Preface: A Java EE server is a server application that the implements the Java EE platform APIs and provides the standard Java EE services. Java EE servers are sometimes called application servers, because they allow you to serve application data to clients, much like web servers serve web pages to web browsers.
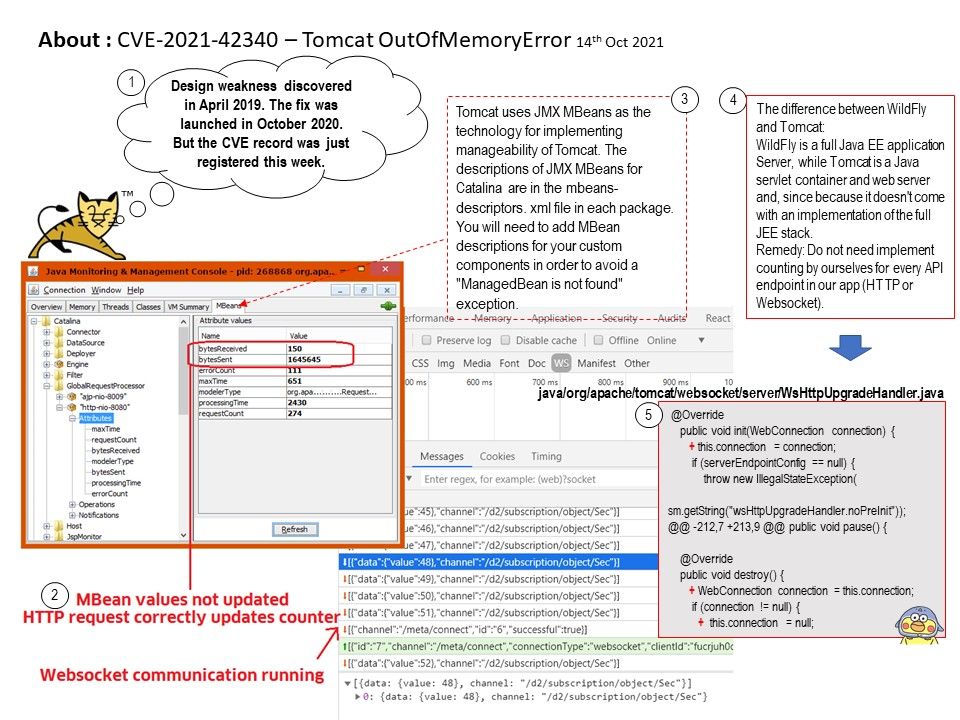
Background: The difference between WildFly and Tomcat:
WildFly is a full Java EE application Server, while Tomcat is a Java servlet container and web server and, since because it doesn’t come with an implementation of the full JEE stack.
Tomcat uses JMX MBeans as the technology for implementing manageability of Tomcat. The descriptions of JMX MBeans for Catalina are in the mbeans-descriptors. xml file in each package. You will need to add MBean descriptions for your custom components in order to avoid a “ManagedBean is not found” exception.
Vulnerability details: The fix for bug 63362 present in Apache Tomcat 10.1.0-M1 to 10.1.0-M5, 10.0.0-M1 to 10.0.11, 9.0.40 to 9.0.53 and 8.5.60 to 8.5.71 introduced a memory leak. The object introduced to collect metrics for HTTP upgrade connections was not released for WebSocket connections once the connection was closed. This created a memory leak that, over time, could lead to a denial of service via an OutOfMemoryError.
Remedy: Users of the affected versions should apply one of the following
mitigations:
- Upgrade to Apache Tomcat 10.1.0-M6 or later
- Upgrade to Apache Tomcat 10.0.12 or later
- Upgrade to Apache Tomcat 9.0.54 or later
- Upgrade to Apache Tomcat 8.5.72 or later
Technical reference: When using the WebSocket client to connect to server endpoints, the number of HTTP redirects that the client will follow is controlled by the userProperties of the provided javax.websocket.ClientEndpointConfig. The property is org.apache.tomcat.websocket.MAX_REDIRECTIONS. The default value is 20. Redirection support can be disabled by configuring a value of zero.
.jpg)
.jpg)