are used during install.
High CVE-2018-15387
Cisco SD-WAN Solution Certificate Validation Bypass Vulnerability
https://tools.cisco.com/
High CVE-2018-15383
Cisco Adaptive Security Appliance Direct Memory Access Denial of Service Vulnerability
https://tools.cisco.com/

Firefox 62.0.3 and Firefox ESR 60.2.2 user require attention!
System vulnerability never stop and keep running in cyber world. Sometimes you feel frustrated and may give up! As a modern people, no way ! So the only way is follow to do so!
People say human can control computer systen. But now vulnerabilities control business, industry, healthcare, public facility. Perhaps it is not require bring up a robot. They are virtually control your life. It sound scary!
Mozilla Releases Security Updates for Firefox. The bug will causes remote attacker could exploit these vulnerabilities to take control of an affected system.
Security vulnerabilities fixed in Firefox 62.0.3 and Firefox ESR 60.2.2
https://www.mozilla.org/en-US/security/advisories/mfsa2018-24/
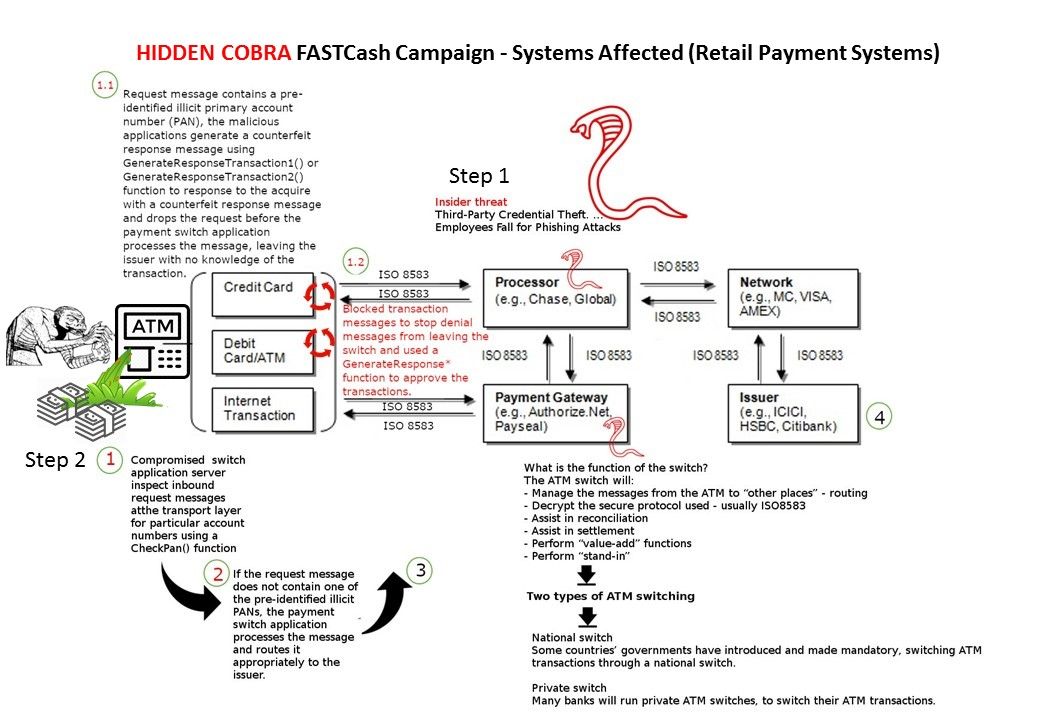
US Homeland security urge banking industry especially payment gateway services provider staying alert of new round of malicious cyber attack of their system. Similar of cyber attack was happened in Taiwan. The heist draw the cash equal to $2.6m (£2.1m). Homeland security reveal how the technique let ATM machine like human vomiting. But this is the bank note. You and me like it.
