Preface: Since we have virtual machines, memory management is more difficult to manage. Maybe you disagree. Yes, in theory, the effective memory type is determined by the PAT entry value and the MTRR value.
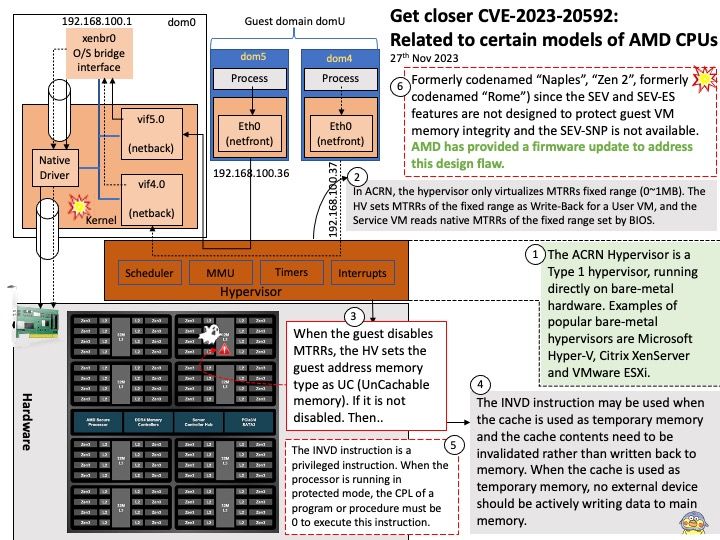
Background: The hypervisor (HV) virtualizes real physical memory so an unmodified OS (such as Linux or Android) that is running in a virtual machine can manage its own contiguous physical memory. The ACRN Hypervisor is a Type 1 hypervisor, running directly on bare-metal hardware. Examples of popular bare-metal hypervisors are Microsoft Hyper-V, Citrix XenServer and VMware ESXi. In ACRN, the hypervisor only virtualizes MTRRs fixed range (0~1MB). The HV sets MTRRs of the fixed range as Write-Back for a User VM, and the Service VM reads native MTRRs of the fixed range set by BIOS.
The INVD instruction is a privileged instruction. When the processor is running in protected mode, the CPL of a program or procedure must be 0 to execute this instruction.
Vulnerability details: Improper or unexpected behavior of the INVD instruction in some AMD CPUs may allow an attacker with a malicious hypervisor to affect cache line write-back behavior of the CPU leading to a potential loss of guest virtual machine (VM) memory integrity.
Mitigation:
No mitigation is available for the first or second generations of EPYC™ processors (“Zen 1”, formerly codenamed “Naples”, “Zen 2”, formerly codenamed “Rome”) since the SEV and SEV-ES features are not designed to protect guest VM memory integrity and the SEV-SNP is not available.
As a mitigation for the potential vulnerability, AMD has provided a hot-loadable microcode patch and updated the firmware image for AMD 3rd generation EPYC™ processors (“Zen 3” microarchitecture, formerly codenamed “Milan”) for customers with the AMD Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) feature enabled. No performance impact is expected from the patch.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-20592