Preface: In simplest terms, policies define what end-users can do on the cluster and possible ways to ensure that clusters are in compliance with organization policies.Policy-enablement empowers organizations to take control of Kubernetes operation and ensure that clusters are in compliance with organization policies.
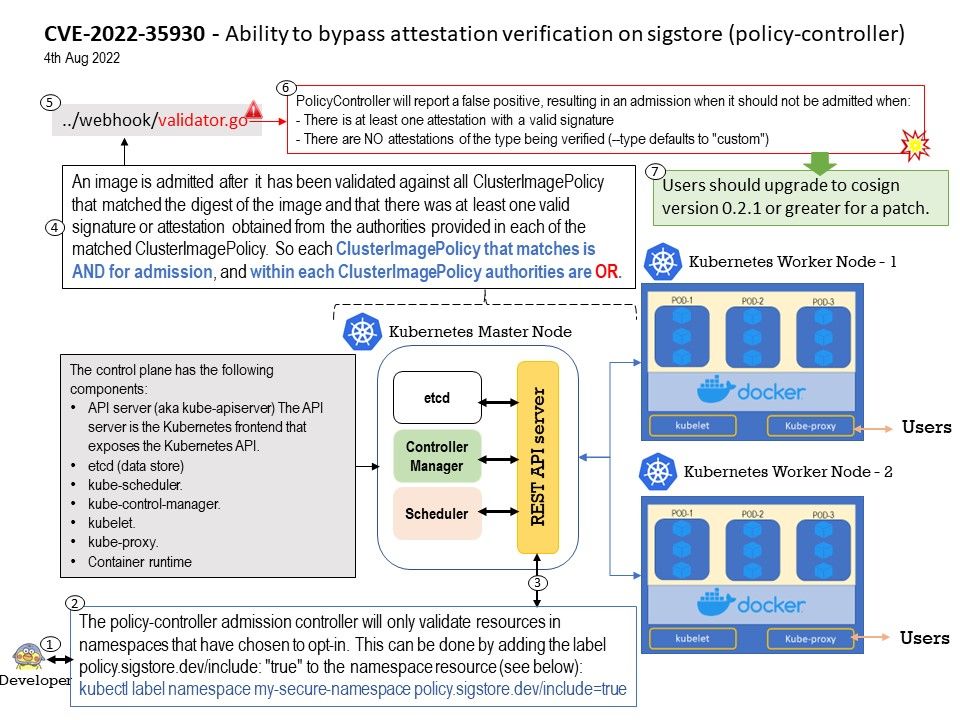
Background: The policy-controller admission controller will only validate resources in namespaces that have chosen to opt-in. This can be done by adding the label policy.sigstore.dev/include: “true” to the namespace resource (see below):
kubectl label namespace my-secure-namespace policy.sigstore.dev/include=true
Ref: An image is admitted after it has been validated against all ClusterImagePolicy that matched the digest of the image and that there was at least one valid signature or attestation obtained from the authorities provided in each of the matched ClusterImagePolicy. So each ClusterImagePolicy that matches is AND for admission, and within each ClusterImagePolicy authorities are OR.
Vulnerability details: PolicyController is a utility used to enforce supply chain policy in Kubernetes clusters. In versions prior to 0.2.1 PolicyController will report a false positive, resulting in an admission when it should not be admitted when there is at least one attestation with a valid signature and there are NO attestations of the type being verified (–type defaults to “custom”). An example image that can be used to test this is ghcr.io/distroless/static@sha256:dd7614b5a12bc4d617b223c588b4e0c833402b8f4991fb5702ea83afad1986e2.
Solution: Users should upgrade to version 0.2.1 to resolve this issue.
Workarounds: There are no workarounds for users unable to upgrade.