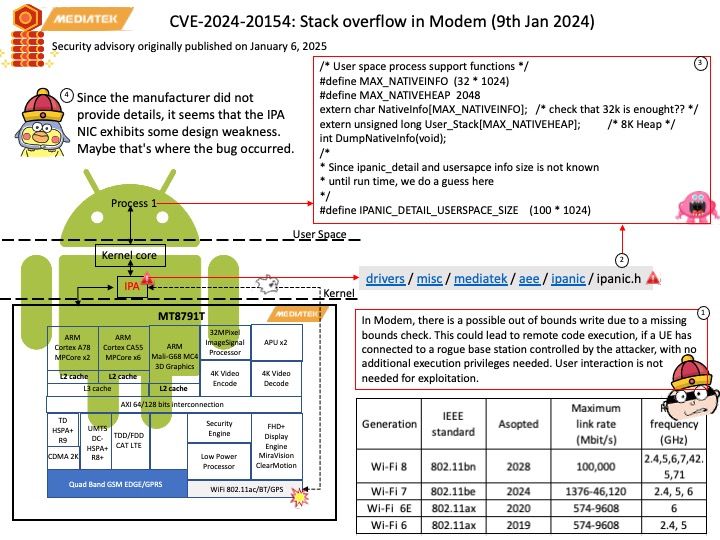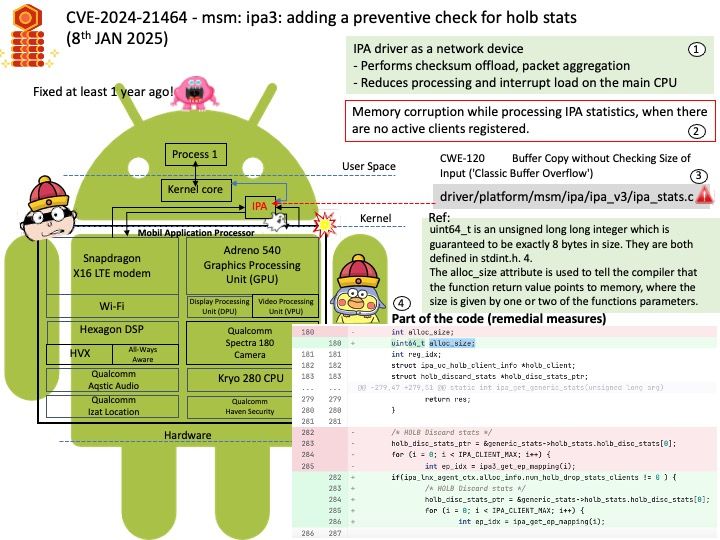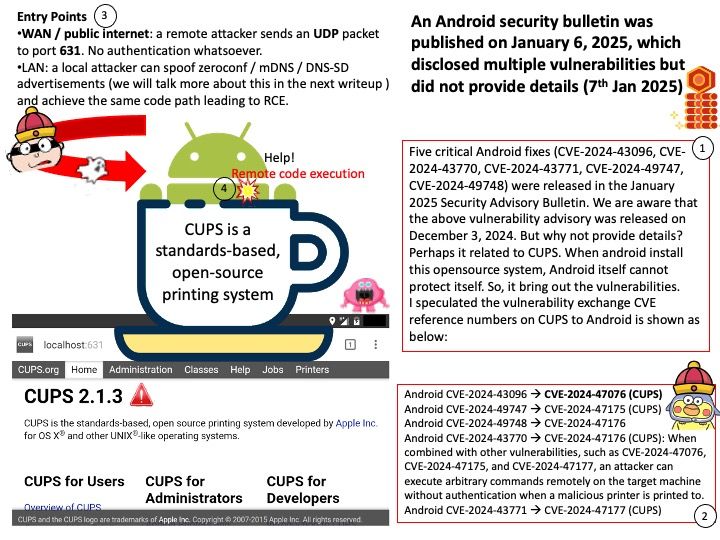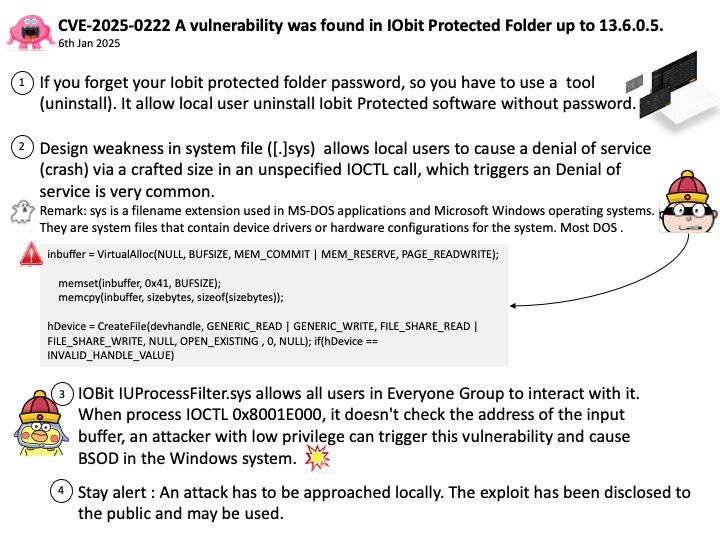
Preface: PowerVR is a division of Imagination Technologies (formerly VideoLogic) that develops hardware and software for 2D and 3D rendering, and for video encoding, decoding, associated image processing and DirectX, OpenGL ES, OpenVG, and OpenCL acceleration.
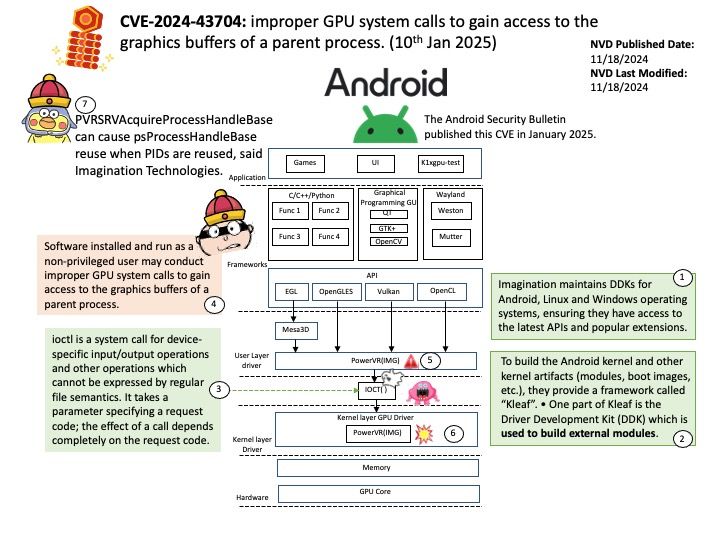
Background: Imagination maintains DDKs for Android, Linux and Windows operating systems, ensuring they have access to the latest APIs and popular extensions.
To build the Android kernel and other kernel artifacts (modules, boot images, etc.), they provide a framework called “Kleaf”. • One part of Kleaf is the Driver Development Kit (DDK) which is used to build external modules.
Vulnerability details: Software installed and run as a non-privileged user may conduct improper GPU system calls to gain access to the graphics buffers of a parent process.
PVRSRVAcquireProcessHandleBase can cause psProcessHandleBase reuse when PIDs are reused, said imagination Technologies.
Official announcement: Please refer to the link for details –
https://source.android.com/docs/security/bulletin/2025-01-01