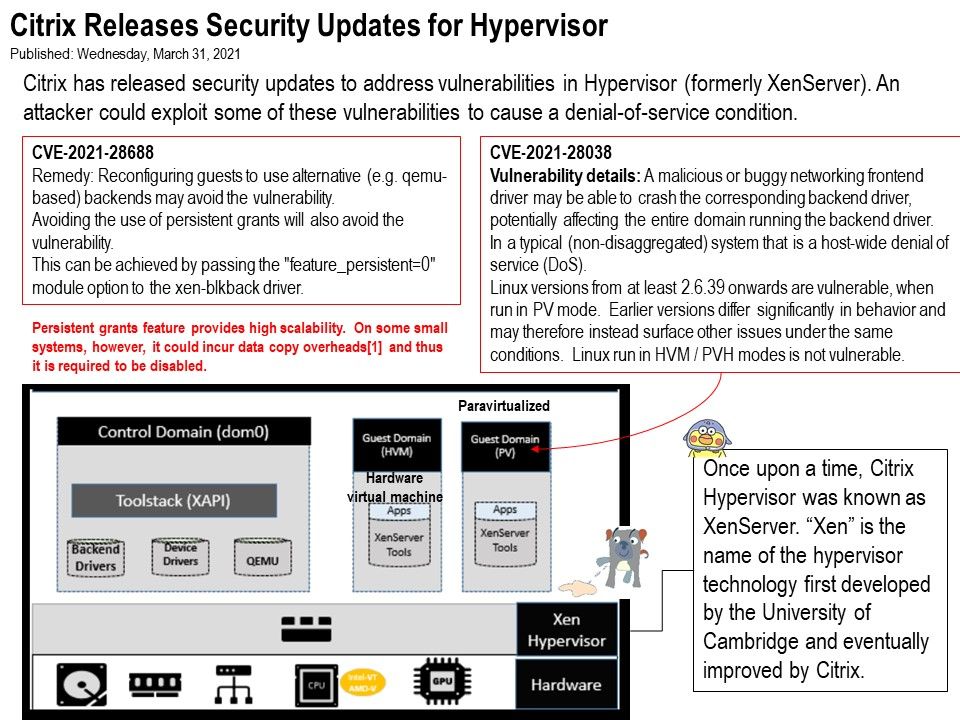
Preface: Once upon a time, Citrix Hypervisor was known as XenServer. “Xen” is the name of the hypervisor technology first developed by the University of Cambridge and eventually improved by Citrix.
Background:
Recommendation 1: It is recommended to use paravirtualized devices instead of emulated devices for virtual machines running I/O intensive applications.
Recommendation 2: Persistent grants feature provides high scalability. On some small systems, however, it could incur data copy overheads and thus it is required to be disabled.
Vulnerability details:
CVE-2021-28688 An attacker with the ability to execute privileged mode code in a guest can perform a denial of service attack against the host. Avoiding the use of persistent grants will also avoid the vulnerability. This can be achieved by passing the “feature_persistent=0” module option to the xen-blkback driver.
CVE-2021-28038 An attacker with the ability to execute privileged mode code in a guest can perform a denial of service attack against the host. Linux versions from at least 2.6.39 onwards are vulnerable, when run in PV mode. Earlier versions differ significantly in behavior and may
therefore instead surface other issues under the same conditions. Linux
run in HVM / PVH modes is not vulnerable.
Official details: Two security issues have been identified in Citrix Hypervisor – https://support.citrix.com/article/CTX306565