Preface: Amazon now “owns” FreeRTOS, in the sense that the company will provide all support going forward. FreeRTOS includes a kernel and a growing set of software libraries suitable for use across industry sectors and applications. To support a growing number of use cases, AWS provides software libraries that offer enhanced functionality including connectivity, security, and over-the-air updates.
Background: FreeRTOS is customised using a configuration file called FreeRTOSConfig.h. Every FreeRTOS application must have a FreeRTOSConfig.h header file in its pre-processor include path. FreeRTOSConfig.h tailors the RTOS kernel to the application being built. It is therefore specific to the application, not the RTOS, and should be located in an application directory, not in one of the RTOS kernel source code directories.
Reference:
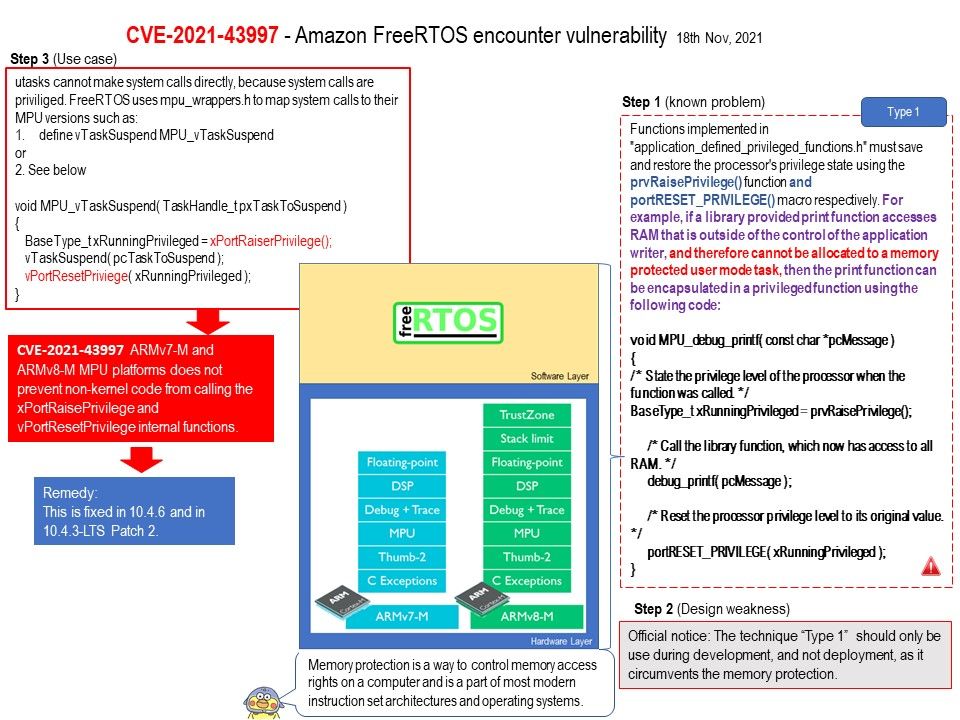
Functions implemented in “application_defined_privileged_functions.h” must save and restore the processor’s privilege state using the prvRaisePrivilege() function and portRESET_PRIVILEGE() macro respectively. For example, if a library provided print function accesses RAM that is outside of the control of the application writer, and therefore cannot be allocated to a memory protected user mode task, then the print function can be encapsulated in a privileged function.
Official reminder: Above technique should only be use during development, and not deployment, as it circumvents the memory protection.
Vulnerability details: Amazon FreeRTOS 10.2.0 through 10.4.5 on the ARMv7-M and ARMv8-M MPU platforms does not prevent non-kernel code from calling the xPortRaisePrivilege and vPortResetPrivilege internal functions.
Remedy: This is fixed in 10.4.6 and in 10.4.3-LTS Patch 2.
Official announcement: https://github.com/FreeRTOS/FreeRTOS-Kernel/releases/tag/V10.4.6