Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
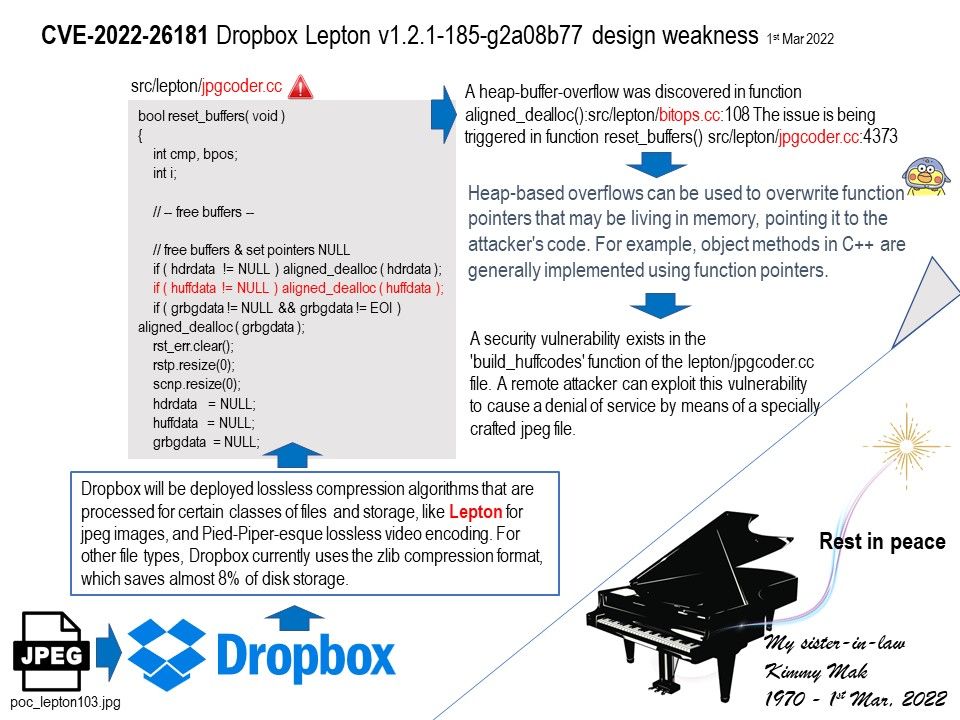
Background: Dropbox will be deployed lossless compression algorithms that are processed for certain classes of files and storage, like Lepton for jpeg images, and Pied-Piper-esque lossless video encoding. For other file types, Dropbox currently uses the zlib compression format, which saves almost 8% of disk storage.
Lepton is a tool and file format for actively compressing JPEGs. First developed by Daniel Horn at a Dropbox Hack Week, this streaming image compression format achieves a 22% savings reduction for existing JPEG images, while preserving the original file bit-for-bit perfectly.
Vulnerability details: A security vulnerability exists in the ‘build_huffcodes’ function of the lepton/jpgcoder[.]cc file. A remote attacker can exploit this vulnerability to cause a denial of service by means of a specially crafted jpeg file.
Reference: Buffer overflows often can be used to execute arbitrary code, which is usually outside the scope of a program’s implicit security policy. Besides important user data, heap-based overflows can be used to overwrite function pointers that may be living in memory, pointing it to the attacker’s code. Even in applications that do not explicitly use function pointers, the run-time will usually leave many in memory. For example, object methods in C++ are generally implemented using function pointers. Even in C programs, there is often a global offset table used by the underlying runtime.
Official announcement: For details , please refer to the link – https://drive.google.com/file/d/1bJlHozO37c5NZ1wI0NBWh0yHHyTcfaQL/view?usp=sharing