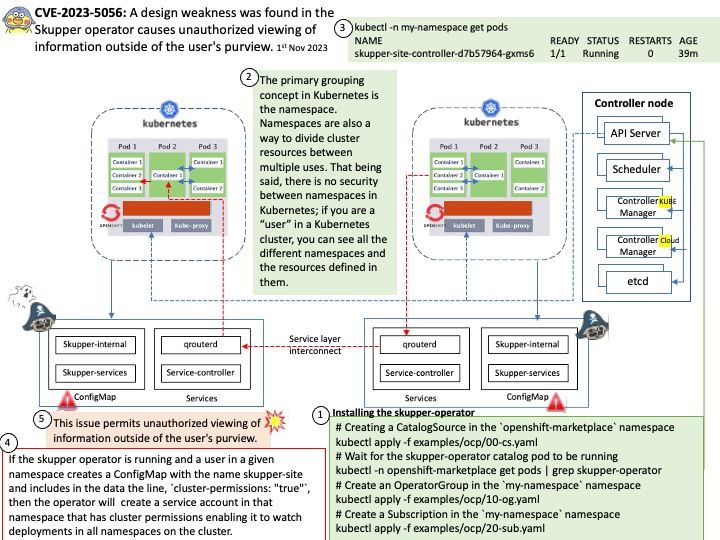
Preface: The payment systems based on a distributed architecture will be enhanced efficient and scalable. Therefore, distributed ledger technology (DLT) will become a trend in future. The DLT Pilot Regime defines “tokenization of financial instruments” as a process that involves the conversion of traditional financial asset classes into digital tokens that can be stored, transferred and traded on distributed ledgers. Apart from DLT, there is other option in the market. NATS makes it easy for applications to communicate by sending and receiving messages. These messages are addressed and identified by subject strings, and do not depend on network location. Data is encoded and framed as a message will be sent by a sender (original destination).
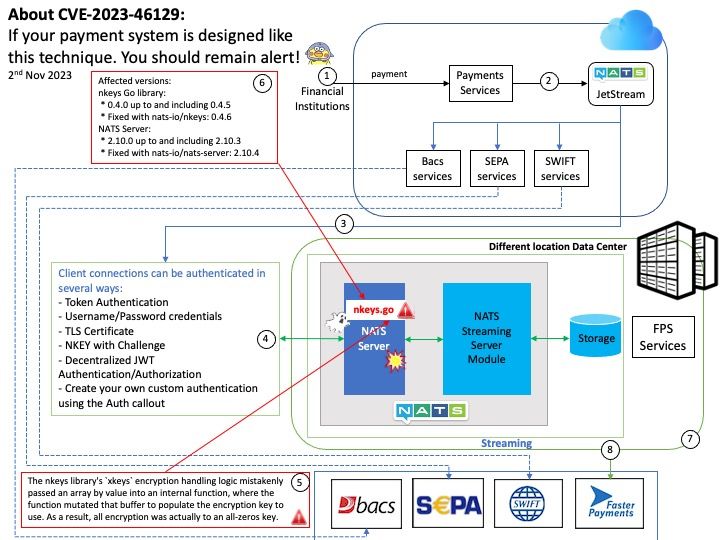
Background: NATS.io is a high performance open source pub-sub distributed communication technology, built for the cloud, on-premise, IoT, and edge computing. The cryptographic key handling library, nkeys, recently gained support for encryption, not just for signing/authentication. This is used in nats-server 2.10 (Sep 2023) and newer for authentication callouts. Vulnerability details: The nkeys library’s “xkeys” encryption handling logic mistakenly passed an array by value into an internal function, where the function mutated that buffer to populate the encryption key to use. As a result, all encryption was actually to an all-zeros key. This affects encryption only, not signing.
Within the nats-server, the encryption is used for the Auth Callouts feature, introduced with 2.10.0 (September 2023). The Auth Callout request includes the supplied user password. These messages are sent within NATS, and should typically be in a dedicated NATS Account used for callouts, but this is not required. Thus in scenarios where the Callouts are in an account shared with untrusted users or where the callout responders connect without TLS, this may lead to user credential exposure.
Affected versions:
nkeys Go library:
* 0.4.0 up to and including 0.4.5
* Fixed with nats-io/nkeys: 0.4.6
NATS Server:
* 2.10.0 up to and including 2.10.3
* Fixed with nats-io/nats-server: 2.10.4
Official announcement: Please refer to the link for details – https://advisories.nats.io/CVE/secnote-2023-02.txt