Preface: Complex data queries not to use Redis as a Database.
Big data and the new phenomenon open data are closely related but they’re not the same. Open data is information that is available to the public, regardless of its intended purpose.
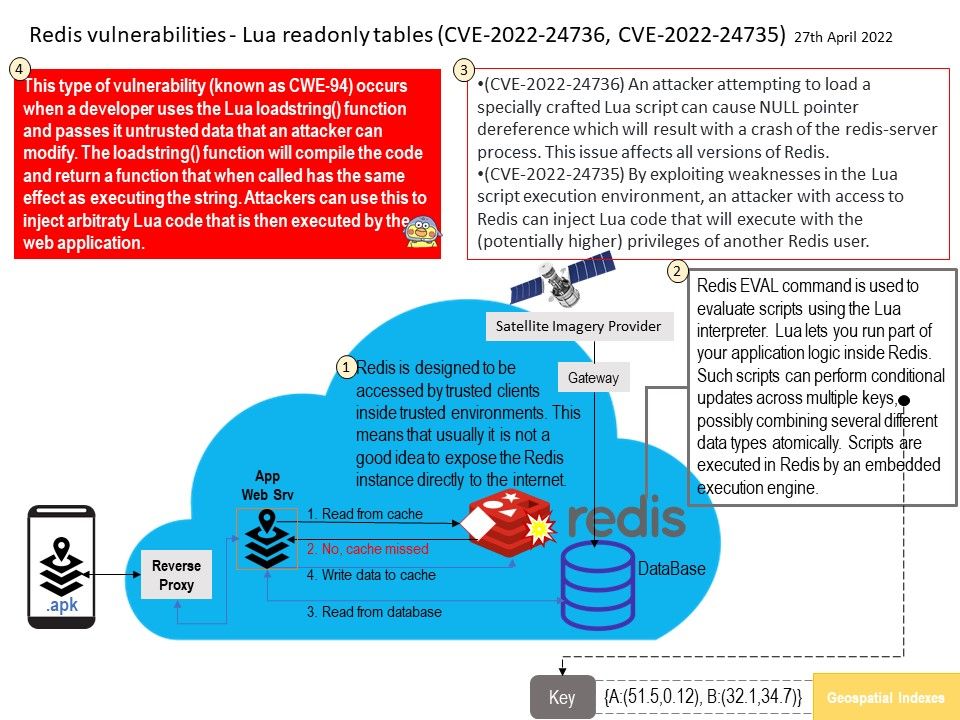
Background: Redis is designed to be accessed by trusted clients inside trusted environments. This means that usually it is not a good idea to expose the Redis instance directly to the internet. Redis is an in-memory database that persists on disk. It can be used as a distributed cache, which is probably its most common and popular use case, as a NoSQL Database and as a Message broker (pub\sub mode, similar to Kafka or RabbitMQ).
Redis EVAL command is used to evaluate scripts using the Lua interpreter. Lua lets you run part of your application logic inside Redis. Such scripts can perform conditional updates across multiple keys, possibly combining several different data types atomically. Scripts are executed in Redis by an embedded execution engine.
Vulnerability details:
(CVE-2022-24736) An attacker attempting to load a specially crafted Lua script can cause NULL pointer dereference which will result with a crash of the redis-server process. This issue affects all versions of Redis.
(CVE-2022-24735) By exploiting weaknesses in the Lua script execution
environment, an attacker with access to Redis can inject Lua code that will execute with the (potentially higher) privileges of another Redis user.
By exploiting weaknesses in the Lua script execution environment, an attacker with access to Redis prior to version 7.0.0 or 6.2.7 can inject Lua code that will execute with the (potentially higher) privileges of another Redis user.
Ref: This type of vulnerability (known as CWE-94) occurs when a developer uses the Lua loadstring() function and passes it untrusted data that an attacker can modify. The loadstring() function will compile the code and return a function that when called has the same effect as executing the string. Attackers can use this to inject arbitraty Lua code that is then executed by the web application.
Several weaknesses of these measures have been publicly known for a long time.
Official announcement: Please refer to the link for details – https://github.com/redis/redis/pull/10651
Remedy: The problem is fixed in Redis versions 7.0.0 and 6.2.7. An additional workaround to mitigate this problem without patching the redis-server executable, if Lua scripting is not being used, is to block access to SCRIPT LOAD and EVAL commands using ACL rules.