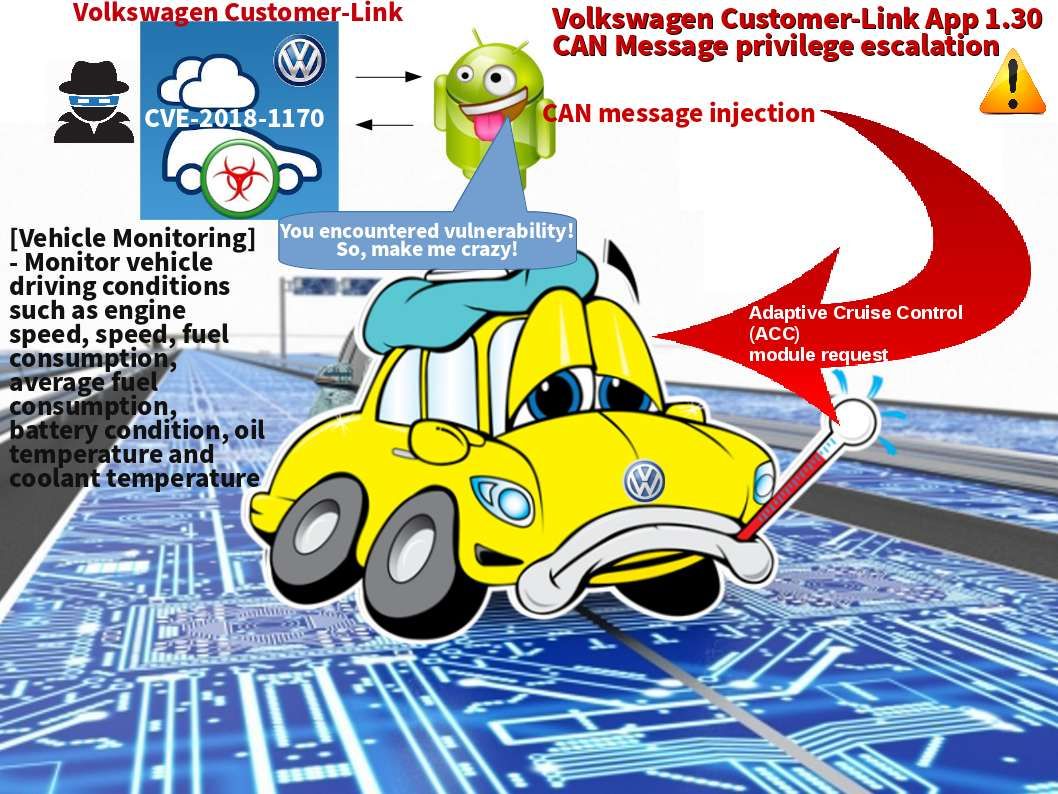
Auto Pilot system has been implemented in many countries. Perhaps Auto Pilot function enabled become a hot topic. You are allow to install mobile apps on your Android phone keep track the status of your car. We are really appreciate for Controller Area Network (CAN bus) technology assistance. The vulnerability found on car automation not surprising the world. Since this is a computer technology. The design flaw found on Android App this round belongs to Volkswagen.An attacker can leverage this vulnerability to inject CAN messages. How does it work?
The messages sent seem to fall into one of three categories. One is informative. The other type of message is one requesting action of another ECU (Electronic Control Units). The final type of message is diagnostic. For details, please refer below url for reference.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-1170
Is this the cost we are going to pay for automation world?