Preface: Linux mainly uses a paging mechanism to achieve virtual memory management. The size of the memory page is PAGE_SIZE bytes instead of 4 KB. On different platforms, the page size can range from 4 KB to 64 KB.
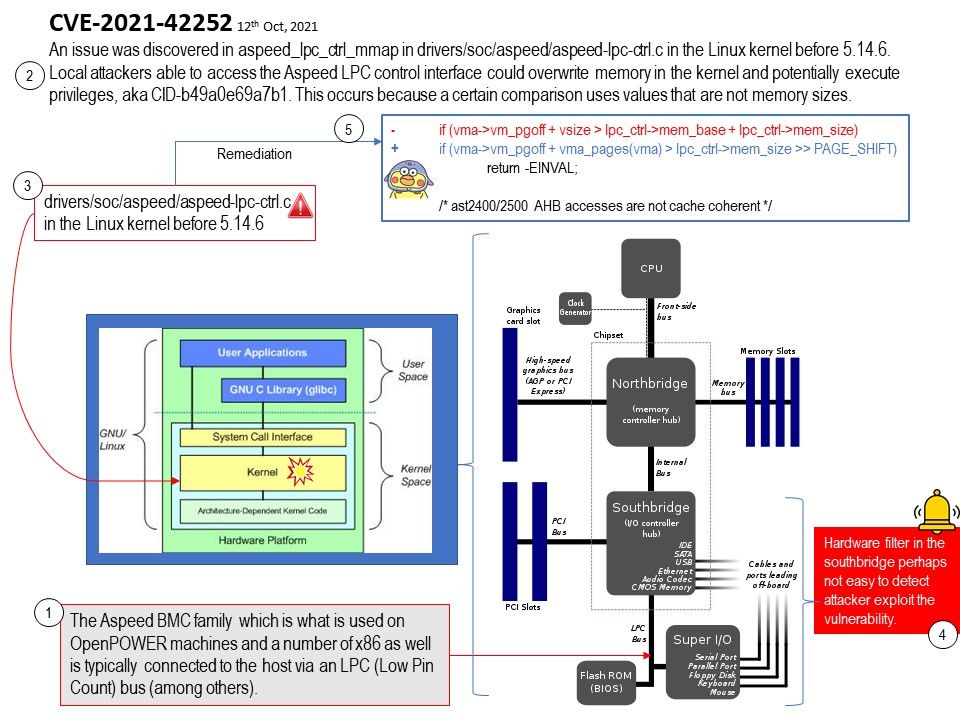
Background: The Aspeed BMC family which is what is used on OpenPOWER machines and a number of x86 as well is typically connected to the host via an LPC (Low Pin Count) bus (among others).
The check mixes pages (vm_pgoff) with bytes (vm_start, vm_end) on one side of the comparison, and uses resource address (rather than just the resource size) on the other side of the comparison. This can allow malicious userspace to easily bypass the boundary check and map pages that are located outside memory-region reserved by the driver.
Vulnerability details: CVE-2021-42252 – An issue was discovered in aspeed_lpc_ctrl_mmap in drivers/soc/aspeed/aspeed-lpc-ctrl.c in the Linux kernel before 5.14.6. Local attackers able to access the Aspeed LPC control interface could overwrite memory in the kernel and potentially execute privileges, aka CID-b49a0e69a7b1. This occurs because a certain comparison uses values that are not memory sizes.
Reminder: Hardware filter in the southbridge perhaps not easy to detect attacker exploit the vulnerability.
Official announcement:Please refer to the website for details – https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=b49a0e69a7b1a68c8d3f64097d06dabb770fec96
Remark: Seems no proof of concept disclosed till now. Refer to official details, it is a local attack. But this design flaw cause by memory corruption error trigger privilege escalation. Furthermore it is running on Linux. Therefore exploit the design flaw through 3rd party API then triggers the vulnerability still have possibilities.