Security Focus: CVE-2020-36558 appears in this patch. Do you have interest to know the details?
Preface: A NULL pointer dereference occurs when the application dereferences a pointer that it expects to be valid, but is NULL, typically causing a crash or exit.
Background: RHEL 8.6 includes a wide range of new features and enhancements . Primary features and benefits:
i.Mitigate potential risks across the hybrid cloud – Web console support for Smart Card Authentication with Sudo and SSH to use smart card authentication credentials when performing administrative functions and accessing remote hosts through the RHEL web console.
ii.Support for SAP HANA in production with Red Hat and SAP, a jointly-tested RHEL configuration with SELinux enabled. SELinux’s security technology allows process isolation, offering great privilege escalation attack mitigation to SAP users.
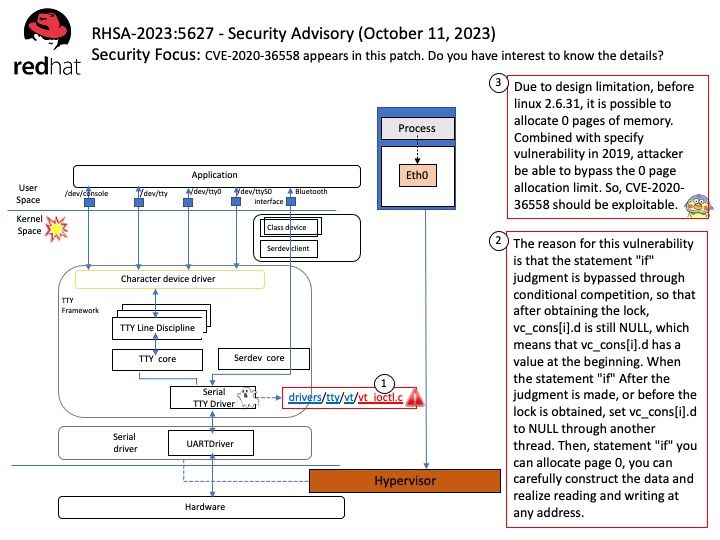
Vulnerability details: CVE-2020-36558 – kernel: race condition in VT_RESIZEX ioctl when vc_cons[i].d is already NULL leading to NULL pointer dereference
Synopsis: The reason for this vulnerability is that the statement “if” judgment is bypassed through conditional competition, so that after obtaining the lock, vc_cons[i].d is still NULL, which means that vc_cons[i].d has a value at the beginning. When the statement “if” After the judgment is made, or before the lock is obtained, set vc_cons[i].d to NULL through another thread. Then, statement “if” you can allocate page 0, you can carefully construct the data and realize reading and writing at any address.
Due to design limitation, before linux 2.6.31, it is possible to allocate 0 pages of memory. Combined with specify vulnerability in 2019, attacker be able to bypass the 0 page allocation limit. So, CVE-2020-36558 should be exploitable.
Ref: The ‘if’ Statement: The basic syntax of the if statement looks like this: if (condition) { // code to be executed if the condition is true; }.
Official announcement: Please refer to the link for details – https://access.redhat.com/errata/RHSA-2023:5627