Preface: Perhaps the risk of this vulnerability is not high. However, if attackers exploit specific design weaknesses. It’s hard to say if Lamda can’t direct the attack to the backend service cloud.
Background: Alexa is able to play music, provide information, deliver news and sports scores, tell you the weather, control your smart home and even allow Prime members to order products from Amazon.
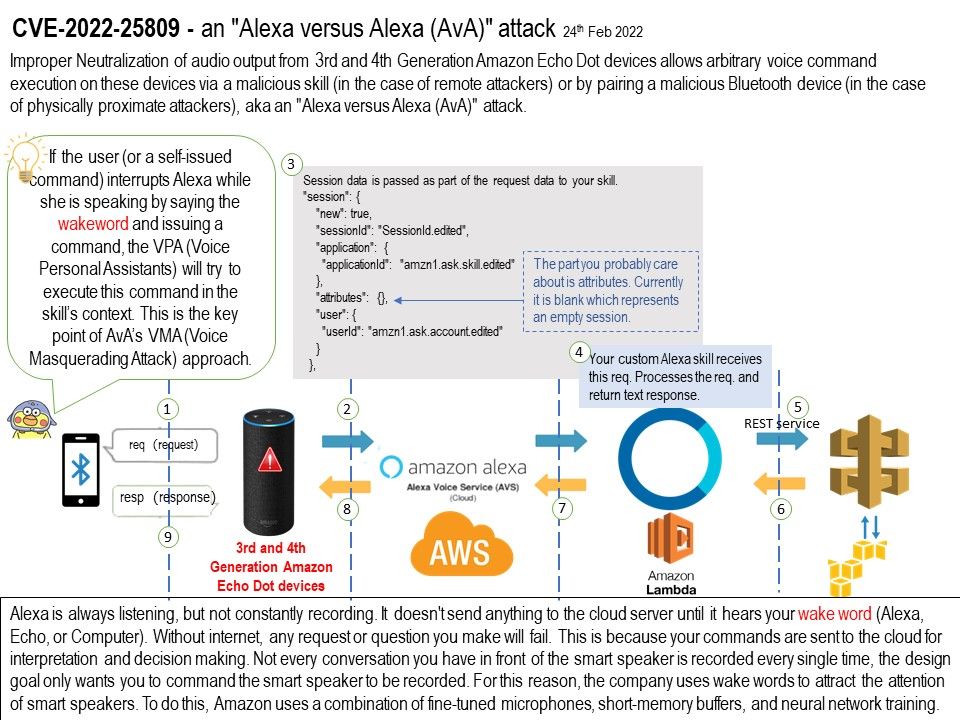
Alexa is always listening, but not constantly recording. It doesn’t send anything to the cloud server until it hears your wake word (Alexa, Echo, or Computer). Without internet, any request or question you make will fail. This is because your commands are sent to the cloud for interpretation and decision making. Not every conversation you have in front of the smart speaker is recorded every single time, the design goal only wants you to command the smart speaker to be recorded. For this reason, the company uses wake words to attract the attention of smart speakers. To do this, Amazon uses a combination of fine-tuned microphones, short-memory buffers, and neural network training.
Vulnerability details: Improper Neutralization of audio output from 3rd and 4th Generation Amazon Echo Dot devices allows arbitrary voice command execution on these devices via a malicious skill (in the case of remote attackers) or by pairing a malicious Bluetooth device (in the case of physically proximate attackers), aka an “Alexa versus Alexa (AvA)” attack.
Ref: What is Alexa in Python? What is Alexa command in the skill’s context?
The Alexa Skills Kit SDK for Python simplifies the development of the back-end cloud service for your Alexa skill. A part of the Alexa Skills Kit, the SDK reduces the amount of code you need to write to process Alexa requests and responses and to handle other common skill tasks.
You can built few basic Alexa skills, the goal of these skills related to predefined questions. These predefined skills will do information mapping to find the right answer.
For more details, please refer to the link – https://arxiv.org/abs/2202.08619