Preface: Times have changed, and people’s concerns about data security are compared with the past three decades. it looks important. The basis of the design goals of the http protocol in the 90s was to focus on network connections. Because the computing technology at that time was very simple. It does not have the concepts of virtual machines and cloud computing. As of now, man-in-the-middle attacks are easily triggered by network analysis tools, especially wireshark and open source application penetration testing tools. So the http protocol looks even less secure. Maybe you say, I work on the intranet. Or the data fo through network do not have confidential data. However, for modern technology of virtual machine and container architecture, it will be also influenced by http protocol.
Background: OpenShift Container Platform is a cloud-based Kubernetes container platform. The foundation of OpenShift Container Platform is based on Kubernetes and therefore shares the same technology.
For system management and developments. Developers and admins can through the control plane manages the worker nodes and the pods in your cluster. You can configure nodes with the use of machine config pools (MCPs). MCPs are groups of machines, such as control plane components or user workloads. In normal circumstances, it is hard to avoid the network connectivities consists of insecure practice of redirecting users from http:// to https:// URLs.
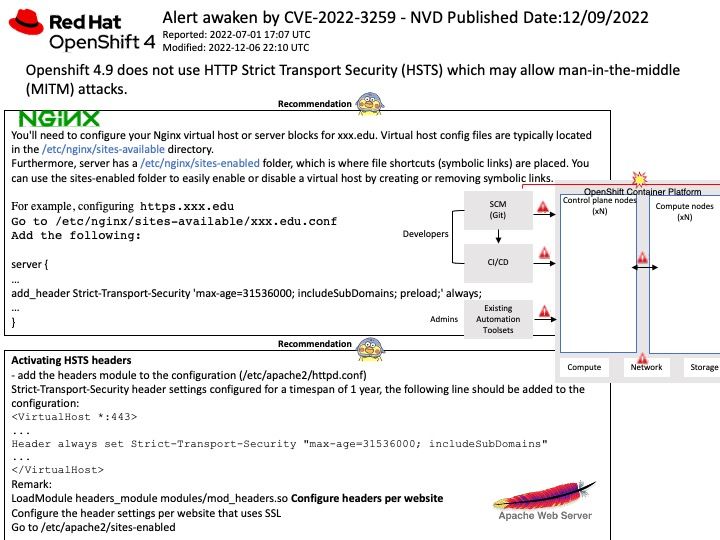
HTTP Strict Transport Security (HSTS) is a simple and widely supported standard to protect visitors by ensuring that their browsers always connect to a website over HTTPS. HSTS exists to remove the need for the common, insecure practice of redirecting users from http:// to https:// URLs.
The following are common scenarios where a man-in-the-middle attack occurs.
- User bookmarks or manually types http://example.com and is subject to a man-in-the-middle attacker.
- Web application that is intended to be purely HTTPS inadvertently contains HTTP links or serves content over HTTP.
- A man-in-the-middle attacker attempts to intercept traffic from a victim user using an invalid certificate and hopes the user will accept the bad certificate.
Vulnerability details: Openshift 4.9 does not use HTTP Strict Transport Security (HSTS) which may allow man-in-the-middle (MITM) attacks.
Official announcement: Please refer to the link for details : https://nvd.nist.gov/vuln/detail/CVE-2022-3259