Preface: Technology cannot fight against coronavirus in the moment.
Easter, commemorating the resurrection of Jesus from the dead.
Wish that human can managed to fight it all. Comparing with coronavirus. The vulnerability in computer system looks easy resolve.
Security focus – Juniper Network product:
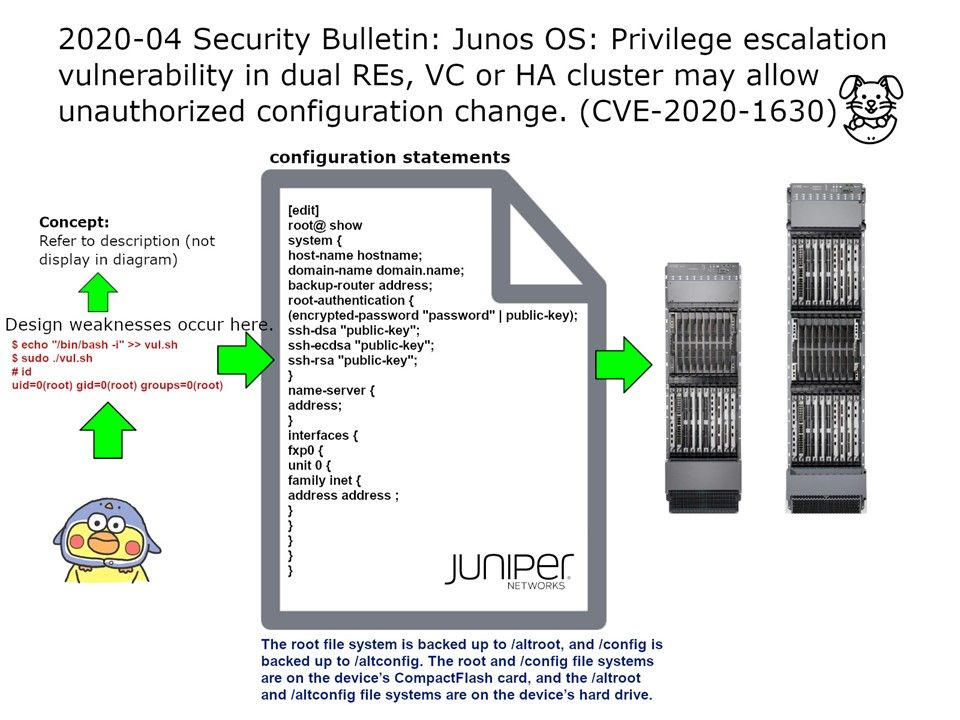
A privilege escalation vulnerability in Juniper Networks Junos OS devices configured with dual Routing Engines (RE), Virtual Chassis (VC) or high-availability cluster may allow a local authenticated low-privileged user with access to the shell to perform unauthorized configuration modification. This issue does not affect Junos OS device with single RE or stand-alone configuration.
My observation: Refer to attach diagram, below is the information for supplement.
Fundamental
/bin/sh is an executable representing the system shell. Actually, it is usually implemented as a symbolic link pointing to the executable for whichever shell is the system shell.
Since it is a bash file so commands inside it will get executed, and if we execute the file as root, then all the commands inside it will also get executed as root. So, let’s take advantage of that and append /bin/bash -i to the file. This will execute bash as root, which in turn will open the root shell.
Official announcement of this matter (JunOS vulnerability) – https://kb.juniper.net/InfoCenter/index?page=content&id=JSA11010&cat=SIRT_1&actp=LIST