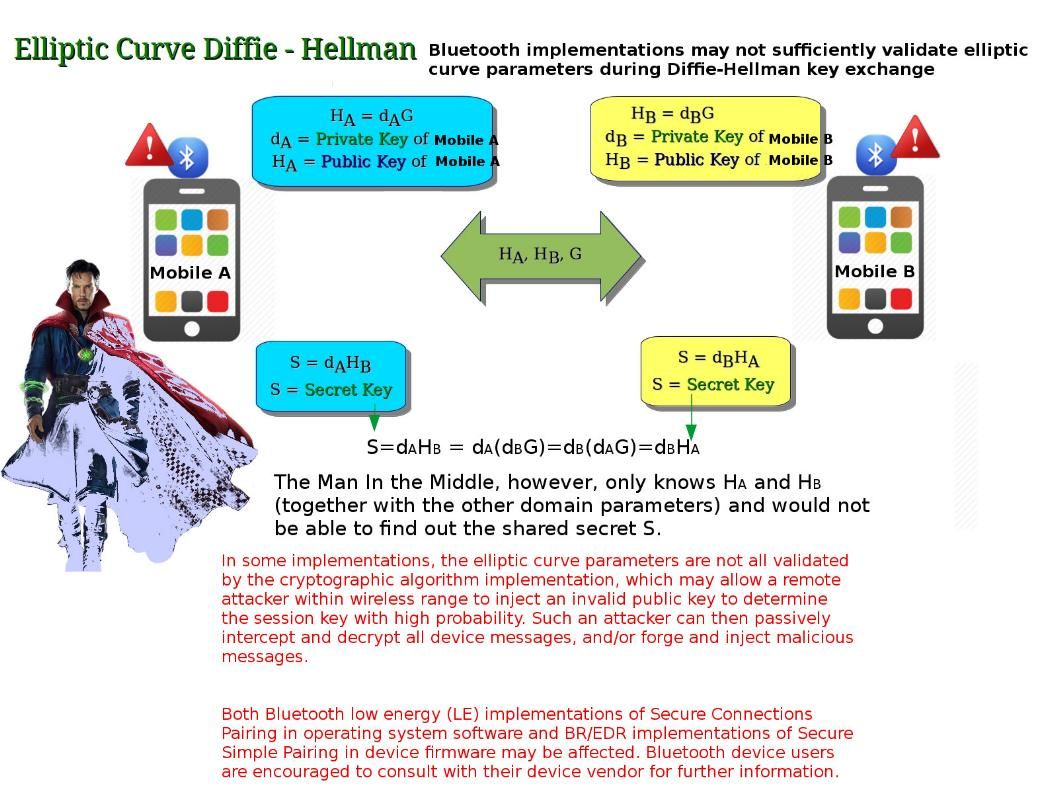
Elliptic Curve Diffie Hellman (ECDH) make man in the middle attack difficult since hacker would not be able to find out the shared secret and therefore it looks secure. The public keys are either static (and trusted, say via a certificate) or ephemeral (also known as ECDHE, where final ‘E’ stands for “ephemeral”). Ephemeral keys are temporary and not necessarily authenticated, so if authentication is desired, authenticity assurances must be obtained by other means. Authentication is necessary to avoid man-in-the-middle attacks. The truth is that similar type of setup has vulnerability occurs.Bluetooth implementations may not sufficiently validate elliptic curve parameters during Diffie-Hellman key exchange.
Reference: Vulnerability Note VU#304725 Bluetooth implementations may not sufficiently validate elliptic curve parameters during Diffie-Hellman key exchange – https://www.kb.cert.org/vuls/id/304725