Preface
When a child is born, his destiny is learning. He requires continuous learning the knowledge. His objective looks simple because his goal is survival.
What is the objective of AI (Artificial Intelligence)?
The aim of the development of AI it is to mimic in machines the “intelligent” behavior of humans.
The major element of AI (Artifical Intelligence). It is learning. The computer similar a baby, the world empower the knowledge to him. As a result, his learning path including human behaviour, human thinking logic, languages, decision making logic. But how does artificial intelligence do the correct decision not jeopardize the world? This is the ethics.
Does science world ignore the key element before A successful build?
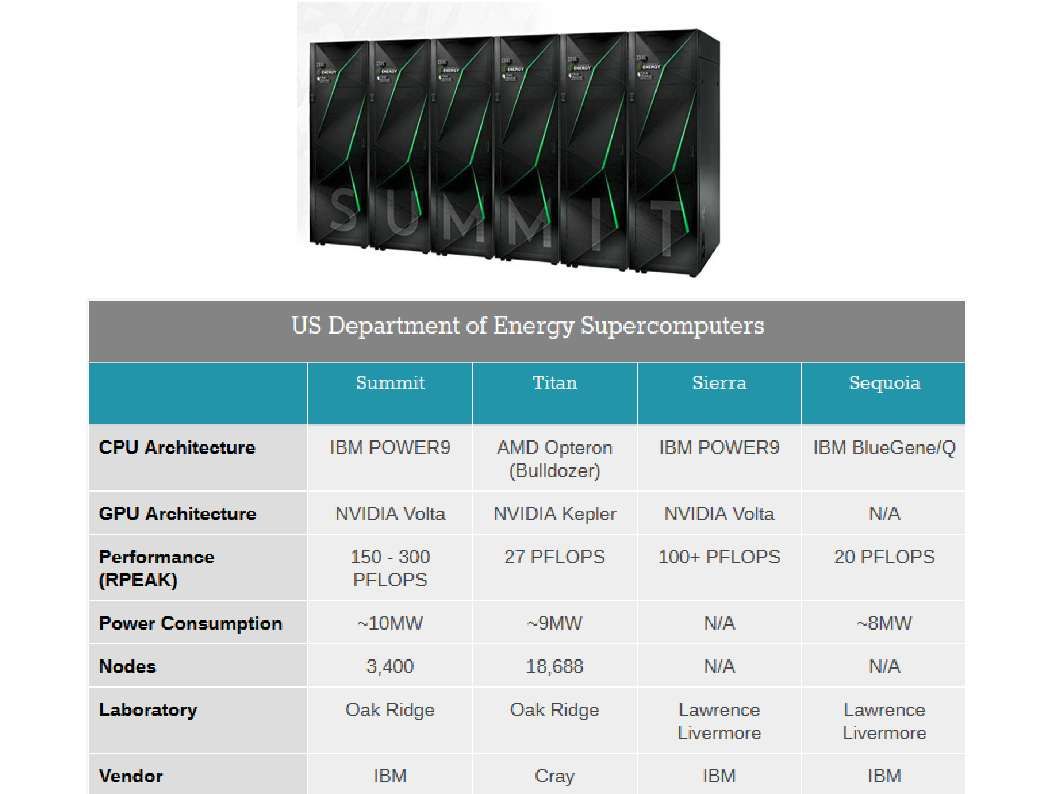
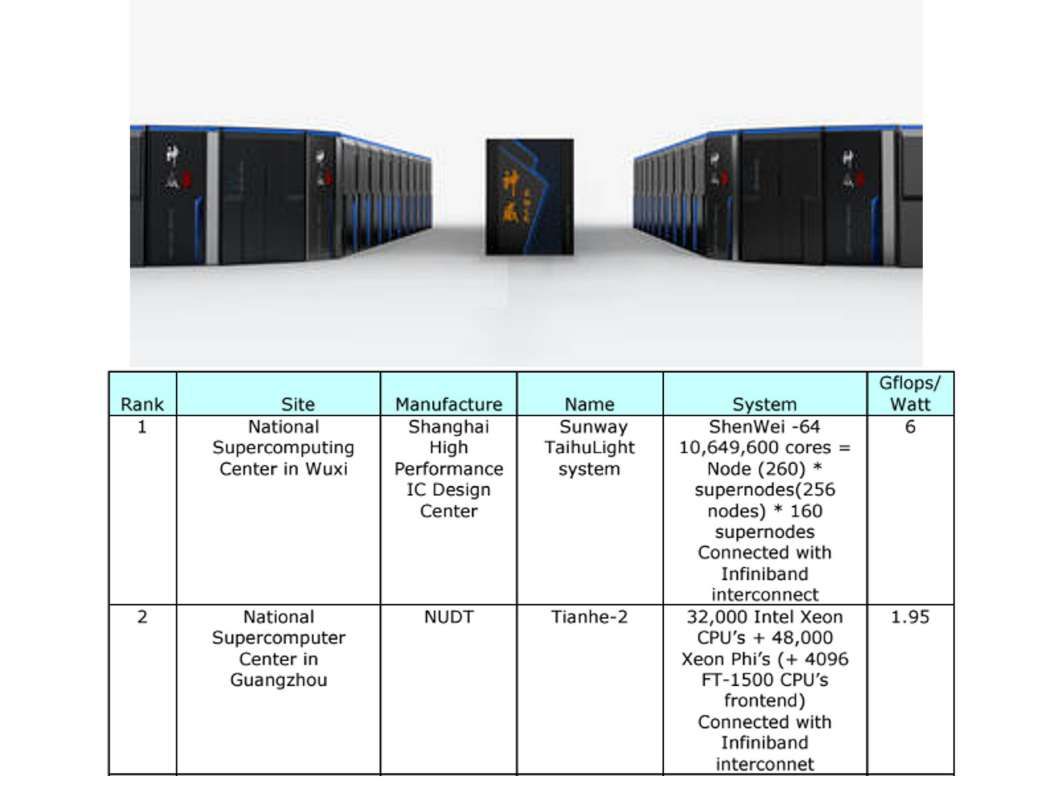
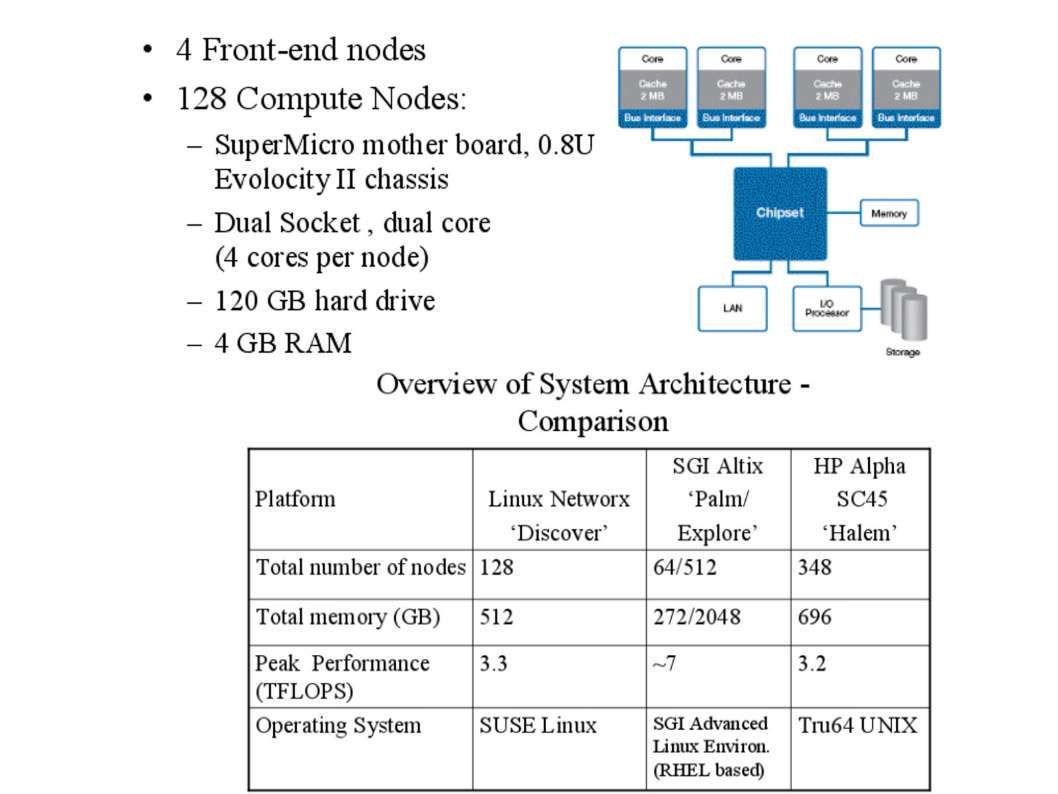
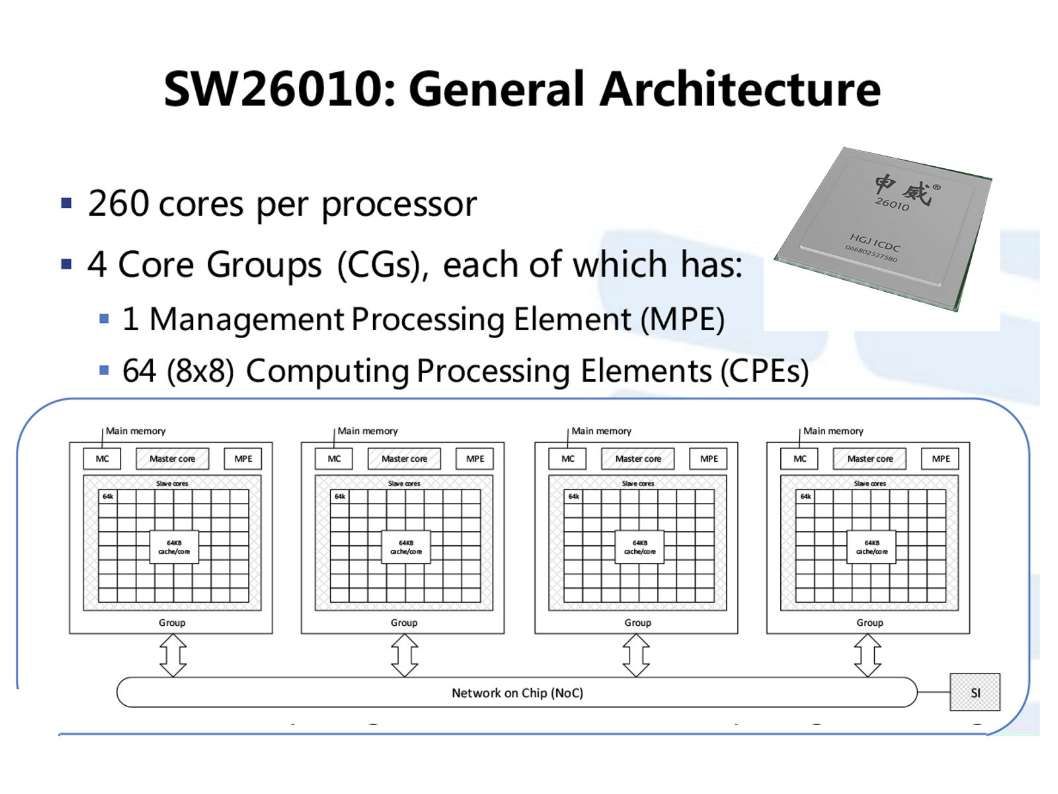
The super computer contains super processing power with high calulation speed. It is without difficulties to do the data analytic. But emulate a human logic thinking require huge volume of data set includes human behaviour data set, differect catagories of data, the historical of crime activities, business decisions logic,…etc.
