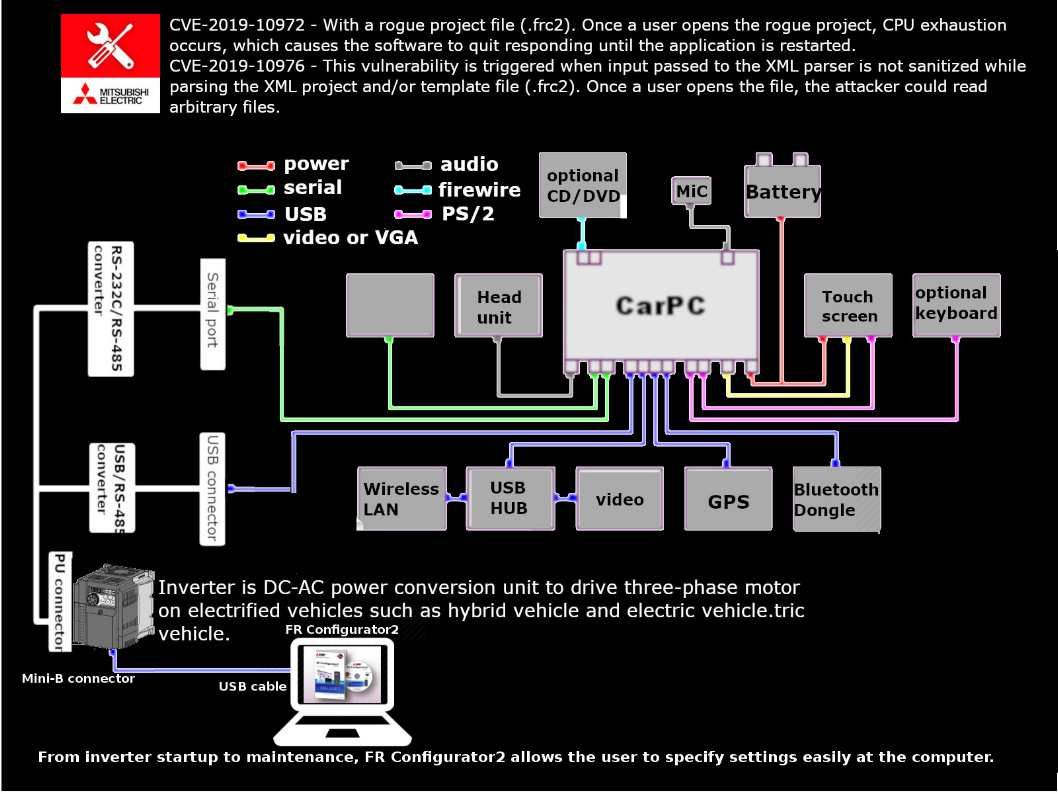
Preface: Internet of Vehicles (IoV) growth rapidly, meanwhile they are also the potential target of the cyber attacker.
About Mitsubishi Electric FR Configurator2: From inverter startup to maintenance, FR Configurator2 allows the user to specify settings easily at the computer.
Vulnerability details:
CVE-2019-10976 – This vulnerability is triggered when input passed to the XML parser is not sanitized while parsing the XML project and/or template file (.frc2). Once a user opens the file, the attacker could read arbitrary files.
CVE-2019-10972 – This vulnerability can be triggered when an attacker provides the target with a rogue project file (.frc2). Once a user opens the rogue project, CPU exhaustion occurs, which causes the software to quit responding until the application is restarted.
Our comment – The impact of these vulnerabilities depends on the source of the infection. If malicious project file (.frc2) send with large scale of scam email. Because of the software design weakness (XML parser is not sanitized while parsing the XML project). Refer to attached infographic, perhaps it will provide a way to attacker exploit malware to infect the car CPU. Because the interconnect in between Car CPU and inverter is USB. So we must stay alert of these vulnerabilities.