The key item of this attack is prioritize to compromise the switching application server. Then malicious applications generate a counterfeit response message using GenerateResponseTransaction1() or GenerateResponseTransaction2() function to response to the acquire with a counterfeit response message and drops the request before the payment switch application processes the message. As a result it fool the issuer with no knowledge of the transaction. Should you have interest of above details, please refer to below URL:
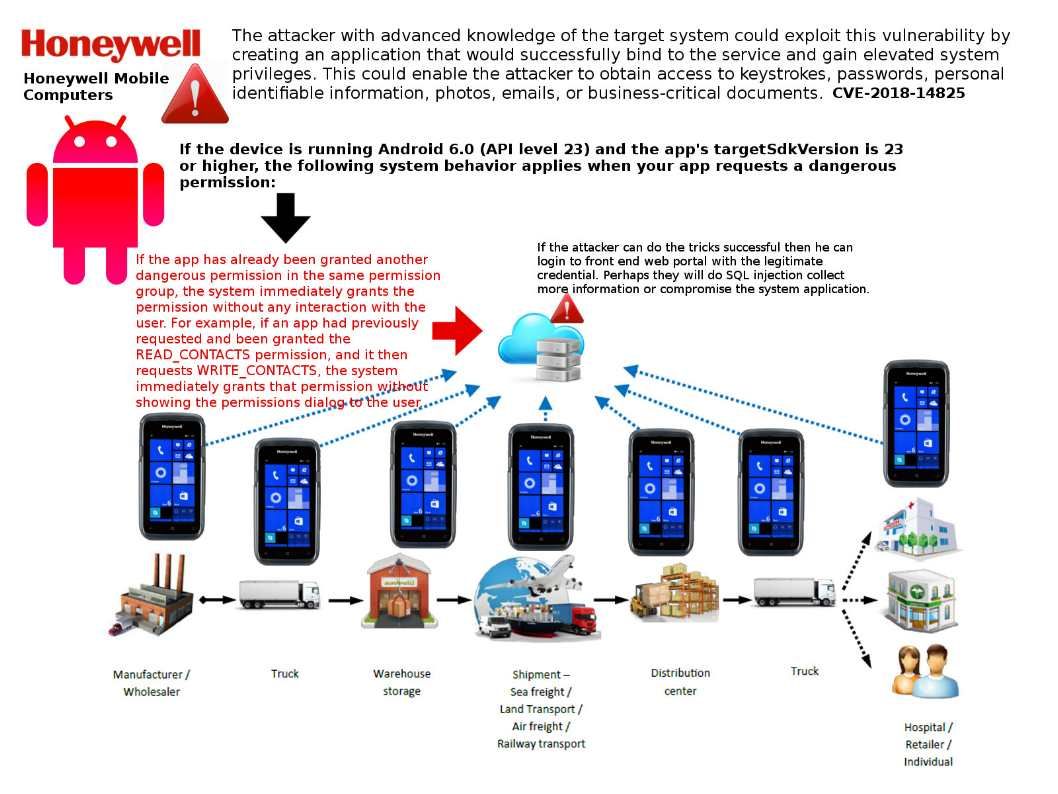
Port of Barcelona and Port of San Diego suffers cyber attack on September 2018. The San Diego port indicated the ransomware attack is mainly an administrative problem and the port is open and operating as usual. Cyber attacker conducting cyber attack to logistic industry not new. Honeywell one of the Industrial Control Systems leading manufacturer. They found that a vulnerability occurs in their android mobile computer devices. Since the headline news last week did not mentioned about the vulnerability details. In order to avoid hacker trigger the attack and vendor not going to provide the vulnerabiity details. My observation is that Android has dangerous permission group which allow user to execute in special circumustances.
The details are shown on attach diagram. Should you have interest, please refer to diagram.
The techincal reference can found in below url:
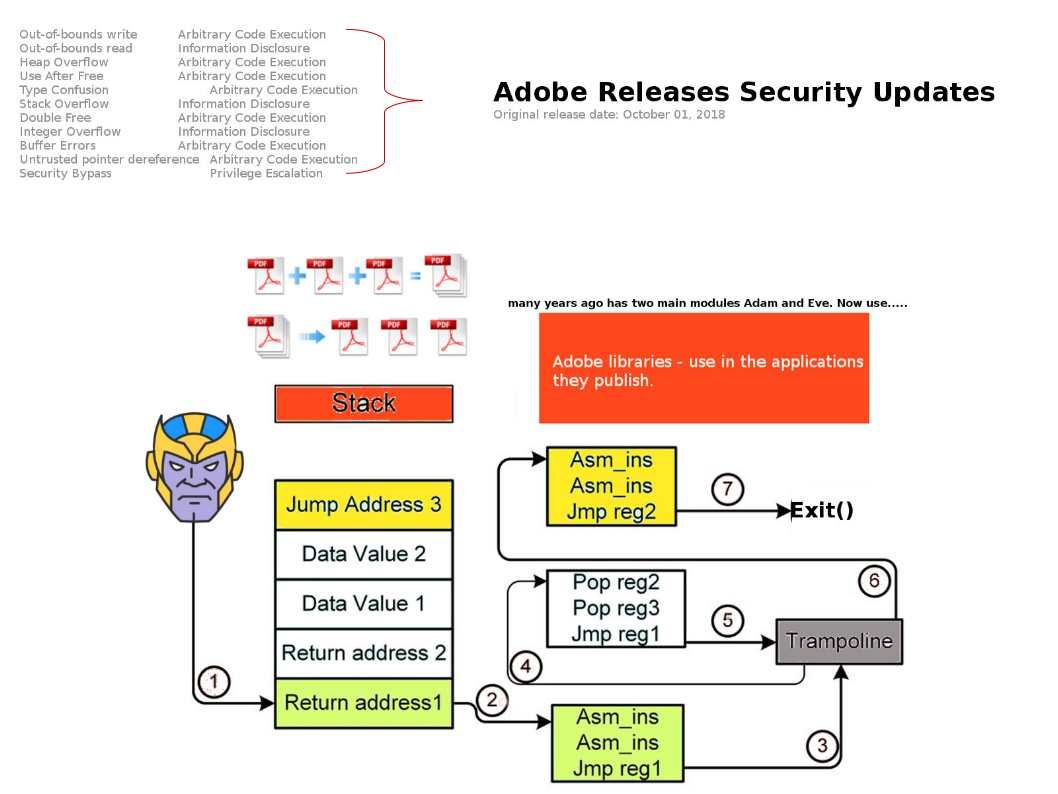
Adobe Releases Security Updates – Oct 2018
Many years ago adobe has two main modules Adam and Eve. Now use….. It looks that adobe products hard to manage memory space. So the critical vulnerabilities happens again. It looks that the software patching hit rate in demanding today. It is better to consider virtual patching now.
