Preface: Flaws that require root access are not considered security issues in existing policy. If we are not using cloud computing concept. It is acceptable. But we need cloud system!
Security focus: Turkish information security specialist found a design weakness in Windows kernel design. According to the vendor’s Bug Bounty program rules, flaws that require root access are not considered security issues and are not classified as vulnerabilities. However our the whole IT world in the trend of cloud technology. It is hard to guarantee similar type of vulnerability will be impact the public cloud farm. Perhaps it might have possibility to do a re-engineering become as a Surveillance tool.
Defect details: An PoC tool proof that it can hijacks the HalPrivateDispatchTable table to create a early-bugcheck hook. Utilizing this early-bugcheck hook it collects information about the exception and basically provides a simple interface to register a high-level system-wide exception handler. My intention is going to urge Microsoft should be consider this technical issue. Perhaps it may become a zero-day. So I do not display related url.Should you have interested of this topic, not difficult to do a search. You will find the details.
Reference:
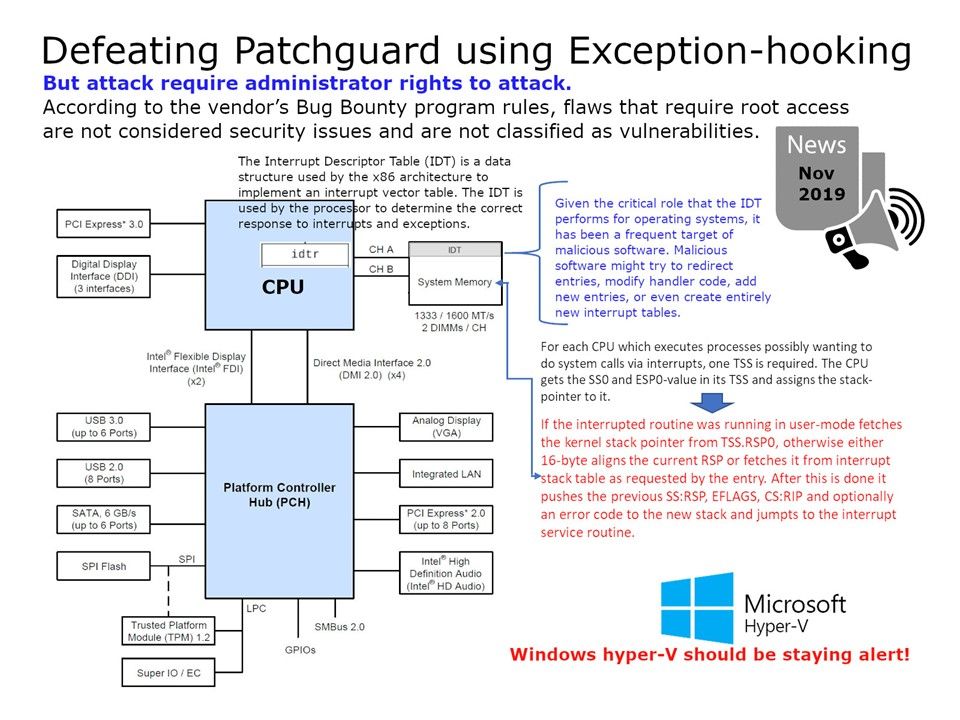
The ntoskrnl.exe kernel service, which is responsible for handling exceptions, system call procedures, and thread scheduling in Windows.
Kernel Patch Protection (KPP), informally known as PatchGuard, is a feature of 64-bit (x64) editions of Microsoft Windows that prevents patching the kernel.
Fundamental design concept – related to this matter:
- RSPx is loaded in whenever an interrupt causes the CPU to change PL to x. The TSS in long mode also holds the Interrupt Stack Table, which is a table of 7 known good stack pointers that can be used for handling interrupts.
- BKPT #0x3 ; Breakpoint with immediate value set to 0x3 (debugger can ; extract the immediate value by locating it using the PC- (program counter))
- x86_64 also has a feature which is not available on i386, the ability to automatically switch to a new stack for designated events such as double fault or NMI, which makes it easier to handle these unusual events on x86_64. This feature is called the Interrupt Stack Table (IST). There can be up to 7 IST entries per CPU. The IST code is an index into the Task State Segment (TSS). The IST entries in the TSS point to dedicated stacks; each stack can be a different size.
This topic is under our observation.