Preface: Apple releases new iOS 15.7.9 and 16.6.1update for iPhone. iOS 15.7.9 and 16.6.1 like many of its predecessors, is a point upgrade and it patches up a security issue. But it doesn’t provides bug fixes technical details!
Background: The Core Graphics framework is based on the Quartz advanced drawing engine. It provides low-level, lightweight 2D rendering with unmatched output fidelity. You use this framework to handle path-based drawing, transformations, color management, offscreen rendering, patterns, gradients and shadings, image data management, image creation, and image masking, as well as PDF document creation, display, and parsing.
In macOS, Core Graphics also includes services for working with display hardware, low-level user input events, and the windowing system.
Vulnerability details: A buffer overflow issue was addressed with improved memory handling. This issue is fixed in macOS Monterey 12.6.9, macOS Big Sur 11.7.10, macOS Ventura 13.5.2, iOS 16.6.1 and iPadOS 16.6.1, iOS 15.7.9 and iPadOS 15.7.9. Processing a maliciously crafted image may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.
My speculation about this vulnerability: I observe that design weakness might happens when Quartz handle the CGdata. What is Quartz? The Core Graphics framework is based on the Quartz advanced drawing engine. Quartz handle path-based drawing, antialiased rendering, gradients, images, color management, PDF documents, and more.
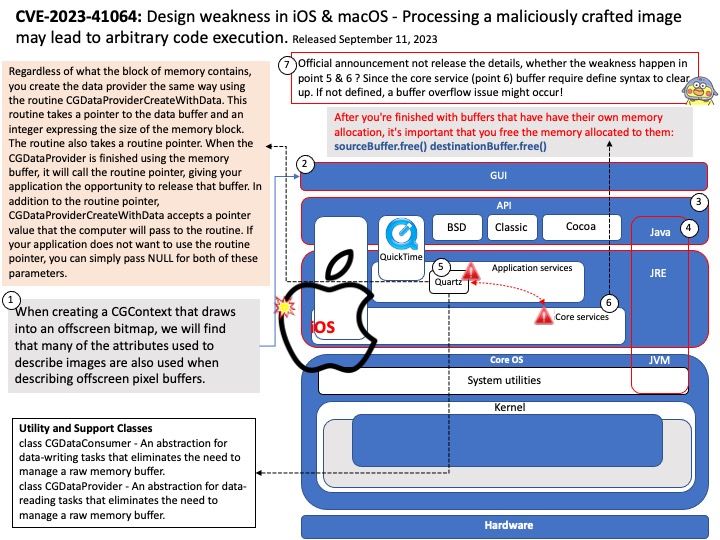
When the CGDataProvider is finished using the memory buffer, it will call the routine pointer, giving your application the opportunity to release that buffer. In addition to the routine pointer, CGDataProviderCreateWithData accepts a pointer value that the computer will pass to the routine. If your application does not want to use the routine pointer, you can simply pass NULL for both of these parameters.
However, core services itself have the following guideline. after you’re finished with buffers that have have their own memory allocation, it’s important that you free the memory allocated to them:
sourceBuffer[.]free() destinationBuffer[.]free()
So, whether the weakness happen in this function. Refer to point 5 and 6 in attached diagram? Since the core service (point 6) buffer require define syntax to clear up. If not defined, a buffer overflow issue might occur!
Ref: There are a number of services in the operating system that can return CGImages to your application. The most obvious source is Core Graphics, which offers a number of routines for creating CGImages from various data sources. However, in addition to Quartz, you can obtain CGImages from other operating system services. For example, QuickTime provides the routine GraphicsImportCreateCGImage, which can create a CGImage from a QuickTime Graphics importer.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-41064