Preface: The security of FIDO deployment largely depends on the choice of underlying security subsystems and their implementation.
Background: An ioctl , which means “input-output control” is a kind of device-specific system call. There are only a few system calls in Linux (300-400), which are not enough to express all the unique functions devices may have. So a driver can define an ioctl which allows a userspace application to send it orders.
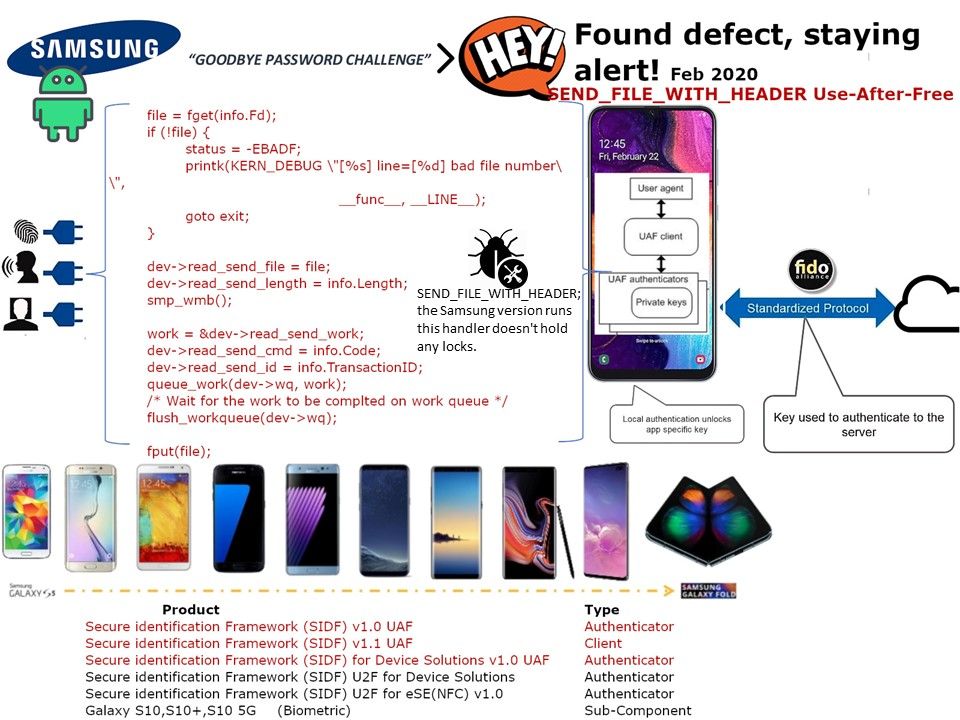
Samsung’s kernel tree contains two implementations of device-side MTP. One of them (drivers/usb/gadget/function/f_mtp.c), based on its copyright headers,seems to be from Google, but this one is disabled at build time.
The second one is drivers/usb/gadget/function/f_mtp_samsung.c.
Both of them have ioctl handlers that handle the ioctl command SEND_FILE_WITH_HEADER; the Google version runs this handler under a lock, but Samsung version doesn’t hold any locks.
Impact: If the object has been freed and then filled with data controlled by attacker, the EIP/RIP register for x86/x64 architecture or the register for ARM architecture is to be hijacked to injected shellcode and an arbitrary code execution in kernel will be achieved.
Remedy: Waiting for response by vendor