Preface: PCMCIA Cards have been around for many years and can still be found in today’s technology. These cards are now classed as legacy products, as they were first introduced over 25 years ago.
PCMCIA cards come in 3 different types of memory; ATA, SRAM and Linear. The cards are still being made today to help support legacy products and applications, mainly aerospace, defence and transportation.
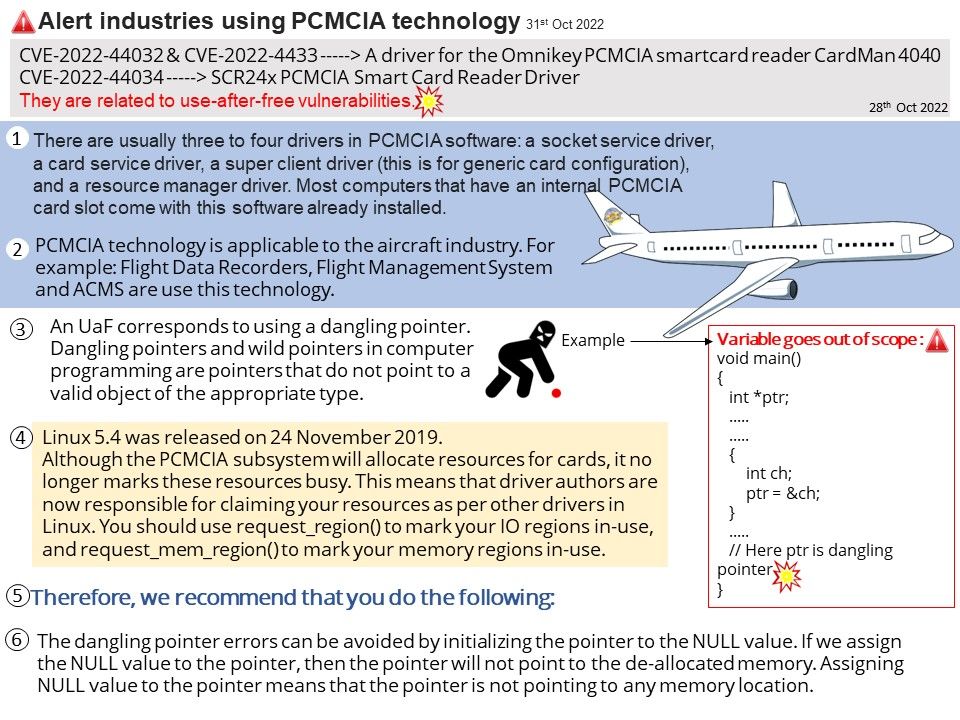
Background: Linux 5.4 was released on 24 November 2019. Although the PCMCIA subsystem will allocate resources for cards, it no longer marks these resources busy. This means that driver authors are now responsible for claiming your resources as per other drivers in Linux. You should use request_region() to mark your IO regions in-use, and request_mem_region() to mark your memory regions in-use.
PCMCIA design weakness recently (28th Oct 2022):
CVE-2022-44032 —–> A driver for the Omnikey PCMCIA smartcard reader CardMan 4040
An issue was discovered in the Linux kernel through 6.0.6. drivers/char/pcmcia/cm4000_cs[.]c has a race condition and resultant use-after-free if a physically proximate attacker removes a PCMCIA device while calling open(), aka a race condition between cmm_open() and cm4000_detach(). Please refer to the link for details – https://lore.kernel.org/lkml/20220915020834.GA110086@ubuntu/
CVE-2022-44033 —–> A driver for the Omnikey PCMCIA smartcard reader CardMan 4040
An issue was discovered in the Linux kernel through 6.0.6. drivers/char/pcmcia/cm4040_cs[.]c has a race condition and resultant use-after-free if a physically proximate attacker removes a PCMCIA device while calling open(), aka a race condition between cm4040_open() and reader_detach().Please refer to the link for details –
https://lore.kernel.org/lkml/20220915020834.GA110086@ubuntu/
CVE-2022-44034 —–> SCR24x PCMCIA Smart Card Reader Driver
An issue was discovered in the Linux kernel through 6.0.6. drivers/char/pcmcia/scr24x_cs[.]c has a race condition and resultant use-after-free if a physically proximate attacker removes a PCMCIA device while calling open(), aka a race condition between scr24x_open() and scr24x_remove(). Please refer to the link for details –
https://lore.kernel.org/lkml/20220919101825.GA313940@ubuntu/
Remedy:
In order to avoid vulnerabilities, we recommend the following:
The dangling pointer errors can be avoided by initializing the pointer to the NULL value. If we assign the NULL value to the pointer, then the pointer will not point to the de-allocated memory. Assigning NULL value to the pointer means that the pointer is not pointing to any memory location.