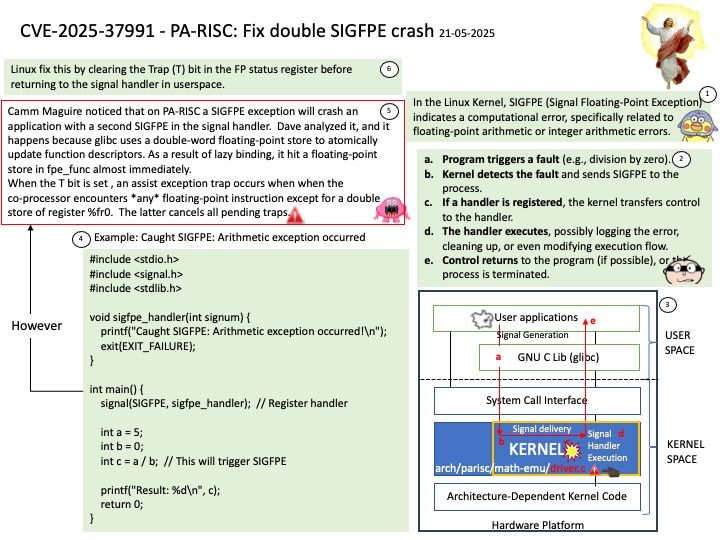
Preface: In the Linux Kernel, SIGFPE (Signal Floating-Point Exception) indicates a computational error, specifically related to floating-point arithmetic or integer arithmetic errors. This signal is triggered by events like floating-point overflow, underflow, or division by zero. While named “Floating-Point Exception,” it actually covers a broader range of arithmetic errors.
Background: What triggers SIGFPE?
- Floating-point errors: These include overflow (exceeding the maximum representable value), underflow (falling below the minimum non-zero value), and division by zero.
- Integer errors: Specifically, integer division by zero can also trigger SIGFPE.
How it works in the Linux Kernel:
- When a process encounters an arithmetic error that triggers SIGFPE, the kernel sends this signal to the process.
- By default, if a signal handler is not registered for SIGFPE, the process will be terminated.
- If a signal handler is registered, the handler can be used to attempt to recover from the error, such as by retrying the operation or taking alternative actions.
- The si_code field in a signal handler can provide more information about the specific type of arithmetic error that caused SIGFPE. For example, FPE_INTDIV indicates integer division by zero, according to a post on Stack Overflow.
Vulnerability details: Camm Maguire noticed that on PA-RISC a SIGFPE exception will crash an application with a second SIGFPE in the signal handler. Dave analyzed it, and it happens because glibc uses a double-word floating-point store to atomically update function descriptors. As a result of lazy binding, it hit a floating-point store in fpe_func almost immediately.
When the T bit is set , an assist exception trap occurs when when the co-processor encounters *any* floating-point instruction except for a double store of register %fr0. The latter cancels all pending traps.
Remedy: Linux fix this by clearing the Trap (T) bit in the FP status register before returning to the signal handler in userspace.
Official announcement: For details, please refer to the link –https://nvd.nist.gov/vuln/detail/CVE-2025-37991