Preface: public class CGIServlet – extends javax.servlet.http.HttpServlet
(CGI-invoking servlet for web applications, used to execute scripts which comply to the Common Gateway Interface (CGI) specification.)
Synopsis: Tomcat implements several Java EE specifications including Java Servlet, JavaServer Pages (JSP), Java EL, and WebSocket, and provides a “pure Java” HTTP web server environment in which Java code can run.
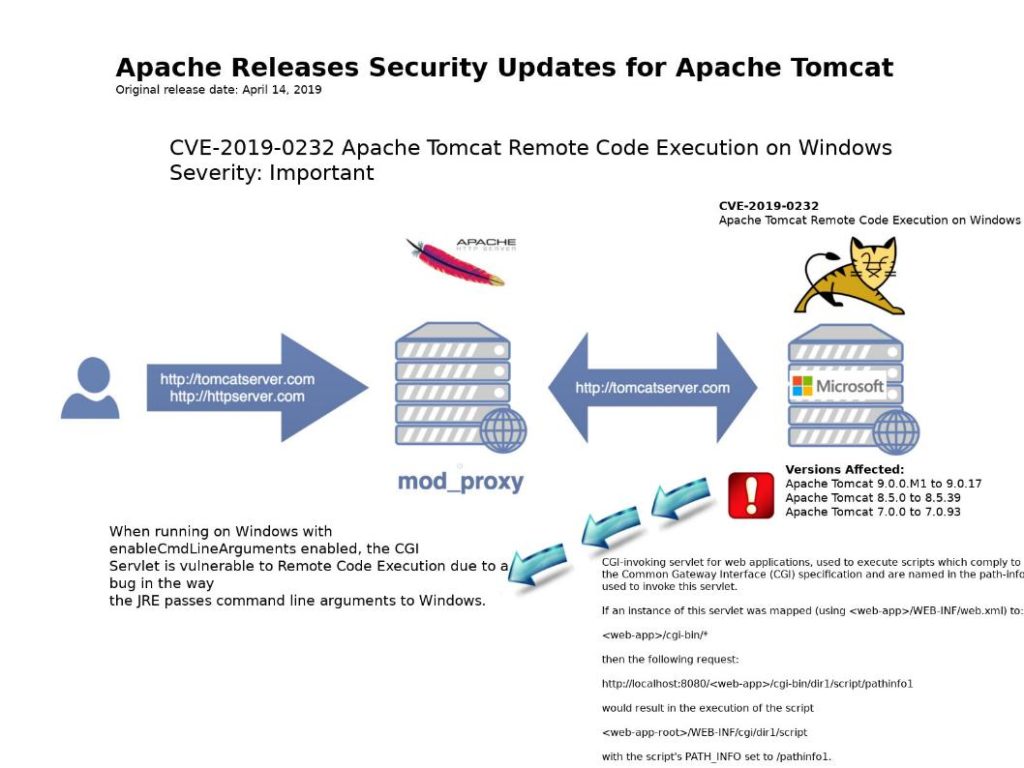
Vulnerability details: CVE-2019-0232 Apache Tomcat Remote Code Execution on Windows
Apache Tomcat version for Windows. A design defect in function (enableCmdLineArguments), the CGI Servlet is vulnerable to Remote Code Execution due to a bug in the way the JRE passes command line arguments to Windows. But this CGI Servlet is disabled by default.
Remark: enableCmdLineArguments – Are command line parameters generated from the query string as per section 4.4 of 3875 RFC? The default is false.
Official announcement shown following url: http://mail-archives.us.apache.org/mod_mbox/www-announce/201904.mbox/%3C13d878ec-5d49-c348-48d4-25a6c81b9605%40apache.org%3E