Preface: The popularity of NFC mobile payments is owed to its ease of use and improved security options. Near-field communication (NFC) enables smartphones to exchange data and function as a payment device. It stores the customer’s credit card details and allows the user to pay at NFC POS terminals through smartphones.
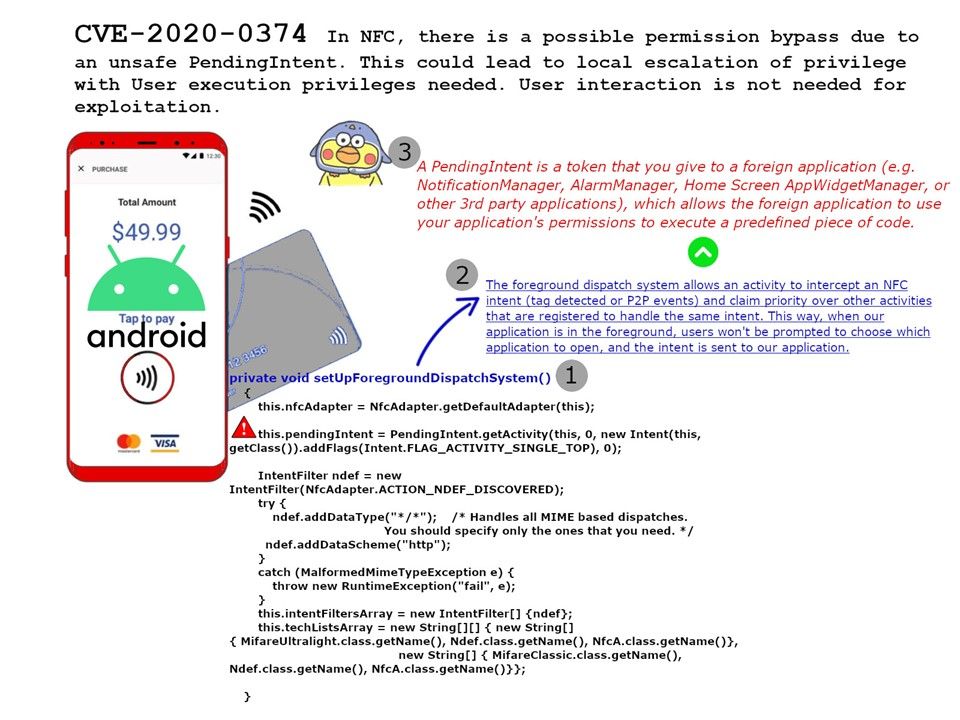
Vulnerability details: In NFC, there is a possible permission bypass due to an unsafe “PendingIntent”. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitation.
By giving a “PendingIntent” to another application, you are granting it the right to perform the operation you have specified as if the other application was yourself (with the same permissions and identity). As such, you should be careful about how you build the “PendingIntent”: almost always, for example, the base Intent you supply should have the component name explicitly set to one of your own components, to ensure it is ultimately sent there and nowhere else.
Reference: A PendingIntent is a token that you give to a foreign application (e.g. NotificationManager, AlarmManager, Home Screen AppWidgetManager, or other 3rd party applications), which allows the foreign application to use your application’s permissions to execute a predefined piece of code.
Affected products: AndroidVersions – Android-11Android ID: A-156251602
CVE reference: https://nvd.nist.gov/vuln/detail/CVE-2020-0374