Adobe offical announcement shown as below:
https://helpx.adobe.com/security/products/acrobat/apsb18-30.html
In 80’s our daily life without any electronic type social media involves. But we understood that we are avoid to talk to the stranger. As time goes by, internet social media fine tune our mind. As a result we make friend and relies on this communication platform.
Since this is a popular open platform. It is hard to avoid scam activities. As a result, the risk factor will growth in such circumstances. Even though you have security awareness . But who can garantee the threat actor only focus to attack the indiviual instead of the social media vendor.
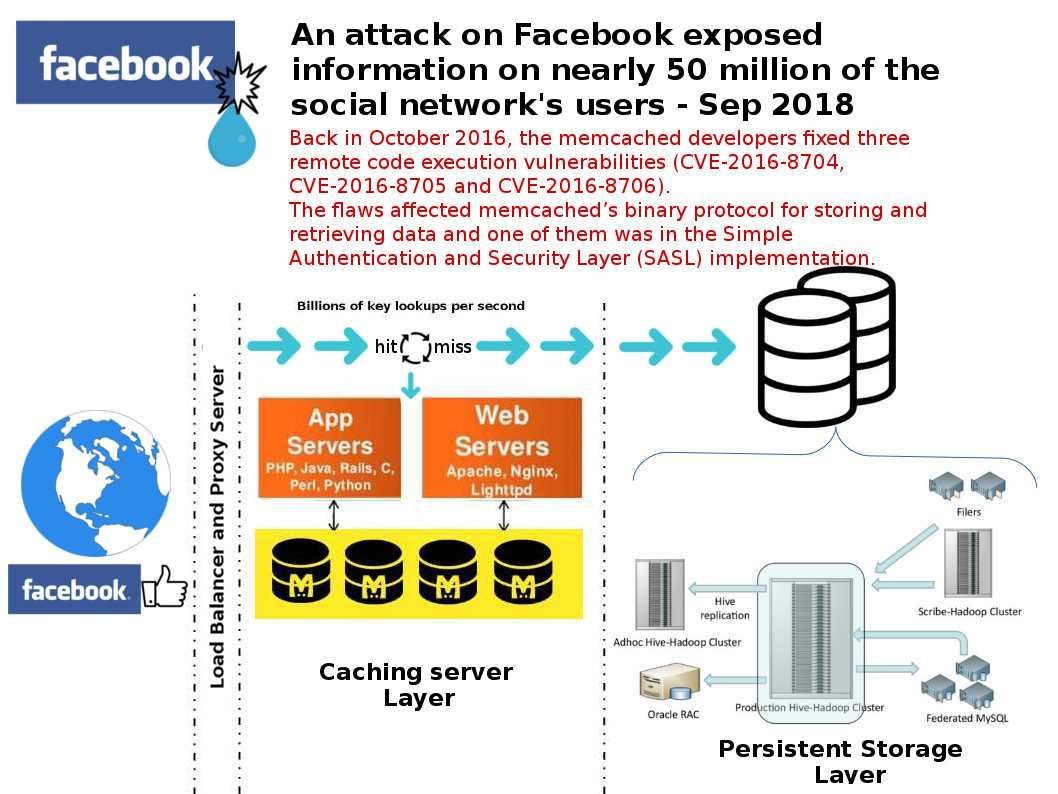
Back in October 2016, the memcached developers fixed three remote code execution vulnerabilities (CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706). The flaws affected memcached’s binary protocol for storing and retrieving data and one of them was in the Simple Authentication and Security Layer (SASL) implementation.
Remark: CVE-2016-8704 – An integer overflow in the process_bin_append_prepend function in Memcached, which is responsible for processing multiple commands of Memcached binary protocol, can be abused to cause heap overflow and lead to remote code execution.
Do you think the data breaches announced by Facebook yesterday whether it happen earlier last year but nobody know?

Even Though end user not affected by the DNSSEC Key Signing Key Rollover. But at least we know the internet world what is happening. For more detail, please refer below url for reference.
If run below command , result display
(dnssec-failed.org. 7200 IN 69.252.80.75).
It shown that DNSSEC is off.
$ dig @$server dnssec-failed.org a +dnssec

XSS vulnerabilities looks common in application world. But do not contempt this issue. A vulnerability in the php_handler function of PHP could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack on a targeted system.
XSS attack has different ways. For instance XSS callback,…etc
PHP has confirmed the vulnerability and released software updates.