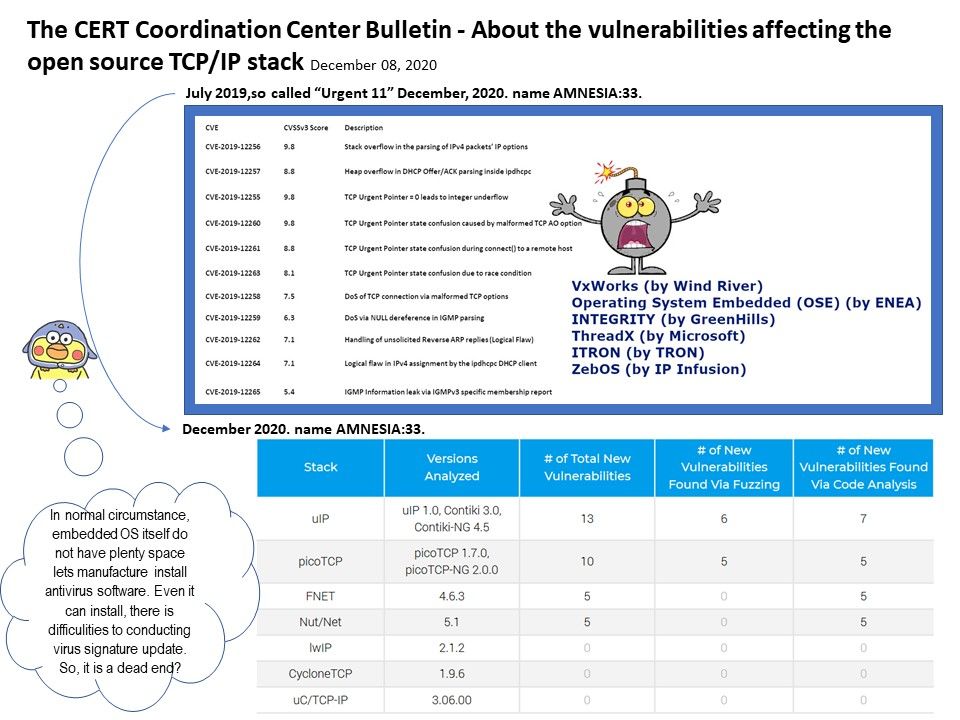
Preface: October 1, 2019 – A security firm has identified 11 vulnerabilities, named “URGENT/11.
Background: TCP/IP stack was developed using subset of the ‘C’ language. The open source TCP/IP stack design is widely used in embedded systems in the market. Briefly describe it as an IoT device. It runs in your business environment and in your home. In addition, Smart City is using them. Open Source implementations includes uIP,LwIP,uC/IP,tinytcp, wattcp and BSD 4.4. Furthermore, the commnerical implementations will be covered CMX-tcp-/ip, NetX, NicheStack, ARC RTCS TCP/IP, RTXC Quadnet TCP/IP, TargetTCP and uc/TCP-IP.
Traditional embedded OS memory Footprint – RAM requirements can vary widely depending on application needs but are typically as low as 12kB. It is possible, with a minimum configuration UDP application,
to use less than 5kB of ROM and a few hundred bytes of RAM (plus network buffers).
Limitation: In normal circumstance, embedded OS itself do not have plenty space lets manufacture install antivirus software. Even it can install, there is difficulties to conducting virus signature update. So, it is a dead end?
Reader space: vulnerabilities make experts worry about this. For more details, please refer to link – https://www.kb.cert.org/vuls/id/815128