Preface: Is this a possible solution? Can we disabled SMT technology as mitigating SQUIP? As far as we know, it will severely degrade the performance of AMD processors.
Background: Attacker modifies system MTR registers to change the SMM memory space from uncacheable to cacheable with type Write-back. The MTRR (Memory Type Range Registers), are registers that provide the system software with control of how accesses to memory ranges by the CPU are cached.
The attacker now can write code into the memory space that is normally reserved only for SMM functions. The CPU will execute the SMM code but it will fetch it from the cache before DRAM. If the malicious code is in cache so it is executed.
Remark: SMM code is the most privileged code executed on the CPU, the code is completely hidden from the running operating system, it cannot be modified by the kernel and even by DMA devices and the most important SMM code can access any physical memory.
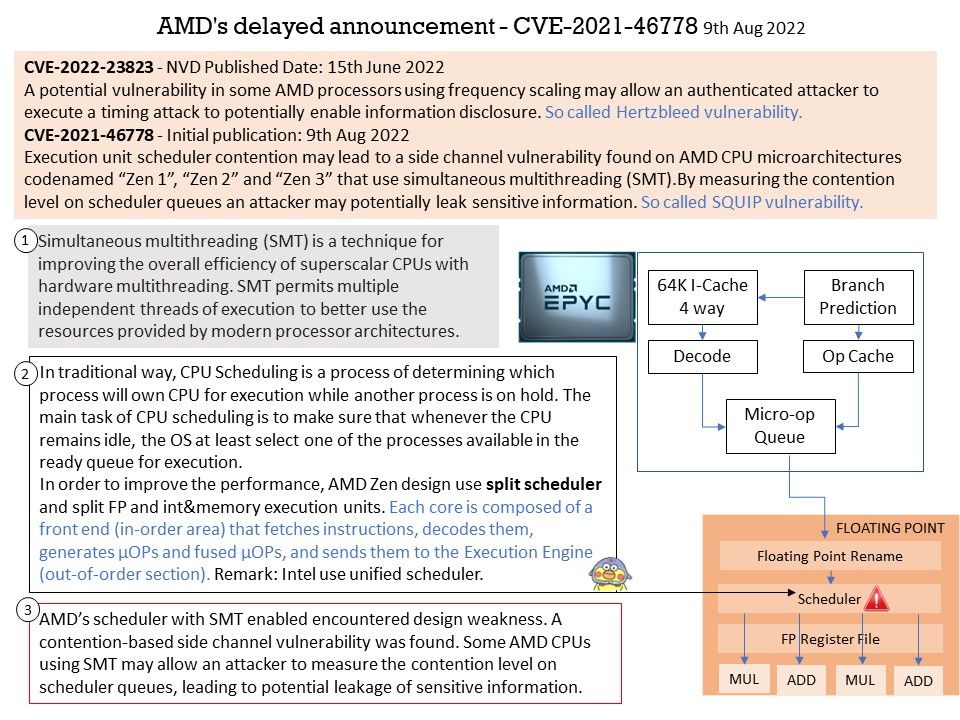
Vulnerability details: A contention-based side channel vulnerability was found in hw. Some AMD CPUs using simultaneous multithreading (SMT) may allow an attacker to measure the contention level on scheduler queues, leading to potential leakage of sensitive information.
To exploit the design weakness and get access to data processed by the same CPU core, attacker need to run malicious code on that CPU core first. Is it possible to take advantage of SMM?
Official announcement – Execution Unit Scheduler Contention Side-Channel Vulnerability on AMD Processors. Please refer to the link for details – https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1039