Somewhere in time. This is 2015 – BlackEnergy2 exists in the form of a kernel-mode driver, which makes it harder for network administrators to discover the compromise. Black energy Group will mimics their custom tool(driver) thus made to look like a normal Windows component. They are interested in infecting Windows servers especially OPC server. But Microsoft implemented a driver signing policy in order to avoid loading unsigned driver. This feature is enabled on 64 bits versions of Windows systems.
Synopsis: In normal circumstances, activate the function of the cyber espionage and information destruction attack features needed to be rebooted in order to start the mimics driver. Even though black energy do not have exception.This unplanned reboot of the Windows server could raise suspicion. To solve the reboot issue, the attackers started to use a tool called DSEFix (an open-source tool that exploits CVE-2008-3431, a vulnerability in the legitimate VirtualBox driver), in order to disable the driver signature check. The attackers will made a custom version of DSEFix that also modifies boot configuration data (BCD) in order to enable TESTSIGNING mode.
What is TESTSIGNING mode: By default, Windows does not load test-signed kernel-mode drivers. To change this behavior and enable test-signed drivers to load, use the boot configuration data editor, BCDEdit.exe, to enable or disable TESTSIGNING, a boot configuration option. You must have Administrator rights to enable this option.
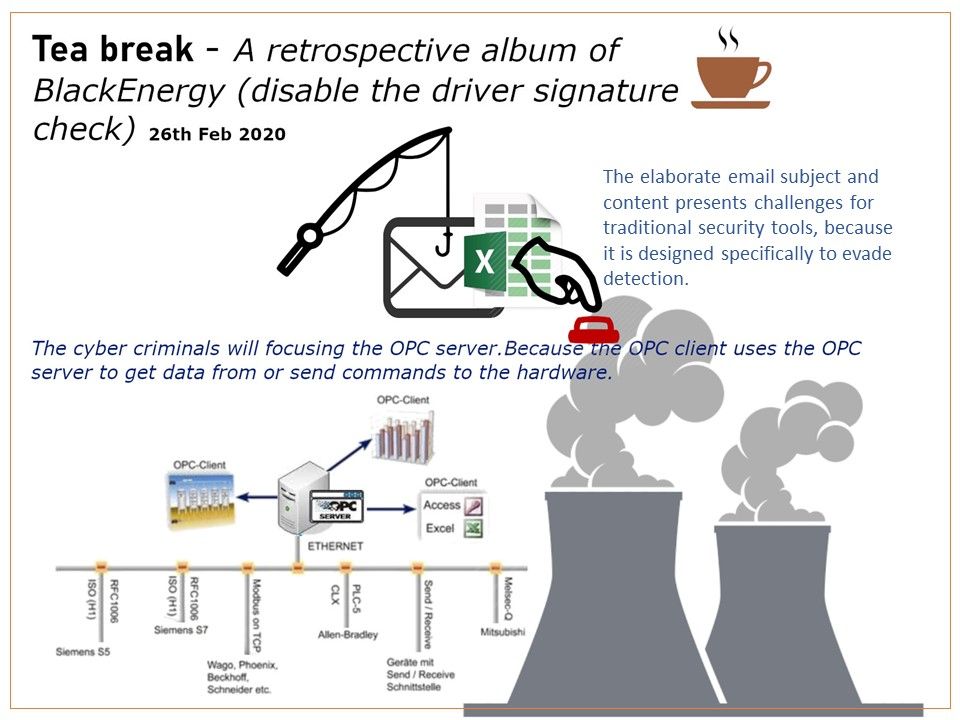
Those cyber criminal will focusing the OPC server.Because the OPC client uses the OPC server to get data from or send commands to the hardware.
Will it happen today? The elaborate email subject and content presents challenges for traditional security tools, because it is designed specifically to evade detection.