Preface: If application do not defenses against directory traversal attacks, so an attacker can request the following URL: hxxp://xxx[.]com/loadImage?filename=../../../etc/passwd
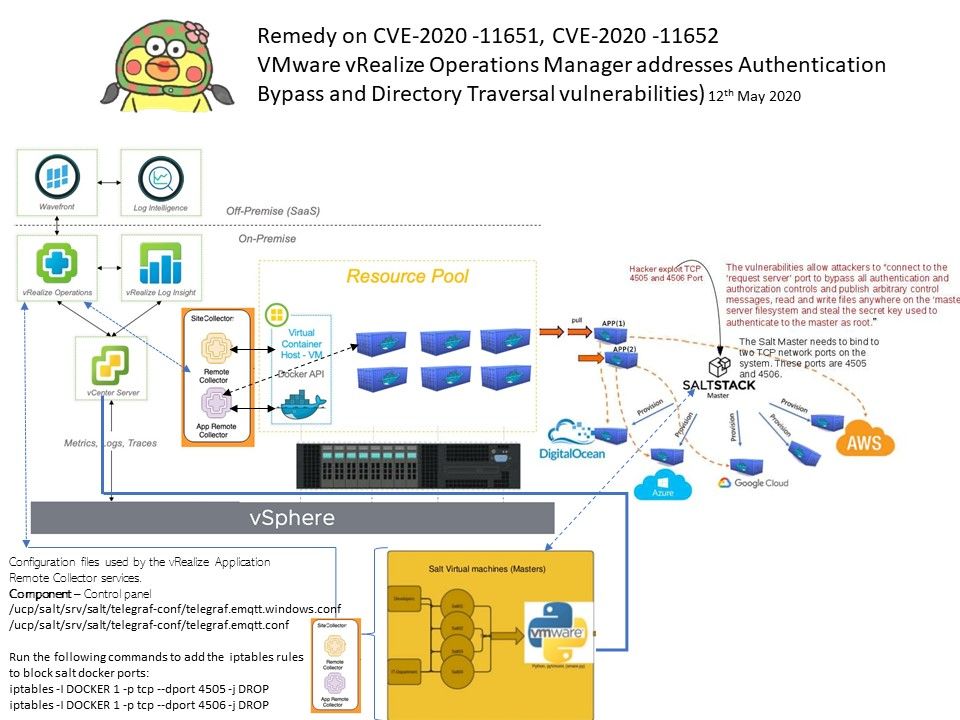
Vulnerability details: The VMware Application Remote Collector (ARC) introduced with vRealize Operations Manager 7.5 can integrate with Salt (SaltStack). However the vulnerabilities (CVE-2020-11651 and CVE-2020-11652) found in saltstack this month will be impact VMware operation simultaneously. The impact causes by SaltStack causes VMware vRealize Operations Manager (vROps) vulnerable to Directory traversal vulnerability. Meanwhile it has possiblites to happen critical impact (authentication bypass). For details, please refer to follow official announcement url. https://kb.vmware.com/s/article/79031
Observation: From technical point of view, the design weakness of salt open TCP port 4505 and 4506 on behalf of service daemon. So attacker can be inject command in this part without authentication.