Foreword: A vulnerability published a few months ago (CVE-2022-22071) intrigued me due to a design flaw in snapdargon’s memory management. Therefore written down my gather information on the subject.
CVE-2022-22071 – Possible use after free when process shell memory is freed using IOCTL munmap call and process initialization is in progress in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music. Perhaps there is no proof of concept how to exploit this flaw. As an Android lover, it allowed me to learn and gain understanding.
Background: In Snapdragon SoCs, three components are used to provide access control: Virtual Master ID Mapping Table (VMIDMT), External Protection Unit (XPU), and System Memory Management Unit (SMMU). The SMMU is a hardware component that performs address translation and access control for bus initiators outside of the CPU. An SMMU can perform two stages of address translation.
- usually controlled by the CPU OS, maps the virtual addresses visible to applications and the OS kernel to intermediate physical addresses visible to a virtual machine.
- maps intermediate physical addresses to physical addresses.
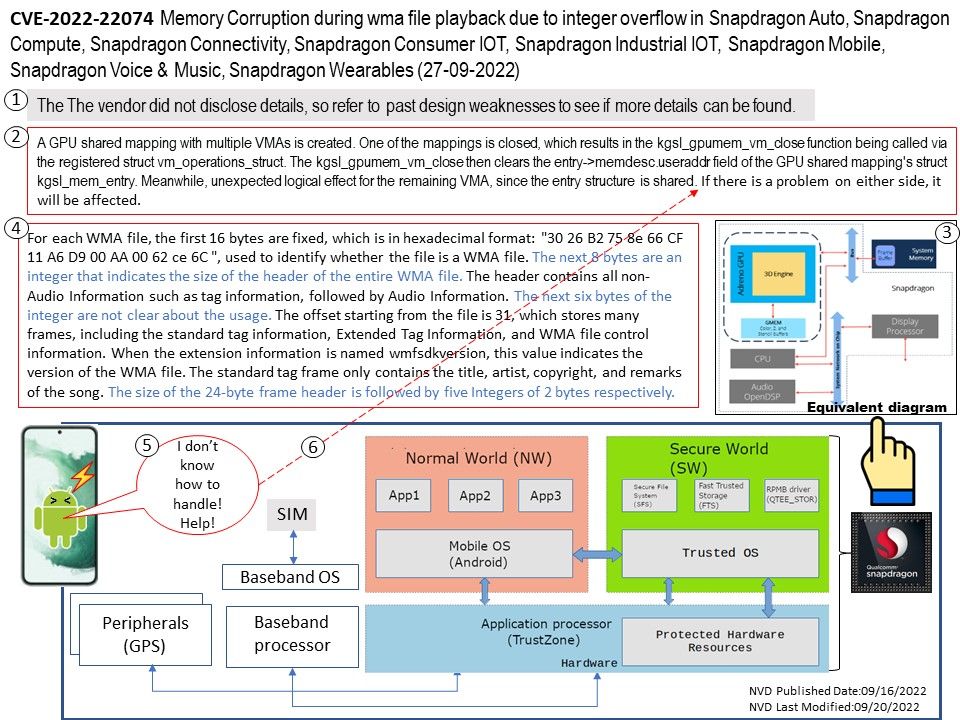
Vulnerability details: Memory Corruption during wma file playback due to integer overflow in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables.
See the diagram for details on my research on such vulnerabilities.
Official announcement: See the link for details – https://www.qualcomm.com/company/product-security/bulletins/september-2022-bulletin