Preface: Government agencies and companies in emerging tech, finance, healthcare, and other industries use Red Hat® products and services. OpenShift gives organizations the ability to build, deploy, and scale applications faster both on-premises and in the cloud. It also protects your development infrastructure at scale with enterprise-grade security.
Background: Skupper is a layer 7 service interconnect. It enables secure communication across Kubernetes clusters with no VPNs or special firewall rules. With Skupper, your application can span multiple cloud providers, data centers, and regions. The Skupper Operator creates and manages Application Interconnect sites in Kubernetes. Skupper operator that simply produces the bundle and the index images. Its goal is to avoid introducing a new CRD, just relying on the site-controller to kick things off based on an existing skupper-site ConfigMap.
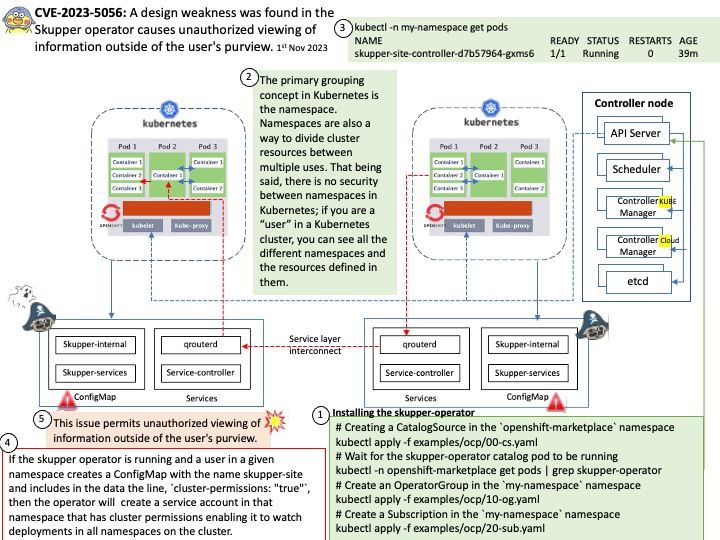
Ref: The primary grouping concept in Kubernetes is the namespace. Namespaces are also a way to divide cluster resources between multiple uses. That being said, there is no security between namespaces in Kubernetes; if you are a “user” in a Kubernetes cluster, you can see all the different namespaces and the resources defined in them.
Vulnerability details: A flaw was found in the Skupper operator, which may permit a certain configuration to create a service account that would allow an authenticated attacker in the adjacent cluster to view deployments in all namespaces in the cluster. This issue permits unauthorized viewing of information outside of the user’s purview.
Additional: If the skupper operator is running and a user in a given namespace creates a ConfigMap with the name skupper-site and includes in the data the line, `cluster-permissions: “true”`, then the operator will create a service account in that namespace that has cluster permissions enabling it to watch deployments in all namespaces on the cluster. This is the case even if the user creating that ConfigMap does not themselves have access to other namespaces.
Official announcement: Please refer to the link for details – https://access.redhat.com/errata/RHSA-2023:6219