Preface: Cloud computing build civilization chain. The strongest of AI, Smart City technology will be according to the foundation of cloud.
Technical background: Google Container Registry (GCR) is a service in Google Cloud Platform (GCP) to manage your own docker container repository. This is fully managed service and you can store your custom container images as well as common images from other image repositories.
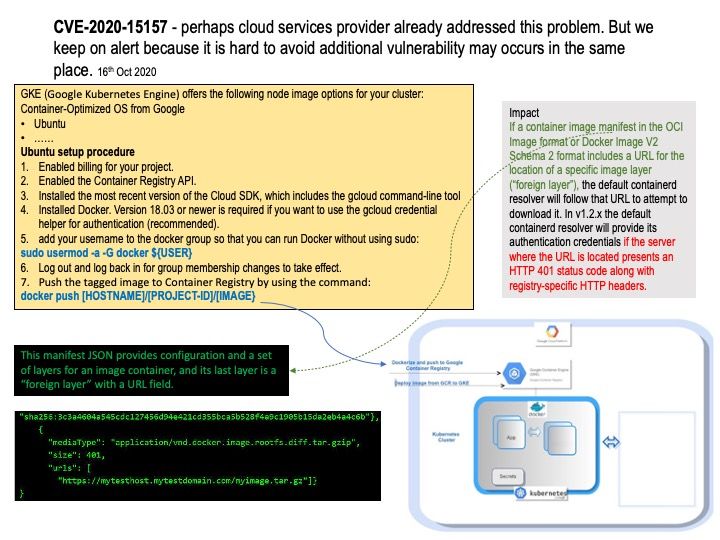
Vulnerability details: If a container image manifest in the OCI Image format or Docker Image V2 Schema 2 format includes a URL for the location of a specific image layer (foreign layer), the default containerd resolver will follow that URL to attempt to download it. In v1.2.x, the default containerd resolver will provide its authentication credentials if the server where the URL is located presents an HTTP 401 status code along with registry-specific HTTP headers.
Highlights: The manifest supports an optional field for an external URL from which content may be fetched, and it can be any registry or domain.
Remedy: This vulnerability has been fixed in containerd 1.2.14. containerd 1.3 and later are not affected.
Workaround: Ensure that only pull images from trusted sources. Other container runtimes built on top of containerd but not using the default resolver (such as Docker) are not affected.