Hey! Is there any contradition found on this place. For instance, a ethic will be bound to human logical thinking? For instance, you visit library to read the book. This is equilvant learning mode. But in the libray, the book could not contain personal data, personal behaviour acivities provides. So this is the classical learning mode.
You pick up sister or brother letter in the mail box. The ethics will guide you are not allow to open the letter, right? But why does the artificial intelligence have this privileges to read the personal data? The AI read the personal data without consent!
Intelligence is not bestowed by whom, but are the condition of each person is born with and enjoys. However the whole way is for human survival in the earth. If machine contains artifical intelligence. From techincal point of view, it looks like human build a new competitor for himself? The major point is that AI will be wind their way to survivail in the world once their technology is mature.
I am not speaking the conspiracy. It is reality since they are in the machine learning phase. Their evolutions are shown as below:

1st Generation
Data science: Data science is an interdisciplinary field that uses scientific methods, processes, algorithms and systems to extract knowledge and insights from data in various forms, both structured and unstructured,similar to data mining.
2nd Generation
Machine learning: Machine learning is a subset of artificial intelligence in the field of computer science that often uses statistical techniques to give computers the ability to “learn”.
Final stage
Artifical intelligence: Artifical intelligence is intelligence demonstrated by machines, in contrast to the natural intelligence (NI) displayed by humans and other animals.
Source of data of machine learning nowadays
Datasets of population, economic and development across the world: https://data.worldbank.org/
Data operate in educational institutions and education demographics from the US and around the world: https://nces.ed.gov/
The collection of social, economic and population data in UK: https://www.ukdataservice.ac.uk/
The national crime statistics, with free data available at national, state and county level: https://ucr.fbi.gov/
Information gathered by NASA’s space exploration missions: https://exoplanetarchive.ipac.caltech.edu/
Conclusion

Human pollute the world because of living standard growth and modern industries.
Artificial intelligence in final phase will be …..
A song is on the way!
Don’t kill the world, don’t let it down. Do not destroy basic ground…..
–End–