Preface: The Citrix ADC NITRO protocol allows you to configure and monitor the Citrix ADC appliance programmatically by using
Representational State Transfer (REST) interfaces. Therefore, NITRO applications can be developed in any programming language.
Additionally, for applications that must be developed in Java or .NET or Python, NITRO APIs are exposed through relevant libraries
that are packaged as separate Software Development Kits (SDKs).
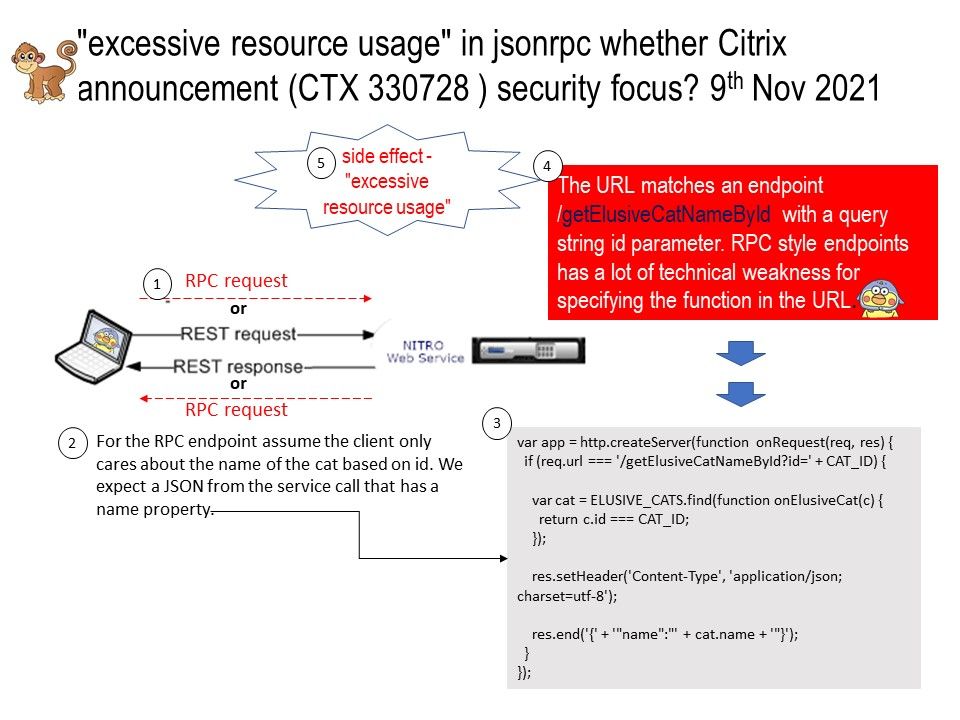
Background: When it comes to network services, you can use remote procedure calls (RPC) and representational state transfer (REST) to create APIs for network communication. As with any programming problem, understanding the advantages of each method will help you choose the best solution to reduce technically unforeseen problems. Are you experienced “excessive resource usage” in jsonrpc technical matter? For more information on this matter, please refer to the attached picture. In addition, do you think the security focus of the Citrix announcement (CTX 330728) is on similar topics?
Vulnerability details:
CVE-2021-22955 – Unauthenticated denial of service
Affected Products – Citrix ADC, Citrix Gateway (Appliance must be configured as a VPN (Gateway) or AAA virtual server)
Possible cause: Uncontrolled Resource Consumption
Criticality – Critical
CVE-2021-22956 – Temporary disruption of the Management GUI, Nitro API and RPC communication
Affected Products: Citrix ADC, Citrix Gateway, Citrix SD-WAN WANOP Edition (Access to NSIP or SNIP with management interface access)
Possible cause: Uncontrolled Resource Consumption
Criticality – Critical
Official announcement – https://support.citrix.com/article/CTX330728