Published: 2025-08-28
Updated: 2025-08-28
Preface: Credentials stores are common, largely due to SAML. SAML’s effectiveness stems from centralizing authentication and authorization, allowing a single Identity Provider (IdP) to manage user credentials instead of each Service Provider (SP) storing them individually. This not only boosts security by reducing the attack surface but also streamlines the user experience by enabling Single Sign-On (SSO), where users log in once to access multiple applications.
Background: Organizations with strict security and operational requirements for production will typically use Vault Enterprise or the managed HashiCorp Cloud Platform (HCP). Vault Enterprise is a paid product for large organizations with advanced capabilities such as disaster recovery (DR), cross-datacenter replication, Sentinel policy enforcement, and namespaces for better tenant isolation and governance. Enterprise also provides dedicated support and features for complex, mission-critical environments with stringent compliance needs.
The community version effectively handles fundamental secrets management in CI/CD, but it lacks the advanced features that larger enterprises need for scalability, compliance, and reliability.
Vault Community Edition is a free, self-managed secret management tool offering core features for small-scale deployments.
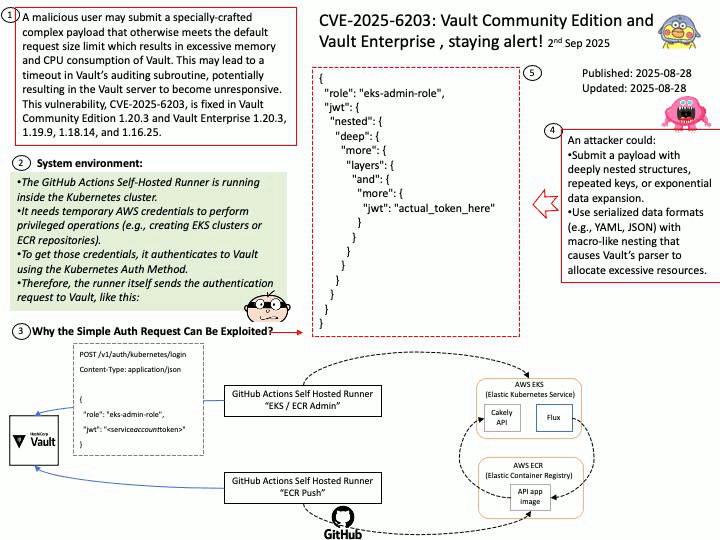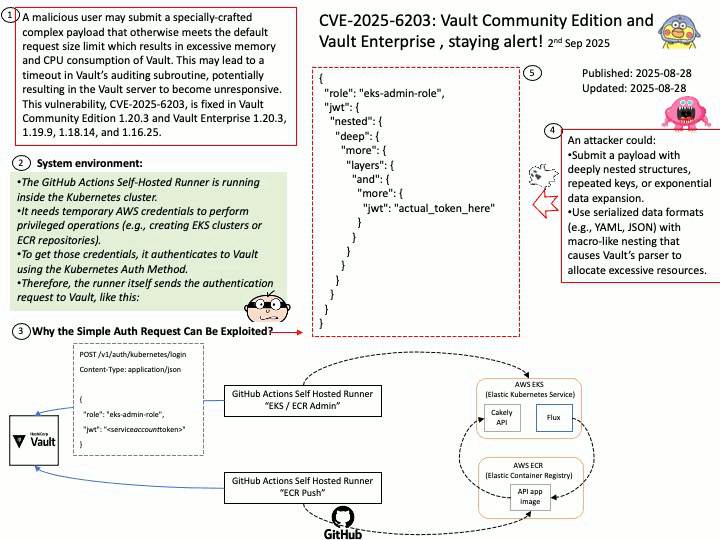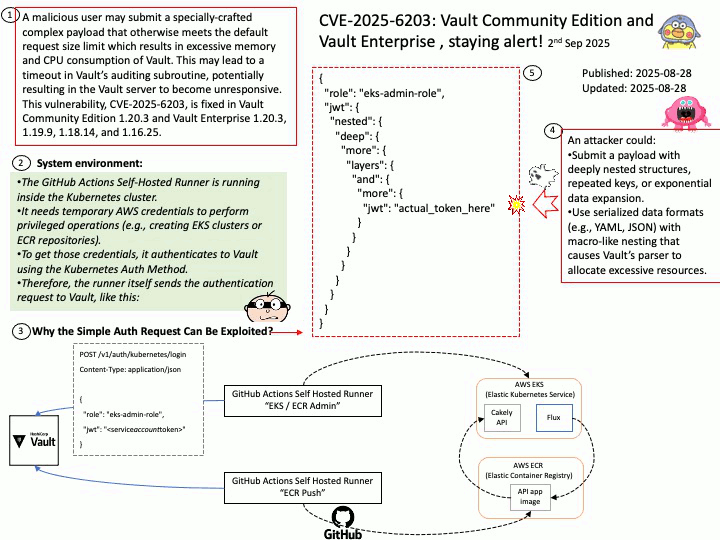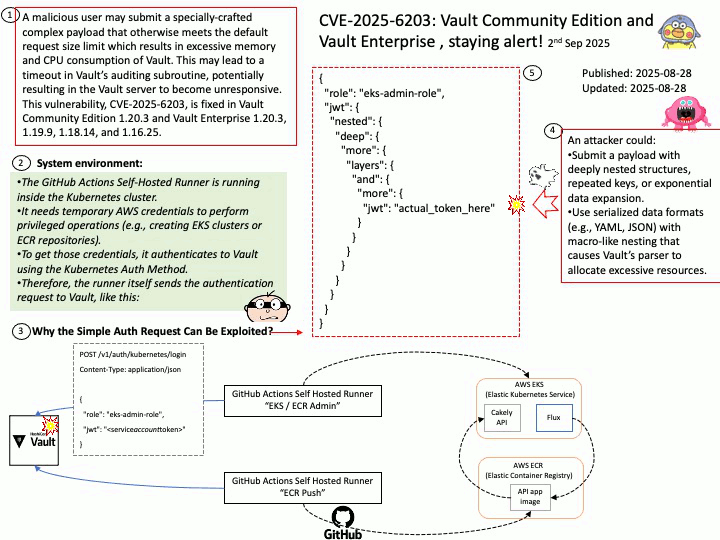
Vulnerability details: A malicious user may submit a specially-crafted complex payload that otherwise meets the default request size limit which results in excessive memory and CPU consumption of Vault. This may lead to a timeout in Vault’s auditing subroutine, potentially resulting in the Vault server to become unresponsive. This vulnerability, CVE-2025-6203, is fixed in Vault Community Edition 1.20.3 and Vault Enterprise 1.20.3, 1.19.9, 1.18.14, and 1.16.25.
Official announcement: Please refer to the link for more details –